daloRADIUS is a sophisticated RADIUS web management tool that has been created with the goal of managing hotspots and ISP installations for general use. User administration, graphical reporting, accounting, and a billing engine are some of the features that are included, and it also connects with GoogleMaps so that users may geo-locate themselves. daloRadius is put to use by a variety of companies in order to manage hotspots and ISP installations that are utilized for general purposes.
The daloRADIUS project team has taken action to fix a high-security vulnerability that was discovered in the program. This vulnerability, if properly exploited, might result in an account takeover. The vulnerability, which is being tracked as CVE-2022-23475, has a CVSS severity score of 8.0. All versions of daloRADIUS that were released previous to version 1.3 are vulnerable to the security issue. daloRadius is put to use by a variety of companies in order to manage hotspots and ISP installations that are utilized for general purposes. An adversary may take control of an organization’s network with the click of a button by establishing a user account with administrative or operator privileges. An attacker will be able to modify the settings of the network, as well as establish new user accounts, remove existing ones, and erase their own.
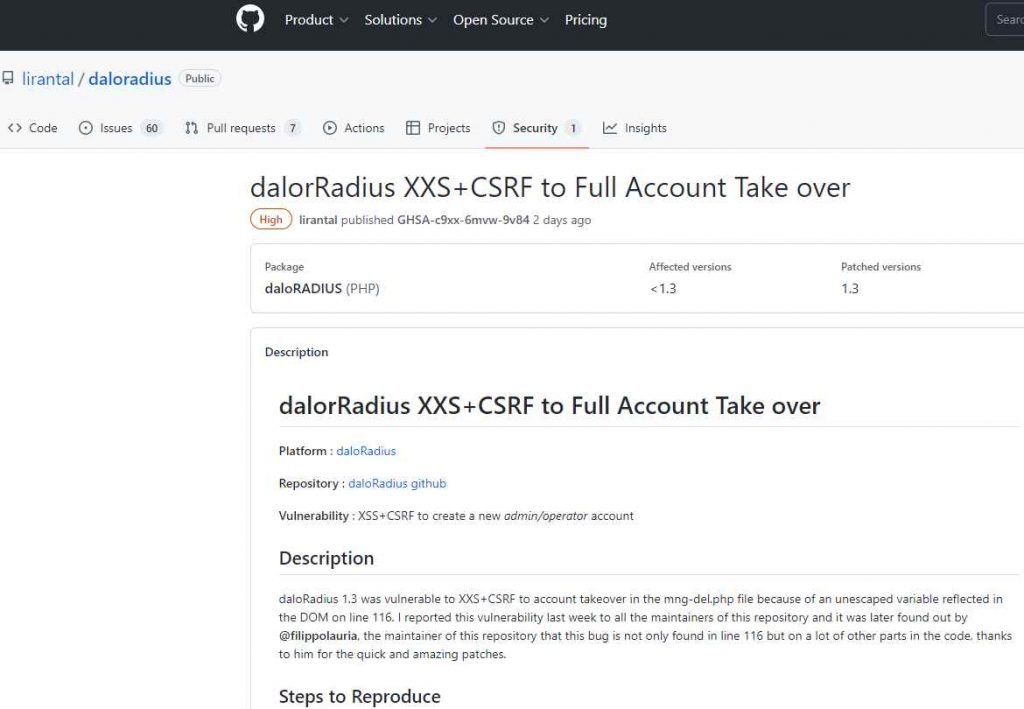
Because of an unescaped variable that was mirrored in the DOM on line 116, daloRadius 1.3 is susceptible to XXS+CSRF attacks that might lead to account takeover. This vulnerability was present in the mng-del.php code. It was discovered later by @filippolauria, the maintainer of this repository, that this flaw is not only located on line 116 but on a lot of other areas in the code; kudos to him for the speedy and great repairs.
The Procedures Needed to Reproduce
1. The /mng-del.php file is where the vulnerability exists, and we may exploit it by sending a request like the one below: http://<domain>/mng-del.php?username[]=a&username[]=%3C%2Ftd%3E%3Cimg+src+onerror%3D%22alert(document.domain)%22%3E to display a basic warning message in a box.
2. If you want to establish a new operator account, you may do so with the following payload.
There is a wide variety of forms that are susceptible to CSRF attacks.
Mitigation
The CSRF vulnerability may be reduced by setting the daloRadius session cookie to the samesite=Lax value or by implementing a CSRF token in all of its forms. Both of these options are viable mitigation strategies.
Either by escaping the XSS or by implementing a content-security policy, we will be able to stop it from happening.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











