Two security flaws in WhatsApp’s chat app for iOS and Android that might have been used to remotely execute malware on the device were recently reported by the company Meta.
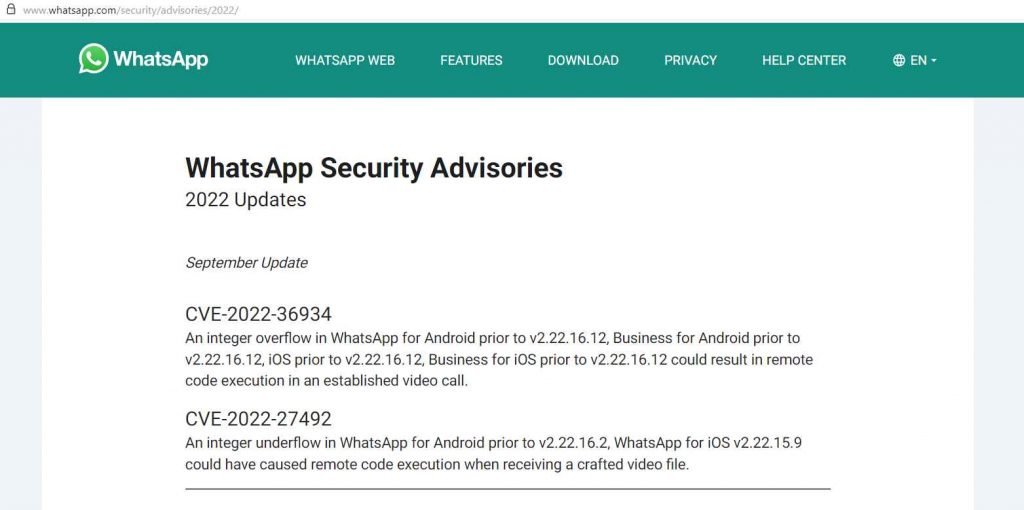
CVE-2022-36934, which has a severe severity rating (CVSS score of 9.8), affects all Android and iOS versions previous to v2.22.16.12, Business for Android prior to v2.22.16.12, and Business for iOS prior to v2.22.16.12. Integer overflow is the root cause of this issue. Unknown code in the component Video Call Handler is vulnerable to this vulnerability. Overflow of a heap-based buffer results from the modification. Declaring the issue with CWE results in CWE-122. On 09/23/2022, the vulnerability was disclosed. Downloads of the advice are available at whatsapp.com. The CVE number for this issue is 2022-36934. Remote activation of the attack is possible. Technical information is not available.
Another flaw, identified as CVE-2022-27492, is an integer underflow that affects WhatsApp versions prior to 2.22.16.2 for Android and 2.22.15.9 for iOS. An attacker might take advantage of this weakness to run arbitrary code on the system by sending the system a specially crafted video file. This issue affects some unknown processing of the component Video File Handler. The manipulation leads to integer underflow. The CWE definition for the vulnerability is CWE-191. The weakness was disclosed 09/23/2022. The advisory is shared at whatsapp.com. The identification of this vulnerability is CVE-2022-27492. The attack may be initiated remotely. There are no technical details available.
It is advised that WhatsApp users update to the most recent version to reduce the risk posed by the CVE-2022-36934 and CVE-2022-27492 issues. According to the business, there is no evidence that any of the vulnerabilities fixed in this version have been used maliciously.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











