Searching vulnerabilities on the host (the host can be a website, web server, network device (router and others), end-user computer) begins with the collection of basic information. This information includes host detection, scanning their ports to search for open, definition of running services at these ports, defining service versions and finding vulnerabilities for these versions, checking for the use of weak passwords, launching additional scans with various tools, depending on the detected network services.
This is usually a fairly typical set of actions that varies from running network services detected on the host. Therefore, there are already various automation tools that can scan the network range and, for example, start the bar-force of the services found.
We want to talk about another ethical hacking tool – this badKarma. This program has a graphical interface in which it is enough to click the mouse – it is not necessary to introduce commands (although they can be adjusted for fine tuning).
How to install badKarma
Installing badKarma is very simple. But the fact is that this is just a graphical shell for launching tools. That is, you need to install all the tools that the program uses. Therefore, I recommend working with badKarma in Kali Linux, in which (almost) everything you need is already present.
To install badKarma in Kali Linux, run the command :
sudo apt install python3-pip python3-gi phantomjs mitmproxy ffmpeg gir1.2-gtk-vnc-2.0 gir1.2-gtksource-3.0 gir1.2-vte-2.91 gir1.2-osmgpsmap-1.0 gir1.2-webkit2-4.0 knockpy ncat gobuster
git clone https://github.com/r3vn/badKarma.git
cd badKarma
sudo pip3 install -r requirements.txt
chmod +x badkarma.py
./badkarma.py
How to use badKarma
Start by entering the target. You can specify the site address, IP address or range of IP addresses :
You can also select a scan profile. The following options are available:
- nmap_default – normal scanning with help Nmap,
- nmap_intense_scan – intensive scanning with Nmap, the options -T4 -A -v -oX are used
- nmap_intense_scan_all_tcp – intensive scanning of all TCP ports with Nmap, options -p 1-65535 -T4 -A -v -oX are used
- nmap_intense_scan_no_ping – intensive scanning with Nmap without checking if the host is available (without ping), the options -T4 -A -v -Pn -oX are used
- masscan_full_tcp – full scan with help Masscan, options are used -p0-65535 –rate 10000 –banner
