Customers were warned by Cisco on Thursday that fixes for a high-severity vulnerability that affects certain of the company’s IP phones are currently under development.
The vulnerability, which is tracked as CVE-2022-20968, affects Cisco IP phones in the 7800 series and the 8800 series (except for the 8821 series). There is no other way around this issue; however, Cisco has offered a mitigation that may be used while waiting for the firm to provide fixes.

The flaw, which has been identified as CVE-2022-20968 and given a score of 8.1 on the CVSS vulnerability assessment, has been characterized as a stack-based buffer overflow that is brought on by faulty bounds checking. A remote attacker might execute arbitrary code or create a denial of service situation on the system by sending specially crafted packets of Cisco Discovery Protocol. These packets would have to be sent in order to overflow a buffer.
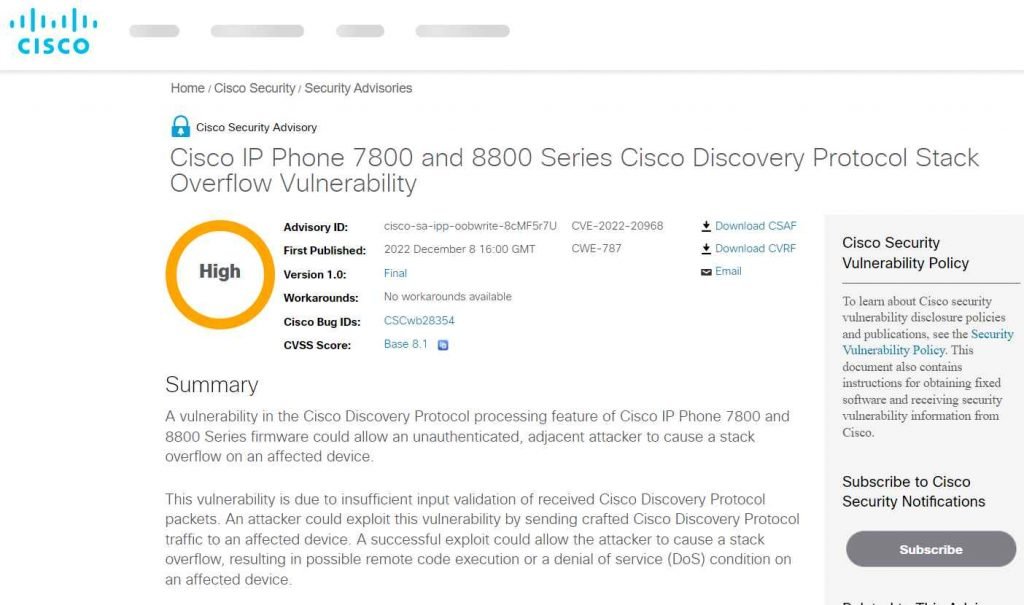
This vulnerability exists as a result of inadequate input validation performed on Cisco Discovery Protocol packets that have been received. An adversary might exploit this issue by sending communication to an affected device that was specially prepared to use the Cisco Discovery Protocol. An exploit that is successful may provide the attacker the ability to trigger a stack overflow, which may result in the execution of remote code or a denial of service (DoS) issue on a device that is vulnerable to the exploit.

The Cisco Discovery Protocol processing capability of Cisco IP Phone 7800 and 8800 Series firmware (with the exception of Cisco Wireless IP Phone 8821) is affected by the CVE-2022-20968 vulnerability.
IP phones manufactured by Cisco that are running firmware versions 14.2 and prior are affected. A fix is expected to be released in January of 2023.
Although proof-of-concept attack code is readily accessible for this issue, the Cisco PSIRT is not aware of any malicious exploitation of the vulnerability at this time.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











