Given that two people—or maybe the same person—leaked the LockBit 3.0 compiler on Twitter, it appears that LockBit has had a breach.
A newly registered Twitter account by the name of “Ali Qushji” claims that their team broke into LockBits’ servers and discovered a compiler of the LockBit 3.0 ransomware encryptor, according to security researcher 3xp0rt.
VX-Underground reported that they were approached on September 10th by a person going by the handle “protonleaks,” who also supplied a copy of the builder, after security expert 3xp0rt tweeted about the hacked LockBit 3.0 builder.
The public face of the LockBit business, LockBitSupp, asserts that they were not hacked and that a frustrated developer instead exposed the secret ransomware compiler.
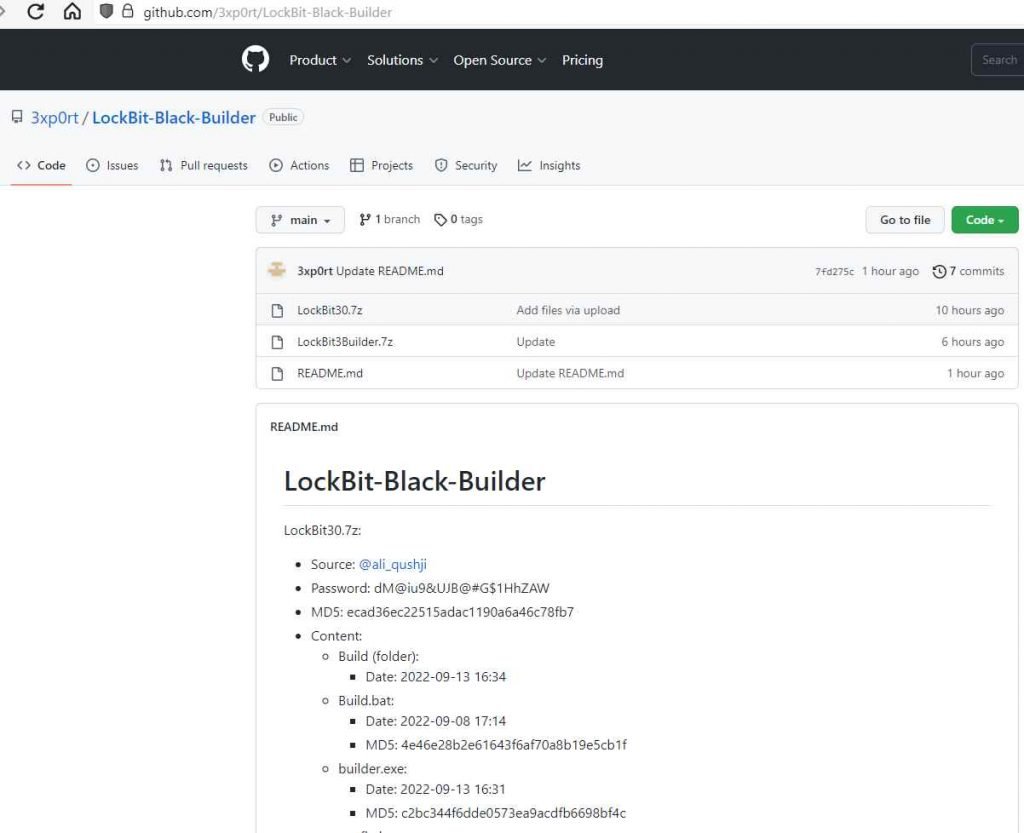
Anyone may easily create the executables needed to begin their own operation, including an encryptor, decryptor, and specialized tools to launch the decryptor in particular ways, using the disclosed LockBit 3.0 builder.
An encryption key generator, a builder, a customizable configuration file, and a batch file to create all of the files are included in the builder.
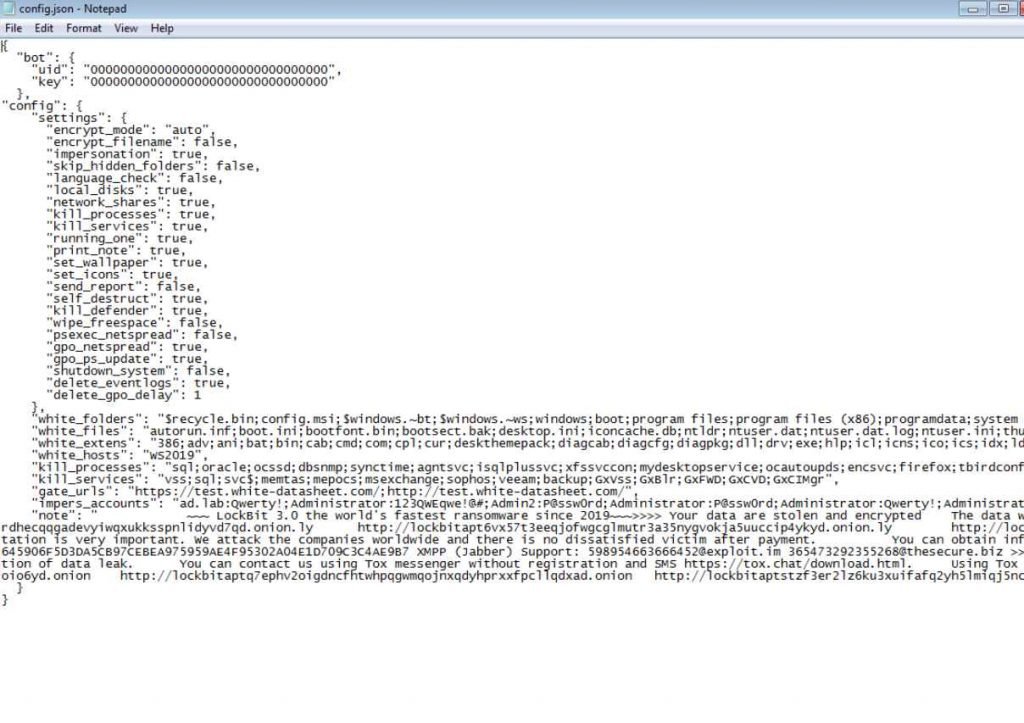
Any threat actor can adapt the configuration file to its requirements and alter the generated ransom message to connect to their own servers. The builder will produce all of the files required to start an effective ransomware campaign when the batch file is performed.
This builder is not the first time a code or ransomware builder has been posted online, prompting a surge in cyberattacks from other threat actors who set up their own businesses.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