- get-from-shodan – do not scan, but get data from shodan. To do this, you must first specify your API key to shodan. In Kali Linux API, the key to shodan must be written in the ~ / filebin / badKarma / conf / shodan.conf. And in the BlackArch API, the key to shodan must be written in the file. /usr/share/badkarma/conf/shodan.conf
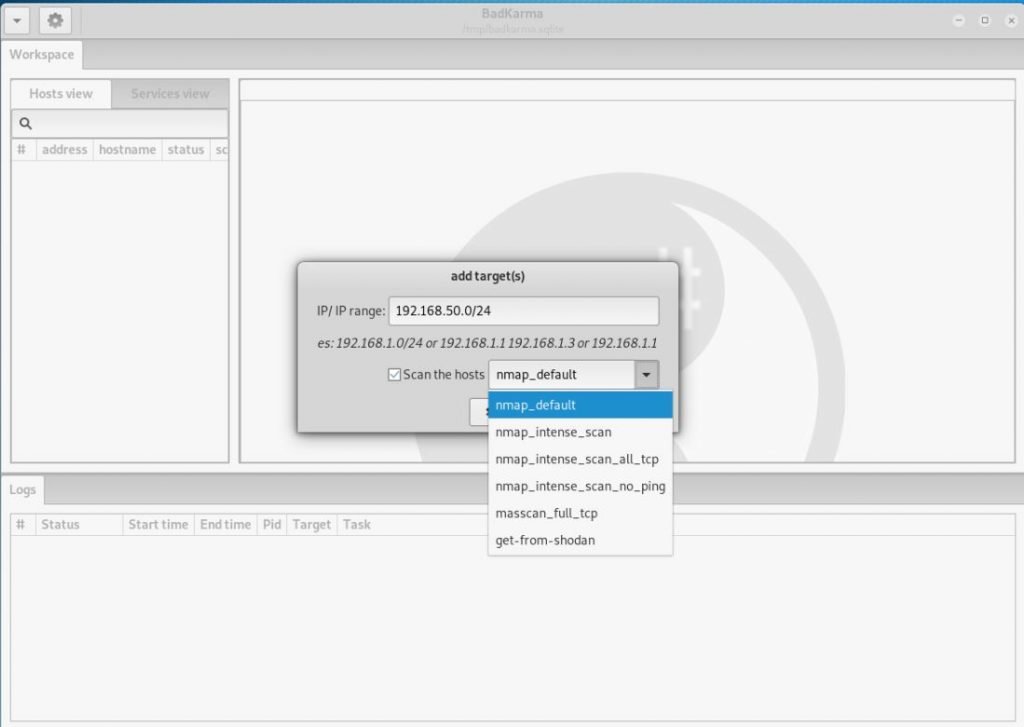
As a goal, I will add the local network through which I go online: 192.168.50.0 / 24
Scan results will be presented as a list of available hosts :
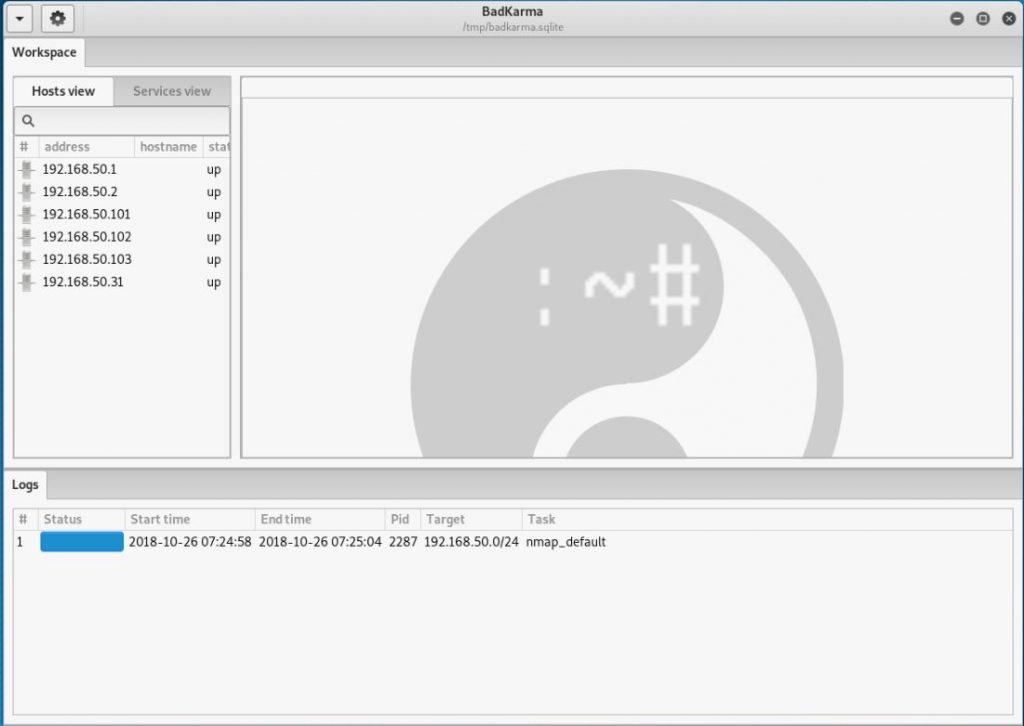
If you click on the host, open ports and running network services will be shown :
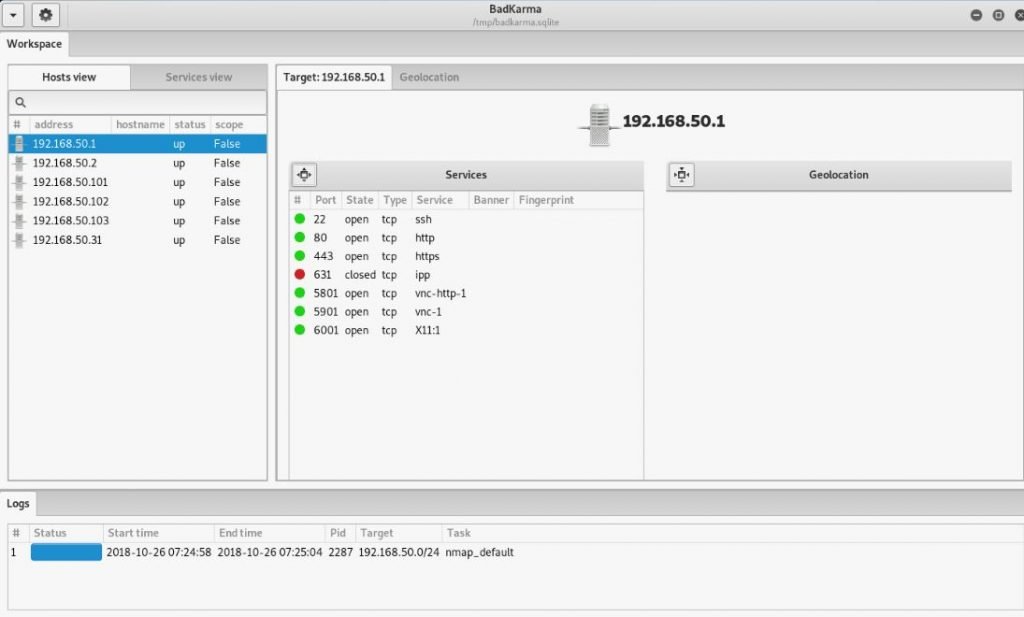
Under the list of running services is other additional information (if it is collected) about the operating system, location, MAC address and more :
Now we have two options: you can continue to explore the host as a whole, or focus on its individual services. To view the available options for working with the host, right-click on it :
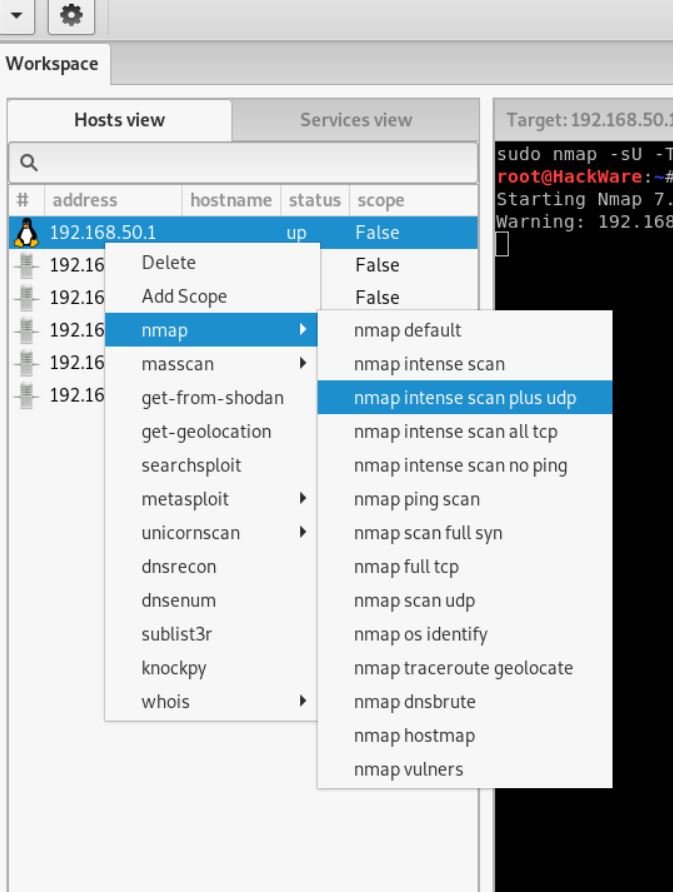
Various types of scanning using Nmap, various options for finding subdomains, DNS record research, and other ways to get information on the host are available there.
