The security researchers at ESET found a new high-risk vulnerability in the UEFI firmware of Acer computers. Because to a security flaw that affects numerous types of Acer laptops, an adversary may be able to deactivate the Secure Boot function, allowing them to circumvent security measures and install malicious software. When the Secure Boot feature is disabled, an adversary is able to load their own unsigned malicious bootloader, which gives them complete control over the operation of loading the operating system.
This may provide them the ability to deactivate or circumvent defenses so that they may covertly deliver their own payloads with the privileges of the system. This vulnerability may let modifications to Secure Boot settings by establishing NVRAM variables, and the attack is not particularly difficult to carry out. Because of this, the security rules offered by Microsoft and third-party security software will be unable to eradicate tenacious malware; hence, vulnerabilities in secure boot have a high criticality.
On some Acer consumer laptops, the automatically loaded DXE driver known as HQSwSmiDxe has a this ulnerability that has been assigned the identifier CVE-2022-4020 and received a CVSS score of 8.1. By making changes to NVRAM variables in the absence of any intervention from the user, an adversary with elevated privileges is able to change the default configuration of UEFI Secure Boot. After exploiting the vulnerability to deactivate Secure Boot, Acer warned in a security warning that an adversary may take control of the operating system and load a bootloader that had not been digitally signed.
According to the manufacturer of computers, the affected device models include the Aspire A315-22, A115-21, and A315-22G as well as the Extensa EX215-21 and EX215-21G.
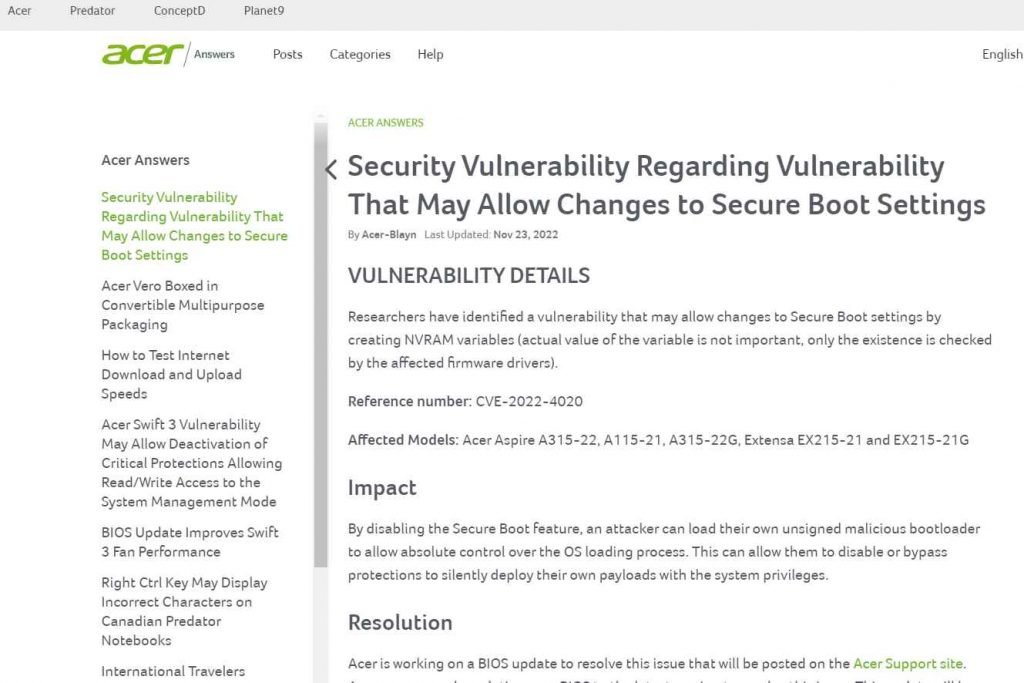
In order to rectify this problem, Acer is now working on a BIOS update, which will subsequently be made available on the Acer Support website. In order to rectify this problem, Acer suggests installing the most recent version of your system’s BIOS. The company states that this fix will be included as a significant part of a future Windows upgrade.
After all, it is unreasonable to anticipate that users would voluntarily download drivers and firmware; hence, the technique of quiet push installation is the most efficient way to ensure that the update is applied to all users as rapidly as possible.
Acer has said that the aforementioned firmware and driver upgrades will be flagged as essential, and that affected models will automatically get the firmware once the patch is released, at which point the user may restart their device.
According to ESET, this problem is similar to CVE-2022-3431, a vulnerability that exists in the DXE driver BootOrderDxe of certain Lenovo laptops. This vulnerability, just like the HQSwSmiDxe DXE driver, checks for the existence of a BootOrderSecureBootDisable variable and disables Secure Boot if the variable is present.
At the beginning of November, ESET issued a security advisory on a flaw affecting Lenovo products and urged customers to promptly update the BIOS of any affected devices.
Now, the cybersecurity group is sounding the alarm on this Acer issue, and they are advising customers to keep a watchful look out for the fixes.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











