Twilio
Twilio has confirmed that hackers accessed customer data after successfully tricking employees into handing over their corporate login credentials.
The San Francisco-based company, which allows users to embed voice and SMS capabilities, such as two-factor authentication (2FA), into apps, said in a blog post that it realized “someone got unauthorized access to information related to some Twilio customer accounts on August 4”.
Twilio has more than 150,000 customers, including Facebook and Uber. According to the company, the as-yet-unidentified threat actor convinced several Twilio employees to hand over their credentials, which allowed access to the company’s internal systems.
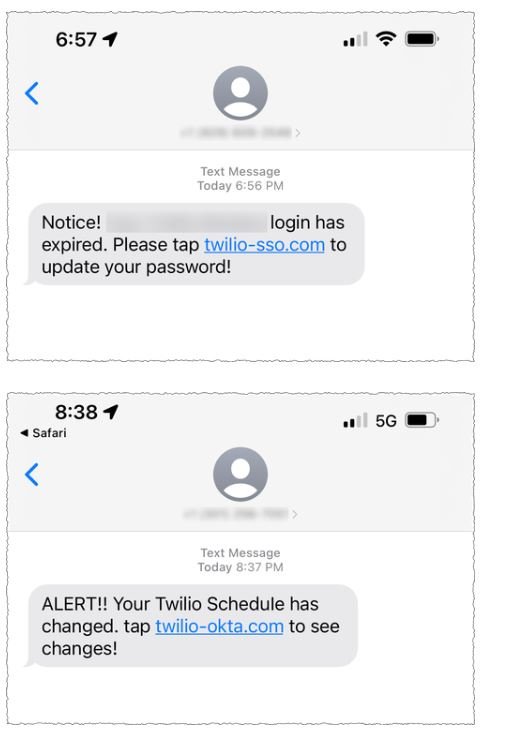
The attack used phishing SMS messages purporting to come from Twilio’s IT department, suggesting that the employees’ password had expired or their schedule had changed, and advising the target to log in with a spoofed web address that controls the attacker.
Twilio said the attackers sent these messages to appear legitimate, including words like “Okta” and “SSO,” referring to single sign-on, which many companies use to secure access to their internal applications. Twilio said it worked with US carriers to stop malicious messages, as well as registrars and hosting providers to shut down malicious URLs used in the campaign.
“Despite this response, threat actors have continued to rotate between carriers and hosting providers to resume their attacks,” Twilio said. “Based on these factors, we have reason to believe that the threat actors are well organized, sophisticated, and methodical in their actions.
The same actor also created phishing pages posing as other IT outsourcing companies and a customer service provider, though the impact, if any, on these organizations is currently unknown.
When contacted, the Twilio spokeswoman declined to say how many customers were affected or what data the threat actors accessed says Twilio’s privacy policy that the information it collects includes addresses, payment details, IP addresses, and in some cases, proof of identity.
Twilio said that since the attack, it has revoked access to compromised employee accounts and increased its security training to ensure employees are on “high alert” for social engineering attacks. The company said it has begun contacting affected customers on an individual basis.
Slack
Slack reported that it reset approximately 0.5% of its users’ passwords, after fixing a bug that exposed hashes , when creating or revoking shared invite links for workspaces.
Slack says it has more than 169,000 paying customers from more than 150 countries, with 65 Fortune 100 companies using its services.
“When a user performed any of these actions, Slack would transmit an encrypted version of their password (not plain text) to other members of the workspace,”Slack. “Even though this data was shared via the new or disabled invite link, the Slack client did not store or display this data to members of that workspace.
The bug was discovered by an independent security researcher who disclosed it to Slack on July 17. The issue affected all users who created or revoked shared invite links between April 17, 2017 and July 17, 2022.

Fortunately, the encrypted passwords were not visible to Slack clients, requiring active monitoring. of encrypted network traffic from Slack servers to access this exposed information, according to Slack.
Slack also added that it has no reason to believe the bug was used to gain access to plaintext passwords before it was fixed. “However, out of an abundance of caution, we have reset Slack passwords for affected users. They will need to set a new Slack password before they can log in again.”
To make sure your account was not compromised, you can access your personal access logs. Slack also advises all users to enable two-factor authentication and create unique passwords that aren’t used with other online services.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