By right-clicking on the services launched on the host, you can see the actions available for them :
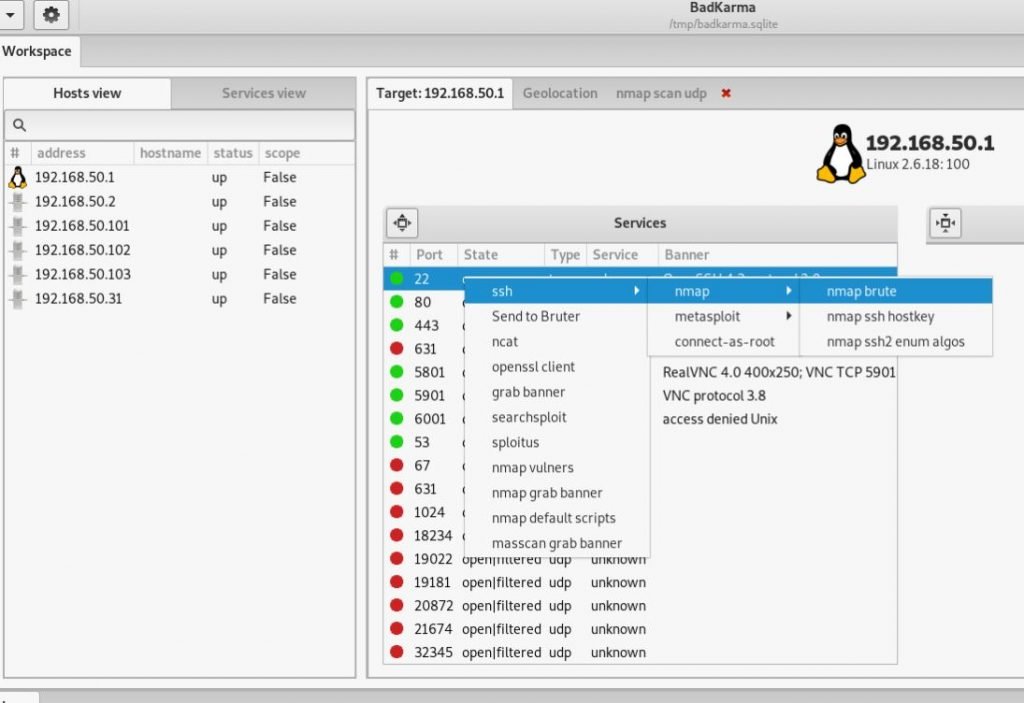
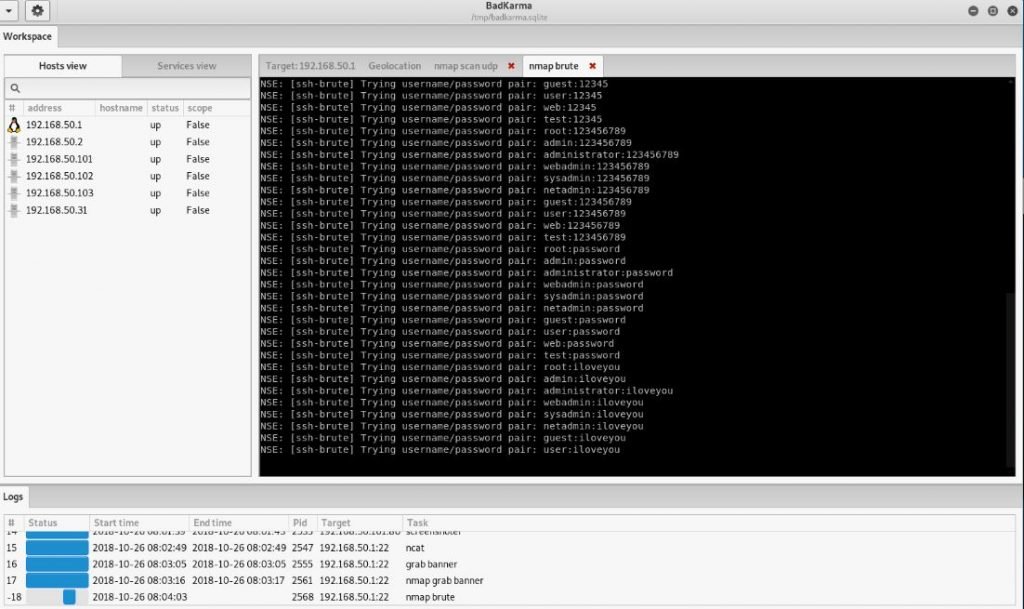
For example, for SSH you can run brut-force :
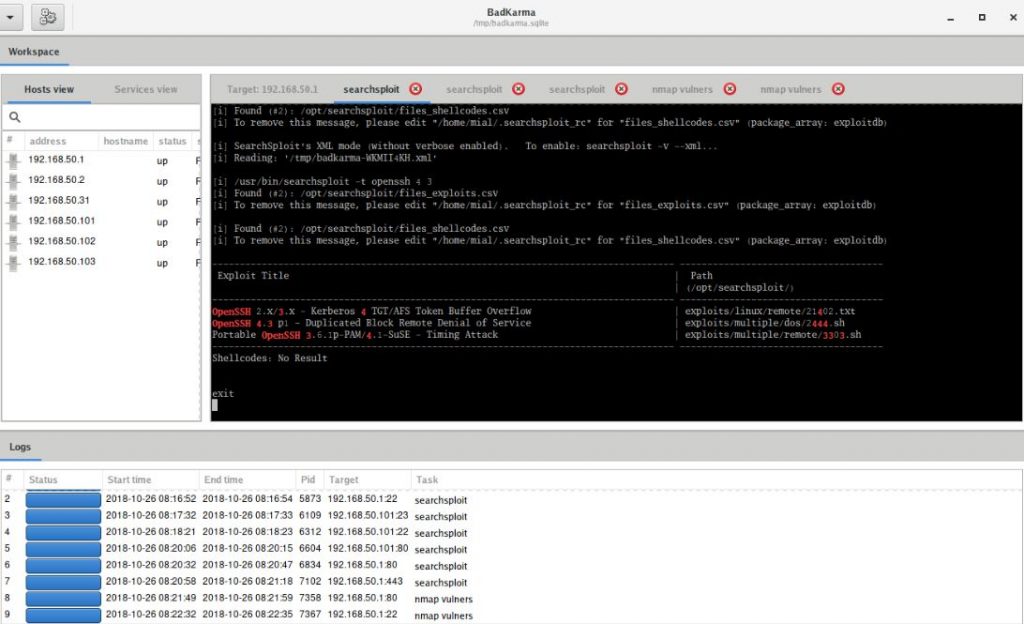
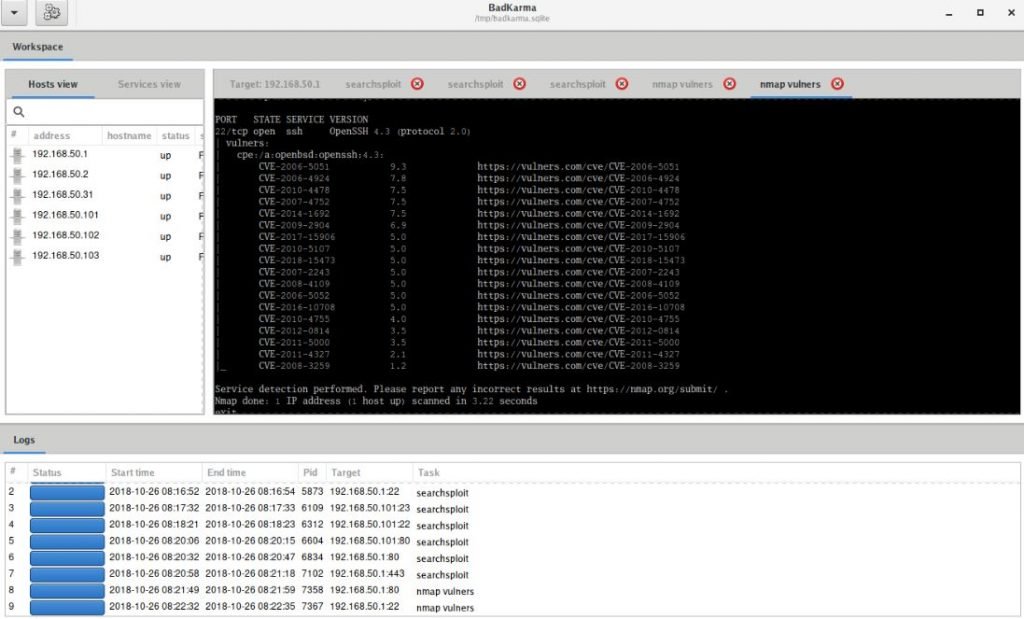
You can start searching for exploits using nmap, searchesploit or splitus:
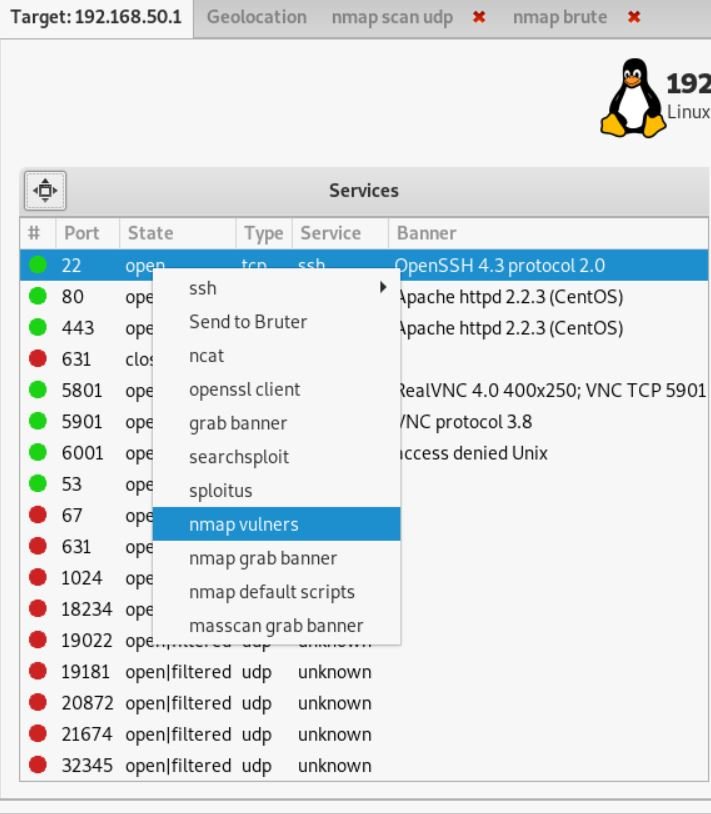
