You will be able to construct Spring-powered, production-ready apps and services with the very minimal amount of hassle with the assistance of Spring Boot. An administrative user interface that is open-source and designed for the administration of spring boot apps is known as spring boot administrators. The apps either find themselves via the use of Spring Cloud or register with our Spring Boot Admin Client (using HTTP) (e.g. Eureka, Consul). The user interface consists of nothing more than a Vue.js application built on top of Spring Boot Actuator endpoints.
A remote code execution vulnerability that might let remote attackers execute arbitrary code against Spring Boot apps has been identified as a high-risk vulnerability in the Spring Boot Admin by a security researcher.
Everyone who runs Spring Boot Admin Server, has enabled Notifiers (like Teams-Notifier), and has UI-based write access to environment variables is at risk of being impacted.
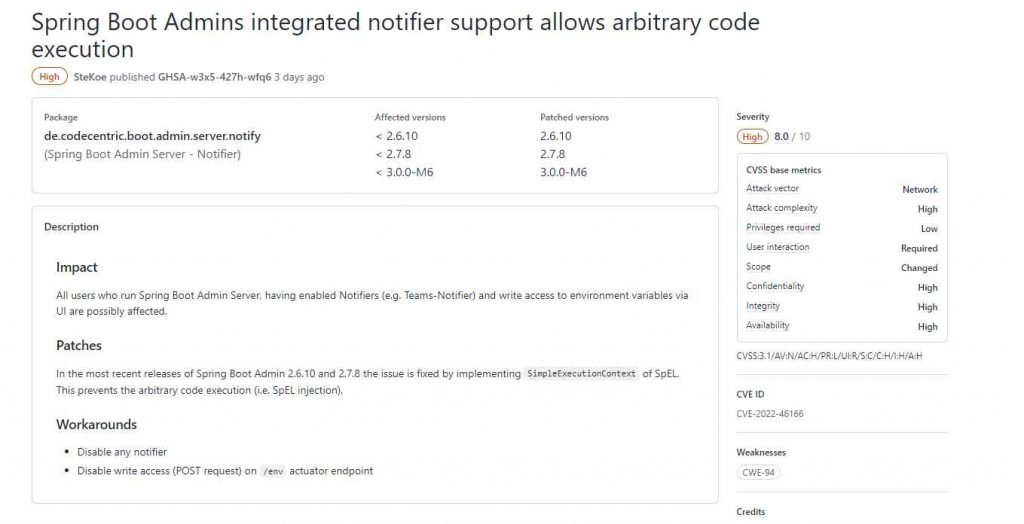
If you are not utilizing Notifiers or if you have blocked write access (POST request) on the /ent actuator endpoint, then you are not susceptible to this issue.
Fixes for this security flaw have been rolled out in Spring Boot Admins versions 2.6.10, 2.7.8, and 3.0.0-M6 that have been issued by Codecentric. Implementing the SimpleExecutionContext feature of SpEL allowed Spring Boot Admin 2.6.10 and 2.7.8 to address the CVE-2022-46166 vulnerability. The execution of arbitrary code is therefore prevented (i.e. SpEL injection).
A security flaw known as CVE-2022-46166 was recently identified in past versions of Spring Boot Admins, including prior versions 2.6.10, 2.7.8, and 3.0.0-M6. Codecentric recently posted an advisory in which the business provided details on this flaw.
Therefore, it is strongly suggested that developers and administrators promptly update their software to the most recent version available.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











