Previously undetected malware called Lightning Framework that targets Linux systems can be used as a backdoor using SSH and deploy rootkits to cover the tracks of attackers.
Described as a “Swiss Army Knife” in a report published today by Intezer, the Lightning Framework is modular malware that also comes with plugin support. “This framework has passive and active capabilities for communication with the threat actor, including opening SSH into an infected machine. The Lightning Framework is built using a simple structure: a downloader component that will download and install the malware’s other modules and plugins, including its core module, on compromised Linux devices.
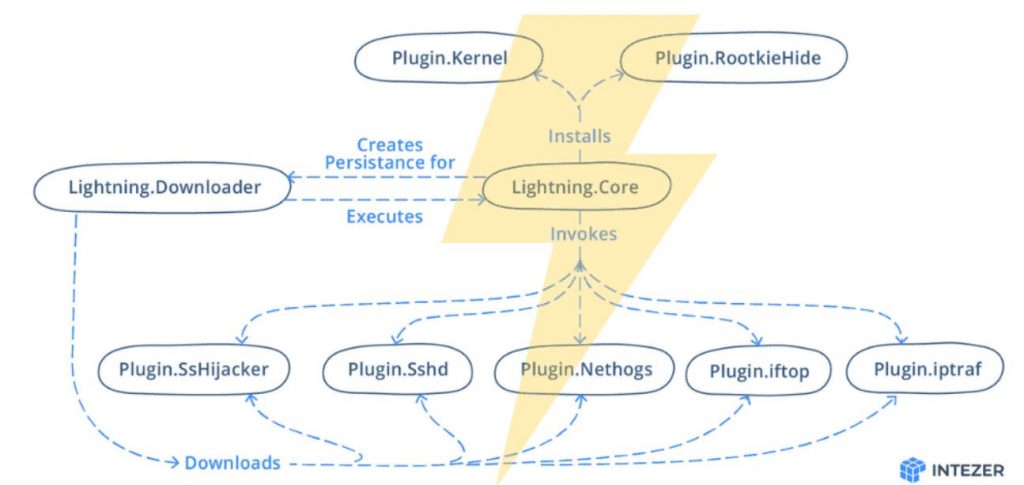
The malware uses a typosquatting encryption key to evade detection on infected systems. After communicating with command and control (C2) server over TCP sockets using C2 information stored in undetectable polymorphic encrypted configuration files, the Lightning Framework fetches other plugins and core modules. The core module (kkdmflush) is the main module of the framework and is what the malware uses to receive commands from its C2 server and run its plugins.
The module has many capabilities and uses a number of techniques to hide artifacts to remain running under the radar.
The core module modifies the name of the calling thread of the module to kdmflush, to make it appear that it is a kernel thread.
Other methods of hiding their presence include altering the timestamping of malicious artifacts by using timestamps, and hiding their process ID (PID) and any related network ports using one of several rootkits that it can implement.
It achieves persistence by creating a script called elasticsearch in /etc/rc.d/init.d/ that is run on every system boot to start the downloader module and re-infect the device.
Last but not least, this malware will also add its own SSH-based backdoor by starting an SSH server using one of the downloaded plugins (Linux.Plugin.Lightning.Sshd). The OpenSSH daemon has encrypted host and private keys, allowing attackers to SSH into infected machines using their own SSH keys. Network communication in the Core and Downloader modules are performed over TCP sockets. The data is structured in JSON. The C2 is stored in a polymorphic encoded configuration file that is unique for every single creation.Lightning Framework is just the latest variant of Linux malware to emerge recently and capable of fully compromising and backdooring devices.
Security researchers also detected OrBit, a stealthy malware that hijacks shared libraries to intercept function calls to steal information from backdoored Linux systems and infect all running processes.
Hashes
| File | SHA256 |
| Lightning.Downloader | 48f9471c20316b295704e6f8feb2196dd619799edec5835734fc24051f45c5b7 |
| Lightning.Core | fd285c2fb4d42dde23590118dba016bf5b846625da3abdbe48773530a07bcd1e |
| Linux.Plugin.Lightning.Sshd | ad16989a3ebf0b416681f8db31af098e02eabd25452f8d781383547ead395237 |

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











