Malware activities carried out by botnets pose a danger to devices and networks that is always developing. Due to the fact that Internet of Things (IoT) devices’ setups often leave them open to attack, threat actors target these devices in order to enlist them into nefarious activities. Additionally, the number of internet-connected devices continues to increase. Operators are redeploying malware for a range of distributions and aims, changing existing botnets to expand operations, and adding as many devices as possible to their infrastructure, according to recent trends.
An example of a threat that is always adapting is Zerobot, which is a Go-based botnet that spreads largely via vulnerabilities in Internet of Things (IoT) devices and online applications. The malware’s controllers are continually adding new exploits and capabilities to it. For many months, the research team for Microsoft Defender for IoT has been keeping an eye on Zerobot, which is also referred to as ZeroStresser by its owners. Since Microsoft began monitoring it, Zerobot has undergone many iterations of modification and has been made available as part of a malware as a service program. The Federal Bureau of Investigation (FBI) seized multiple domains in December 2022 that were related with DDoS-for-hire businesses. Among those domains was one that had ties to Zerobot.
Microsoft has already remarked on the ever-changing environment of potential dangers. The transition in the cyber economy toward malware as a service has industrialized attacks and made it simpler for attackers to purchase and use malware, establish and maintain access to compromised networks, and use ready-made tools to carry out their attacks. This has led to an increase in the number of successful cyberattacks. We have been keeping an eye out for adverts for the Zerobot botnet on a variety of social media networks, in addition to other notifications about the sale and maintenance of the malware, as well as additional capabilities that are currently under development.
The Zerobot botnet, which was discovered for the first time earlier this month, is targeting Apache systems in an effort to broaden the range of Internet of Things (IoT) devices that it is able to attack.
The Zerobot botnet, which was discovered for the first time earlier this month, is targeting Apache systems in an effort to broaden the range of Internet of Things (IoT) devices that it is able to attack.
According to a report that was made public on Wednesday by the Microsoft Security Threat Intelligence (MSTIC) team, the malware-as-a-service (MaaS) model is being used to sell the botnet, which was written in the Go programming language. The botnet spreads through vulnerabilities in Internet of Things (IoT) devices and web applications.
Researchers from Fortinet’s FortiGuard Labs were the ones who made the first discovery of Zerobot at the beginning of December. They said that the botnet was aiming for Linux machines. The objective, much like that of traditional botnets, is to gain control of internet-connected devices such as firewalls, routers, and webcams and incorporate them into a botnet in order to carry out DDoS assaults.
The report that was released by MSTIC this week expands upon the original results that were discovered by FortiGuard by describing the progressions that have been made in the botnet’s most recent generation.
According to research published by MSTIC, “Zerobot 1.1 expands its capabilities by including new attack techniques and new vulnerabilities for supported architectures,” which broadens the scope of the malware’s ability to infect a variety of various kinds of electronic gadgets.
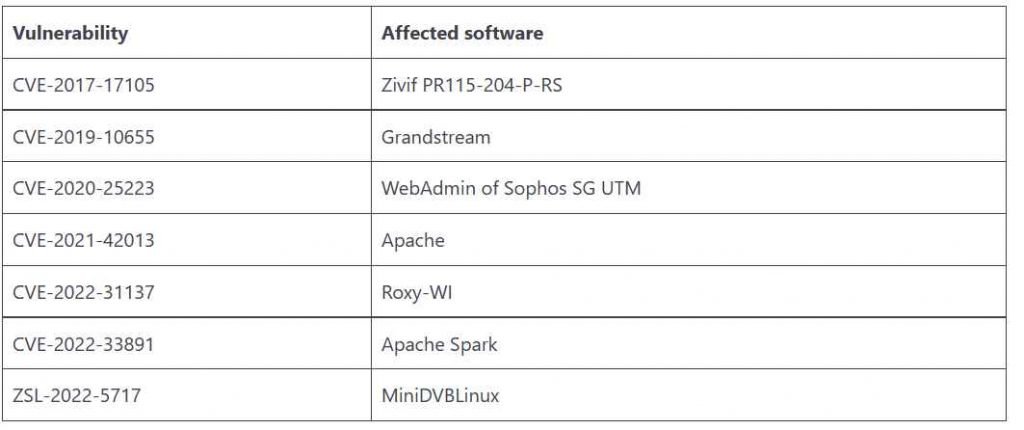
They wrote that Zerobot, which is also known by its operators as ZeroStresser and is tracked by Microsoft as DEV-1061, uses multiple modules to infect vulnerable devices that are based on a variety of architectural designs and operating systems. This information comes from the fact that Microsoft is aware of the malware. The most recent update, however, targets the Apache and Apache Spark operating systems.
According to the information provided by MSTIC, Zerobot 1.1 is now able to exploit vulnerabilities in Apache (CVE-2021-42013) and Apache Spark (CVE=2022-33891). There are also more flaws in the MiniDVBLinux DVR systems, Grandstream networking systems, and Roxy-WI graphical user interface.
The researchers wrote that the botnet takes advantage of vulnerabilities on devices that have not been patched or that have inadequate security measures in place. In some instances, the botnet will use brute-force techniques on vulnerable devices that include insecure configurations that use default or weak credentials.
According to their report, “the malware may try to acquire device access by exploiting a combination of eight popular usernames and 130 passwords for IoT devices using SSH and telnet on ports 23 and 2323 to propagate to devices.” They also noted that efforts have been made to open ports and connect to them via port-knocking on ports 80, 8080, 8888, and 2323.
The malicious payload that is dropped by the botnet is either a generic script named zero.sh that executes Zerobot or a script that downloads the Zerobot binary of a particular architecture via brute force. Either way, the payload is harmful.
In the beginning of this month, the FBI took control of roughly fifty domains that were being used to perform distributed denial of service assaults (DDoS) all over the globe. One of those domains was linked with ZeroStresser.
The Internet of Things is driven by a variety of central processing unit designs, including x86, Arm, and MIPs. Zerobot will continue to sift through many binary options until it locates the correct one.
Additionally, the malware utilizes a variety of persistence mechanisms that are specific to each operating system. The researchers said that they have uncovered samples that can operate on Windows and be saved through the Startup folder, despite the fact that it is unable to propagate to Windows-based computers. It makes use of a mix of desktop entry, daemon, and service setups on systems that are based on Linux.
The Windows samples are derived from a piece of open-source malware that can infect computers running Windows, Linux, and macOS.
Zerobot was known to have nine distinct ways of initiating DDoS assaults, and the researchers at MSTIC identified seven more. These new techniques include sending UDP and TCP packets with customisable payloads, as well as delivering SYN or ACK packets either singly or jointly.
Researchers from Microsoft also discovered a sample that is capable of running on Windows and is based on a cross-platform (Linux, Windows, macOS) open-source remote administration tool (RAT) that has multiple features including the ability to manage processes, perform file operations, take screenshots, and run commands. The discovery of this tool was made possible by research into the command-and-control (C2) IP addresses used by the malware. This Remote Administration Tool (RAT) may be downloaded with the use of a script named impst.sh:
The ongoing development of new capabilities and the speed with which they are being added to the most recent version of Zerobot highlight how urgent it is to establish thorough security measures. The following are some precautions that should be taking to safeguard devices and networks against the danger posed by Zerobot
Utilize security solutions that offer integrated protection across endpoints, identities, email, apps, and data. These solutions have the ability to give cross-domain visibility and detection capabilities.
Adopt a complete IoT security solution lfor IoT to see and monitor all IoT and OT devices, detect and respond to threats, and integrate with SIEM/SOAR and XDR platforms.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











