Fortinet, a company that develops next-generation firewalls, VPNs, antivirus, and endpoint solutions, among other products, issued a public security advisory on October 10, 2022, disclosing that there was a critical vulnerability (CVE-2022-40684) impacting several of their products. The advisory also disclosed that the vulnerability could have been exploited by malicious actors. The security flaw, which Fortinet referred to as an authentication bypass vulnerability, was discovered by the company. An unauthenticated attacker might potentially obtain access to a susceptible Fortinet device if an exploit were to be successfully exploited. To be more specific, the devices that are often integrated with enterprise-wide authentication protocols such as Lightweight Directory Access Protocol (LDAP) and Active Directory (AD) – the “keys to the kingdom,” so to speak.
Fortinet also said in its warning dated October 10 that they had only seen a single instance of the vulnerability being actively exploited. However, this time of peace and tranquility did not last for very long. After another three days, on October 13, 2022, a fully working Proof-of-Concept (POC) exploit code was made available to the public. This sparked a frenzy of activity inside the hacker underground.
TRU was first made aware of a number of threat actors searching the internet for weak Fortinet equipment. TRU then observed hackers buying and selling compromised Fortinet devices in the underground markets while conducting Dark Web hunts. This indicated widespread exploitation, which is a typical result when technical details and knowledge of exploit code become public, and several threat actors begin engaging in exploitation. It seemed that the exploitation operation included the exploitation of previous vulnerabilities, such as CVE-2018-13374, since out-of-date Fortinet devices were not susceptible to the vulnerability that was discovered in 2022.
There was a significant amount of demand from different purchasers, and hacker purchases varied from individual businesses (Figure 1) to mass transactions (Figure 2). One Initial Access Broker was seen providing monthly subscriptions to hacked Fortinet devices located in certain countries and selling this access in bulk at prices ranging between $5,000 and $7,000.
Hackers who employ ransomware get initial access to a college and a major investment business by stealing and using Fortinet virtual private networks (VPNs).
TRU was able to foil and thwart two different cyberattacks in the month of November 2022, both of which originated from weak Fortinet devices that were maintained by third-party service providers. It is not quite apparent if the ransomware attackers obtained access by purchasing it from an Initial Access Broker or whether they carried out the attacks directly. One of the targets was a university in Canada, while the other was an international investment company.
After gaining a foothold in the targets’ information technology environments through the Fortinet VPNs, the threat actors in both instances used Microsoft’s Remote Desktop Protocol (RDP) service to achieve lateral movement. This was done by abusing trusted Windows processes, which are also known as LOLBINs or living-off-the-land binaries. Both the lawful encryption applications BestCrypt and BitLocker were exploited by the hackers, despite the fact that their original purpose was to safeguard the data and not to keep it hostage.
Fortinet has recently patched a number of security flaws that were present in its products. The company also issued a warning to its clients on a high-severity command injection weakness that affected the Application Delivery Controller FortiADC. This bug is identified as CVE-2022-39947 and has a CVSS score of 8.6.
The CVE-2022-39947 problem is an inappropriate neutralization of special elements that are employed in an OS Command vulnerability in FortiADC; it has the potential to lead to the execution of arbitrary code if certain HTTP requests are specially designed.
