A researcher has created a free and open source tool that anybody can use to inspect what code is being injected by such browsers. The researcher did a study to discover how big corporations may track user behavior using their mobile in-app browsers.
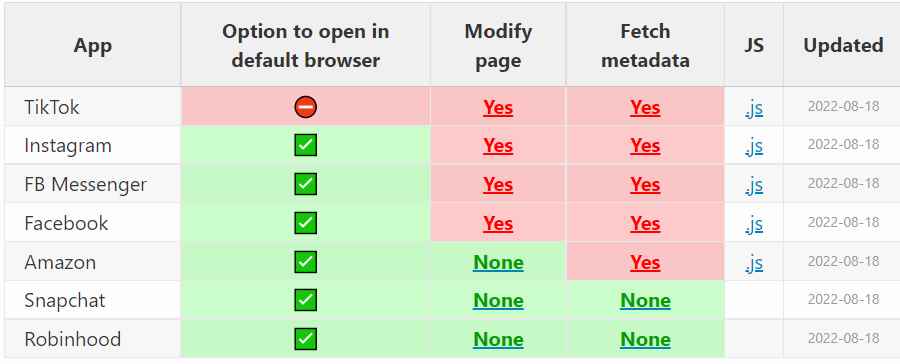
Some mobile applications include built-in browsers that enable users to access other websites rapidly. Other applications have their own browsers that they might use to load the resources they require to carry out certain tasks. These internal browsers could potentially provide privacy and security problems, though.
This month, researcher Felix Krause claimed in a blog post that the iOS applications for Instagram and Facebook could track everything a user did on an external website they visited using the app’s built-in browser.
This assertion was supported by the JavaScript code that the applications inserted into the webpage that the in-app browser showed.
Later studies revealed that TikTok also injects JavaScript code, changing the content of external websites accessed via the social networking app. TikTok appears to be keeping track of all keystrokes and screen touches, which might allow the corporation to gather passwords and other private data inputted into the built-in browser.
According to Meta, the business is injecting the code as part of an App Tracking Transparency (ATT) method to support respecting users’ privacy preferences. The keylogging code is real, according to TikTok, but it’s not being used.
Krause pointed out that, particularly on more recent iterations of iOS, his online tool might not entirely catch all JavaScript injections.
According to Krause, Apple implemented a type of sandboxing for JavaScript in version 14.3 that makes it “difficult for a website to validate what code is being run.”
The researcher said, “On the other hand, just because an app injects JavaScript into external websites, doesn’t guarantee the program is engaging in any harmful activity. We are unable to fully understand the kind of data that each in-app browser gathers, how or not the data is communicated, or how it is used.
When the website inappbrowser.com is accessed using an in-app browser, the online tool known as InAppBrowser shows the JavaScript code that is injected. It also explains the functions of each command.
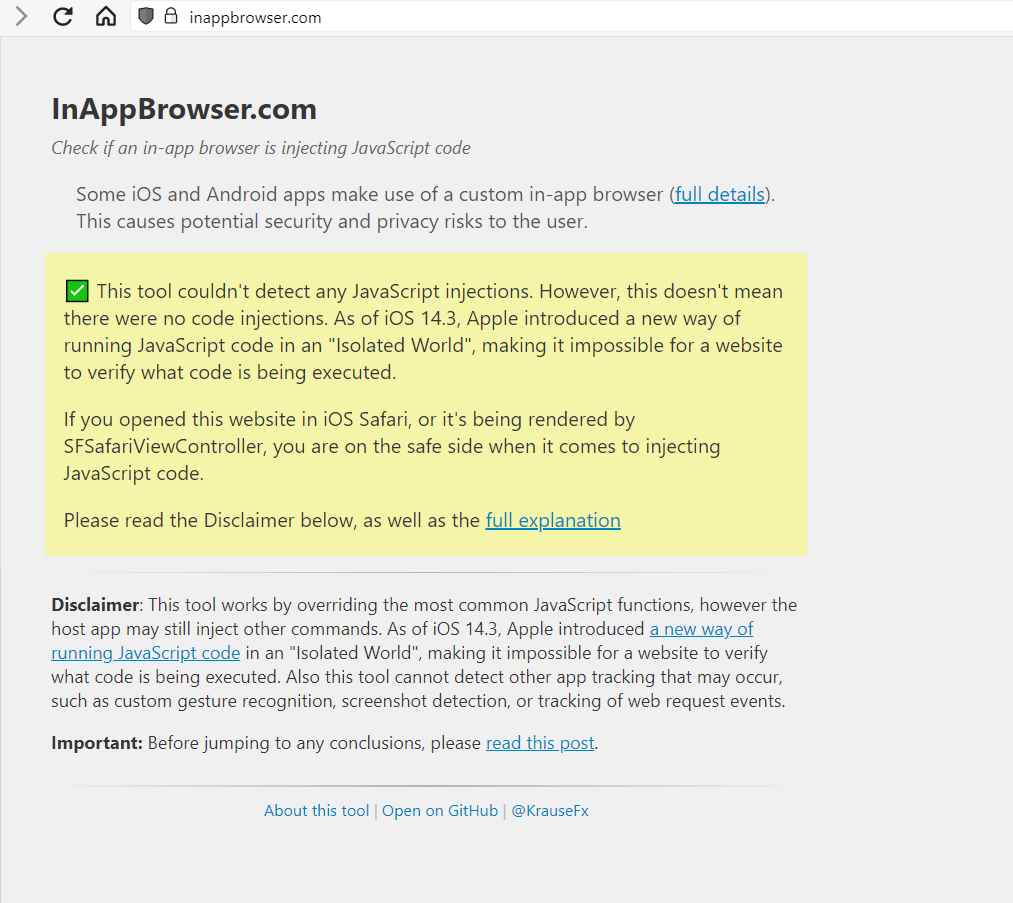
Simply go to InAppBrowser.com by messaging the link to yourself, publishing it, or commenting on it, and the tool should inform you whether any scripts are running, whether they are dangerous or not, and if an app you use is injecting JavaScript into websites via its in-app browser.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