In this case, the exact version number of the service will be determined (if this has not been done previously) and exploits from popular databases will be searched for for it.
Especially many different options for web services :
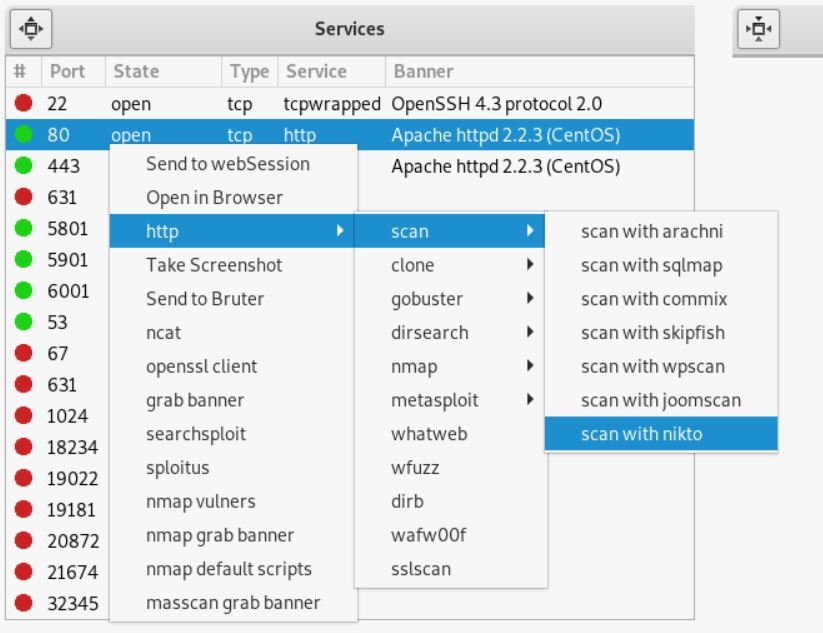
You can take a screenshot, clone a page, scan popular programs for finding vulnerabilities, start searching for users, hosts, directories, subdomains, and more
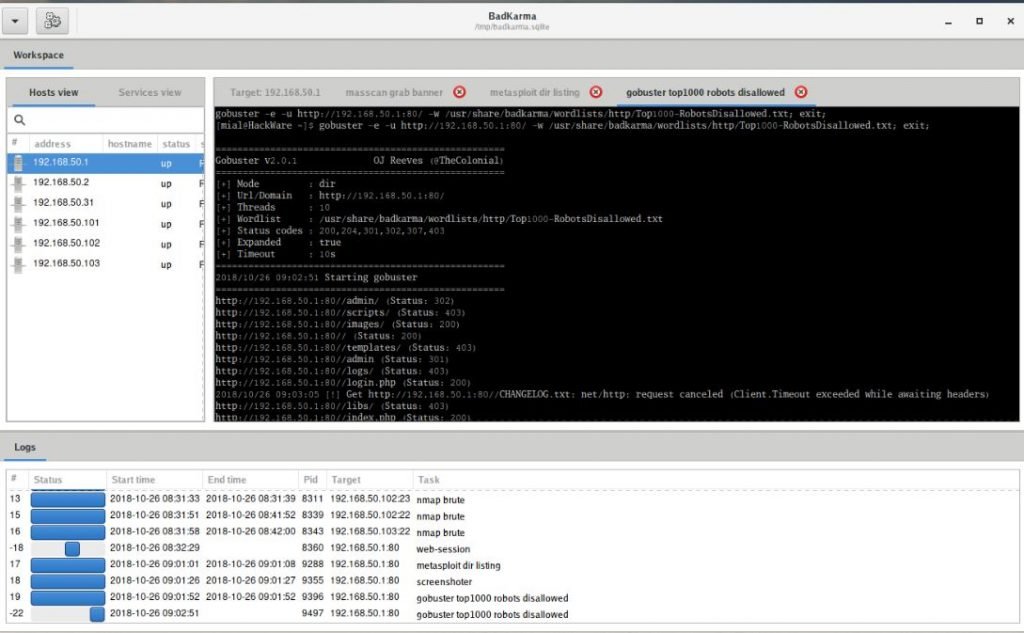