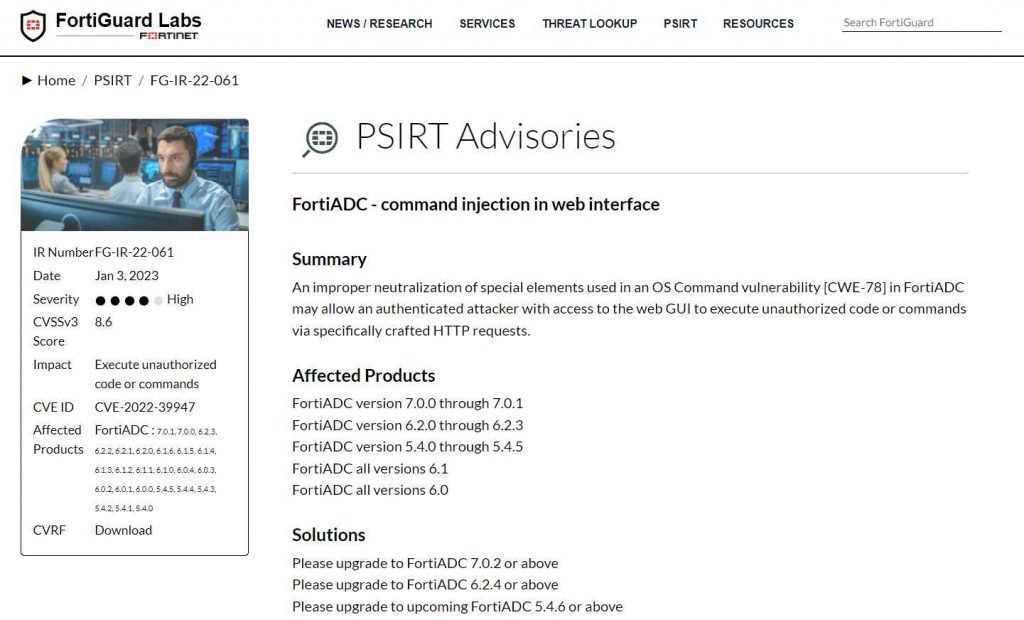
“An improper neutralization of special elements used in an OS Command vulnerability [CWE-78] in FortiADC may allow an authenticated attacker with access to the web GUI to execute unauthorized code or commands through the use of specifically crafted HTTP requests,” according to the report. “This vulnerability exists because FortiADC does not properly neutralize special elements that are used in OS Command vulnerabilities.” reads the advise that was written by the vendor and publishes it.
The following is a list of versions that are affected:
FortiADC versions 7.0.0 through 7.0.2 were released.
Between version 6.2.0 and 6.2.3 of the FortiADC
Between version 6.1.0 and 6.1.6 of the FortiADC
Between version 6.0.0 and 6.0.4 of the FortiADC
Between version 5.4.0 and 5.4.5 of the FortiADC
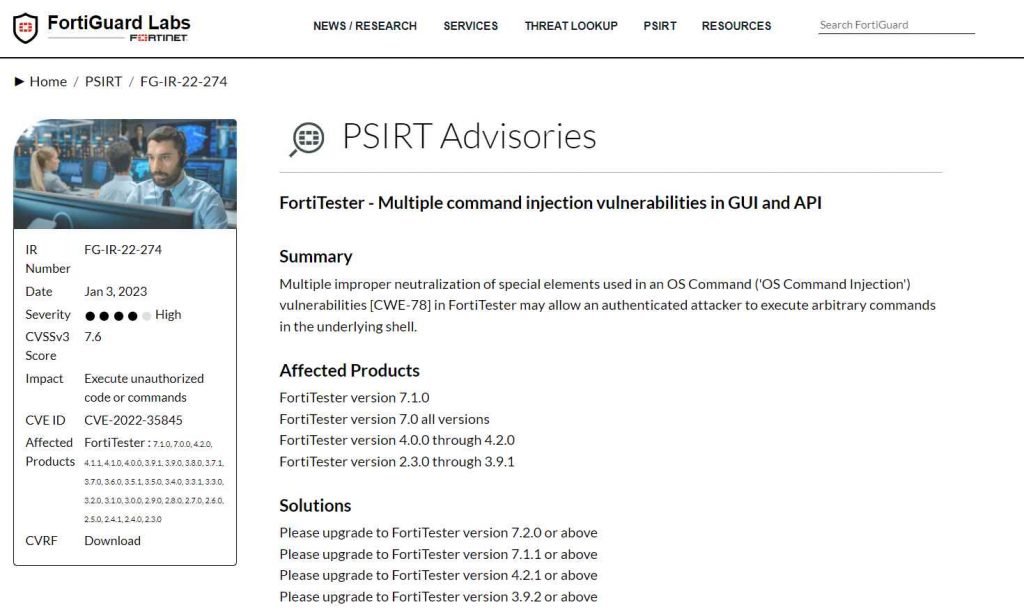
Additionally, the vendor patched a number of critical command injection flaws in FortiTester. These flaws, which are listed under the CVE identifier CVE-2022-35845 and have a CVSS severity rating of 7.6, might have enabled an authorized attacker to run arbitrary instructions in the underlying shell.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











