Microsoft revealed on Tuesday that a large-scale phishing campaign targeted more than 10,000 organizations since September 2021 by attacking the Office 365 authentication process even on accounts secured with multi-factor authentication (MFA).
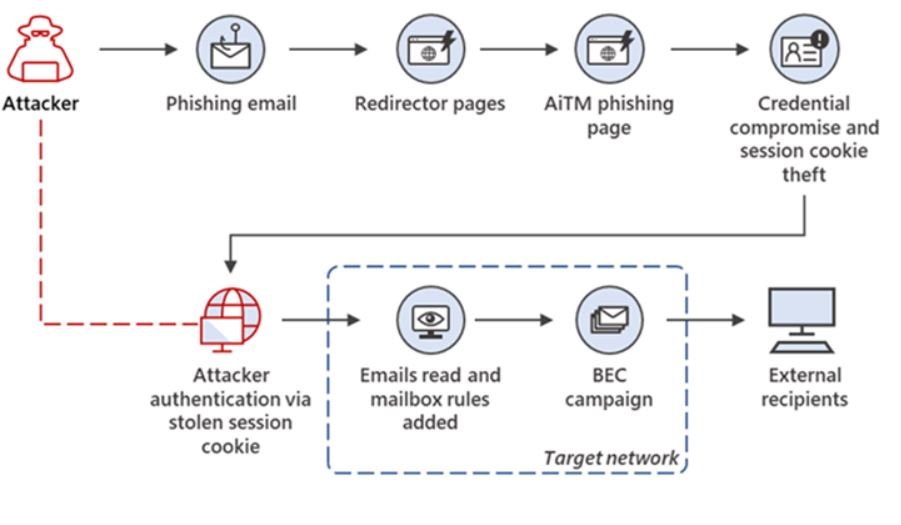
The attackers then used the stolen credentials and session cookies to access the affected users’ mailboxes and carry out e-mail “spoofing” campaigns on their targets.
The intrusions involved the creation of adversary-in-the-middle(AitM) phishing sites, in which the attacker deploys a proxy server between a potential victim and the target website so that recipients of a phishing email are redirected to similar pages designed to capture credentials and MFA information.In AiTM phishing, an attacker attempts to obtain a target user’s session cookie so they can skip the whole authentication process and act on the latter’s behalf.
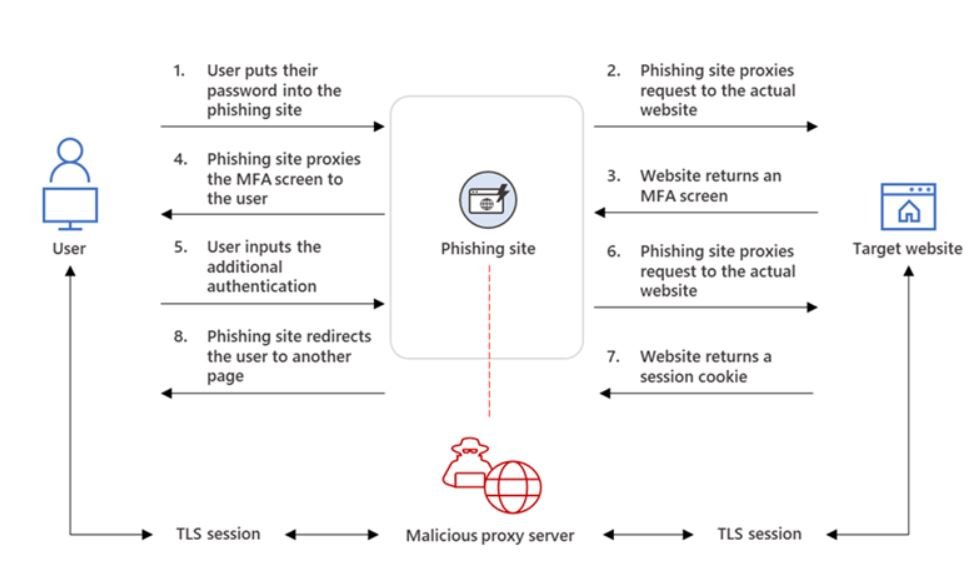
To do this, the attacker deploys a webserver that proxies HTTP packets from the user that visits the phishing site to the target server the attacker wishes to impersonate and the other way around. This way, the phishing site is visually identical to the original website (as every HTTP is proxied to and from the original website). The attacker also doesn’t need to craft their own phishing site like how it’s done in conventional phishing campaigns. The URL is the only visible difference between the phishing site and the actual one.
The phishing page has two different Transport Layer Security (TLS) sessions: one with the target and one with the actual website the target wants to access.
These sessions mean that the phishing page works almost like an AitM agent, intercepting the entire authentication process and extracting valuable data from HTTP requests, such as passwords and, more importantly, session cookies.
The phishing campaign detected by Microsoft was organized to identify Office 365 users by spoofing the Office online authentication page. The AiTM phishing process can currently be automated using open-source phishing toolkits and other online resources. Among the widely-used kits include Evilginx2, Modlishka, and Muraena. The actors used the Evilginx2 phishing kit to carry out the attacks.
The attacks did not end there, as the attackers abused their mailbox access for payment fraud using a technique called “email thread hijacking” to trick parties on the other end of the conversation into illicitly transferring funds to accounts under your control.
While AiTM phishing attempts to circumvent MFA, it’s important to underscore that MFA implementation remains an essential pillar in identity security. Defenders can also complement MFA with the following solutions and best practices to further protect their organizations from such types of attacks:
- Enable conditional access policies.
- Invest in advanced anti-phishing solutions
- Continuously monitor for suspicious or anomalous activities:

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











