Technology business Dell has its headquarters in the United States. It is in the business of creating and selling computers as well as repairing and supporting related goods and services. Dell is a subsidiary of Dell Technologies, which also owns the corporation.
It has come to light that the Dell BIOS has four newly discovered security flaws that, if properly exploited, might lead to the execution of code and the reading of certain parts on susceptible computers.
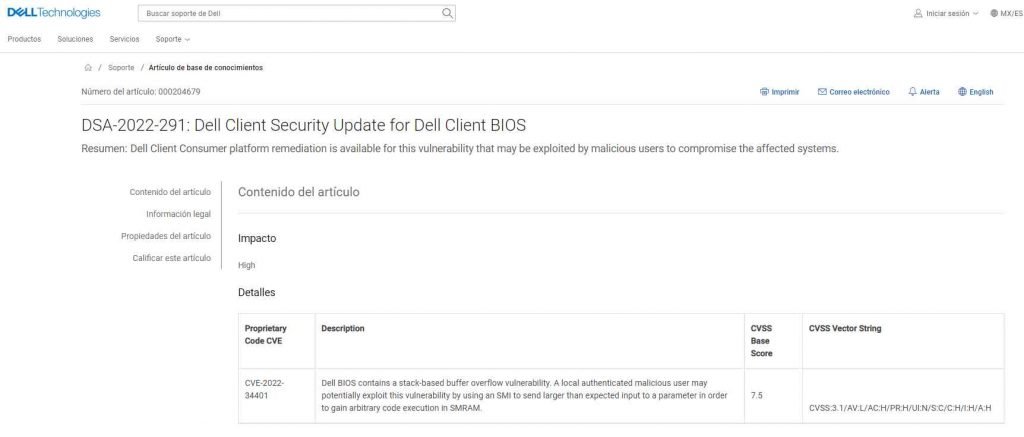
Identified as CVE-2022-34401 with a CVSS score of 7.5, this vulnerability affects three different Dell products (Alienware m15 A6, Alienware m17 Ryzen Edition R5, Dell G15 5525). An exploitable stack-based buffer overflow vulnerability may be found in the Dell BIOS. By using a SMI to provide greater than anticipated input to a parameter in order to obtain arbitrary code execution in SMRAM, a locally authenticated malicious user has the capability to exploit this issue and take advantage of its potential impact.
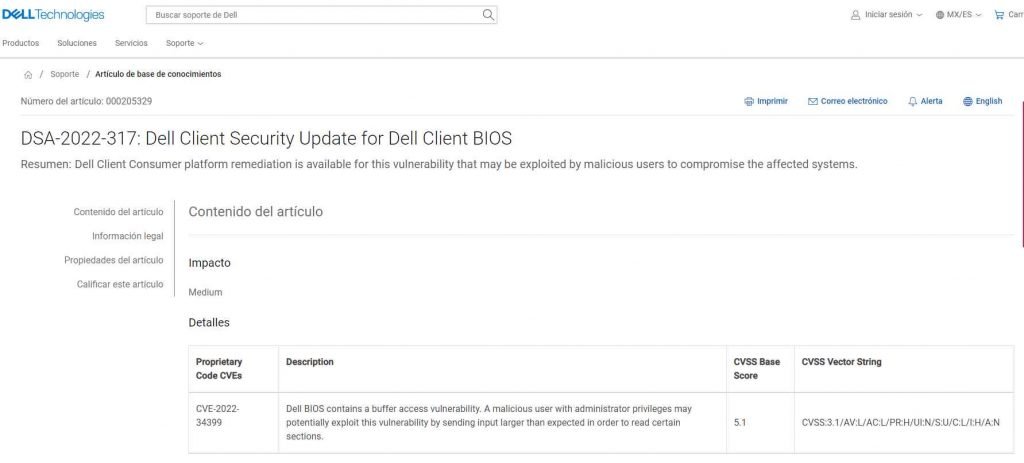
CVE-2022-34399 has an effect on fifteen different models of Dell computers (CVSS score of 5.1). There is a buffer access vulnerability present in the Dell BIOS. This vulnerability might possibly be exploited by a malicious user who has administrator rights by supplying input that is greater than what is intended in order to read certain areas.
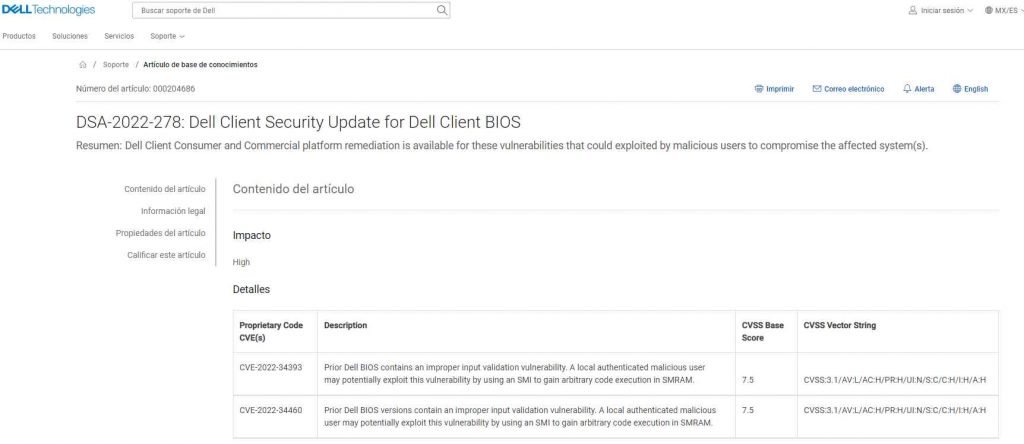
The third and fourth vulnerabilities, CVE-2022-34393 and CVE-2022-34460, respectively, each have a score of 7.5 on the CVSS scale and impact Dell laptop models. An erroneous input validation vulnerability exists in earlier versions of the Dell BIOS. By using a SMI, a local malicious user who has already been authenticated has the capability to exploit this vulnerability and get arbitrary code execution in SMRAM.
A variety of Dell products, including as the G5 SE 5505, Inspiron, and Vostro line-ups, are affected by the problem. According to Dell, it has already distributed BIOS upgrades for the devices that were afflicted by theses issues. Dell highly advises that all of its clients update their software at the earliest available time.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











