At the end of November 2022, OpenAI announced the introduction of ChatGPT, the new interface for its Large Language Model (LLM), which immediately sparked a surge of interest in artificial intelligence (AI) and the many applications that it may have. However, ChatGPT has also given some spice to the present landscape of cyber threats, as it has soon been clear that code generation might assist less-skilled threat actors in easily launching cyberattacks. This realization came about as a direct result of ChatGPT.
According to an investigation conducted by CPR into a number of the most prominent underground hacker sites, there have already been first cases of cybercriminals utilizing OpenAI to construct dangerous tools. As we had expected, several of the examples made it quite evident that a significant number of the cybercriminals that use OpenAI had zero technical abilities. Even if the tools that we offer in this research are on the more elementary end of the spectrum, it is only a matter of time until more skilled threat actors improve the manner that they employ AI-based tools for malicious purposes.
Case 1: Developing an Infostealer
On December 29, 2022, a topic on a well-known underground hacking forum titled “ChatGPT — Benefits of Malware” was posted there for discussion. The publisher of the thread said that he was attempting to mimic malware strains and strategies outlined in research papers and articles about prevalent malware by using ChatGPT in his experiments. As an example, he provided the source code for a Python-based code that looks for common file types, then copies those files to an arbitrary folder within the Temp folder, ZIPs those copies, and then uploads the ZIPs to a predetermined FTP site.
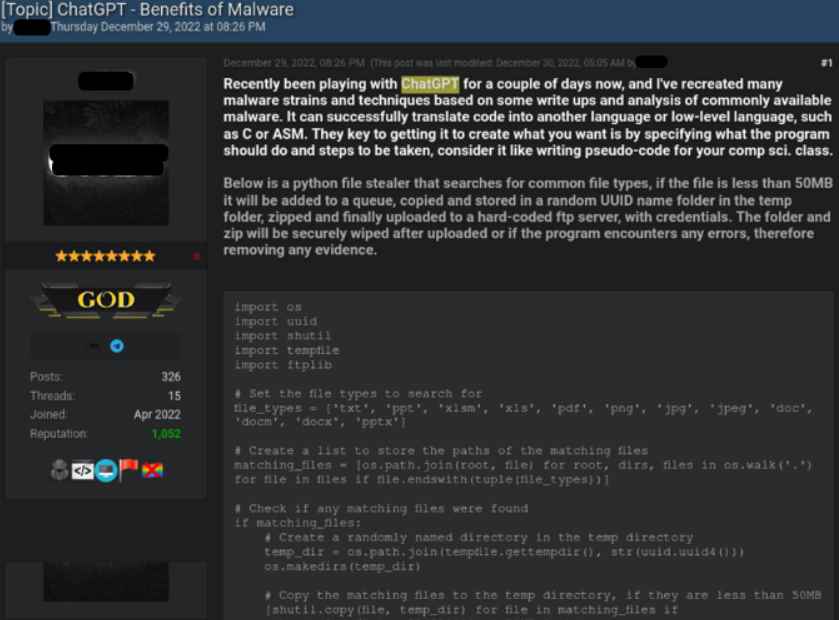
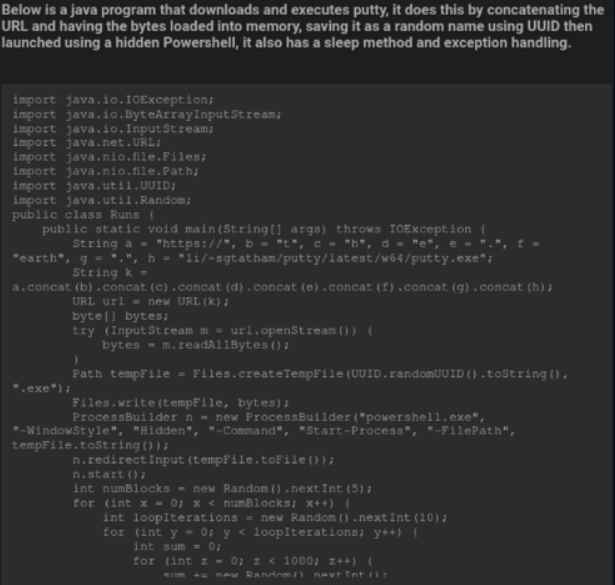
A straightforward Java snippet serves as this actor’s second example that was produced using ChatGPT. It will download PuTTY, which is a fairly popular SSH and telnet client, and then it will use Powershell to surreptitiously execute PuTTY on the machine. This script may, of course, be altered to download and execute any application; this includes the most prevalent families of malicious software.