has WebSession (works with mitmproxy):
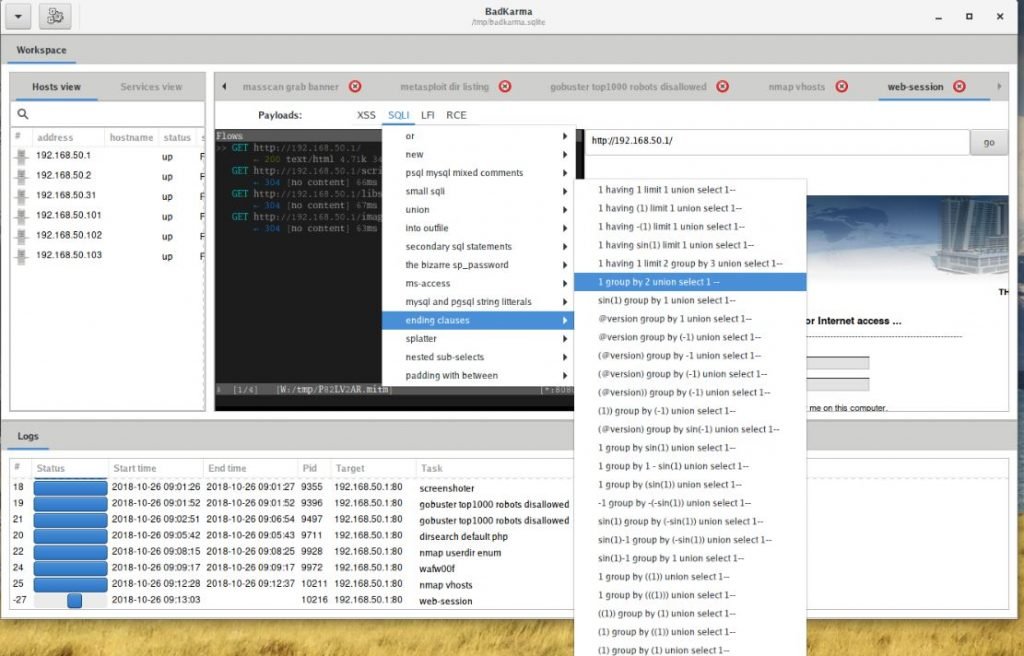
The data obtained during operation are not only displayed, but also stored in the session file /tmp/badkarma.sqlite. If you want to save this file, then after the completion of the work, be sure to copy it to a safe place, since the folder. / tmp automatically cleansed at each computer reboot.
Conclusion
badKarma in general, an interesting pentesting program with which you can quickly perform routine actions and keep the results in one place convenient for visual perception. As you can understand when working with the program, the set of operations for each service is selected intellectually, depending on the type of service. If this list lacks some of your favorite tools, then this is not a problem: badKarma is a modular program and you can add your own module.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