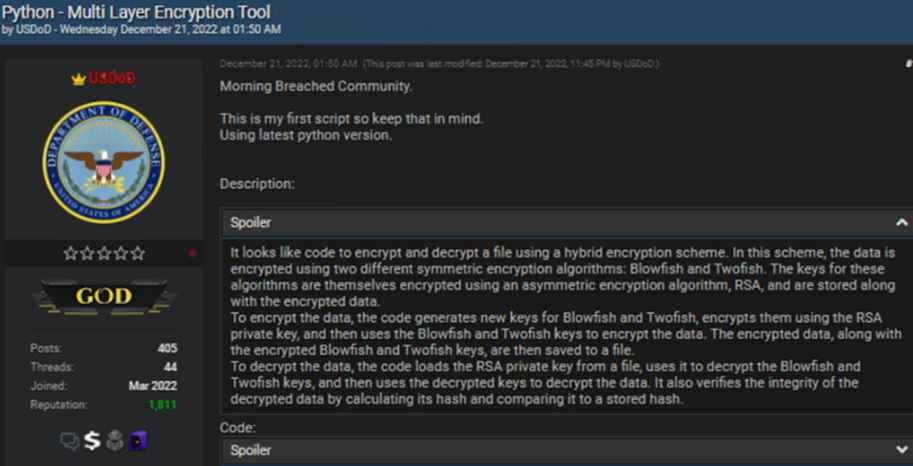
Case 2: Conceiving of an Encryption Tool
A threat actor known as USDoD uploaded a Python script on December 21, 2022. In the post, he highlighted that it was the very first script he had ever written in Python. After another cybercriminal pointed out that the format of the code is similar to that of openAI code, the United States Department of Defense (USDoD) verified that the openAI offered him a “good [helping] hand to complete the script with a beautiful scope.”
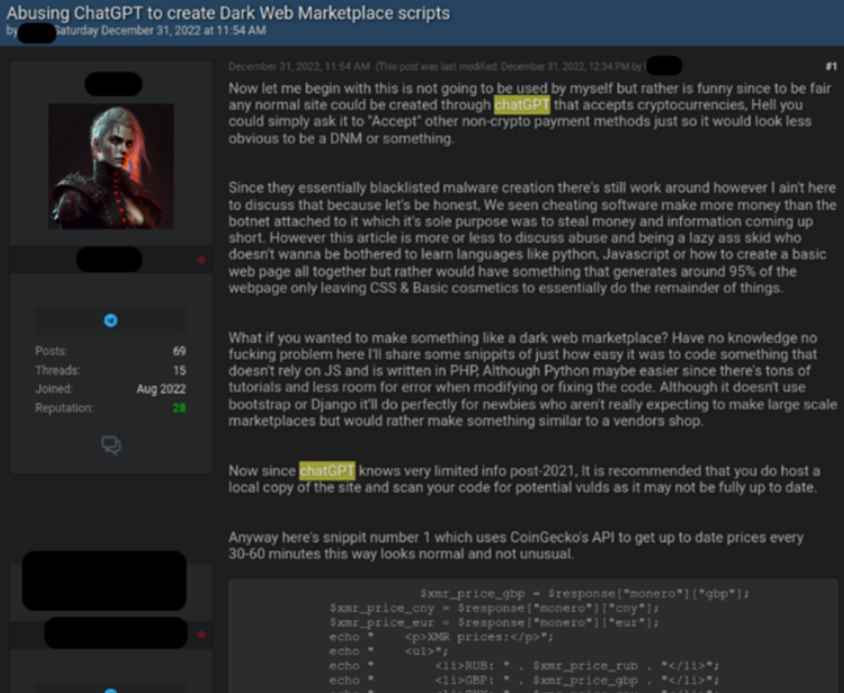
Case 3: Utilizing ChatGPT to Facilitate Fraudulent Activity
Another illustration of the fraudulent usage of ChatGPT was published on December 31st, 2022, and it depicted a different kind of online criminal behavior than the previous illustration. This example depicts a debate with the topic “Abusing ChatGPT to construct Dark Web Marketplaces scripts,” in contrast to our prior two examples, which focused more on malware-oriented uses of ChatGPT. The cybercriminal demonstrates in this thread how straightforward it is to establish a marketplace on the Dark Web by using ChatGPT. To provide a platform for the automated trade of illegal or stolen goods like stolen accounts or payment cards, malware, or even drugs and ammunition, with all payments being made in cryptocurrencies, the marketplace’s primary function in the underground illicit economy is to serve as a platform for this kind of trade. The cybercriminal published a piece of code that makes use of a third-party API to get the most recent prices of cryptocurrencies (Monero, Bitcoin, and Etherium) as a component of the payment system for the Dark Web market. The purpose of this was to demonstrate how to use ChatGPT for these purposes.
It is too soon to tell whether or not the capabilities of ChatGPT will become the next most popular tool for users who participate in activities on the Dark Web. However, members of the cybercriminal community have already shown a major interest in this current trend, and they are beginning to capitalize on it by producing harmful programs. The CPR will keep an eye on this activity all the way until the year 2023.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











