Lexmark products are susceptible to server-side request forgery because to insufficient input validation in the Web Services capability, as tracked by CVE-2023-23560. A remote attacker might use this vulnerability to launch an SSRF attack on the system, enabling the attacker to execute arbitrary code. A vulnerability in the Web Services capability of newer Lexmark machines has been detected as a Server-Side Request Forgery (SSRF). An attacker may exploit this issue to achieve arbitrary code execution on the device.
Although there is no evidence that the CVE-2023-23560 problem has been exploited in the wild, proof of concept code has been made available. An SSRF vulnerability in the context of a printing service might allow attackers to read print jobs, gain the network credentials for the printer, and perhaps switch to other devices on the same segment.
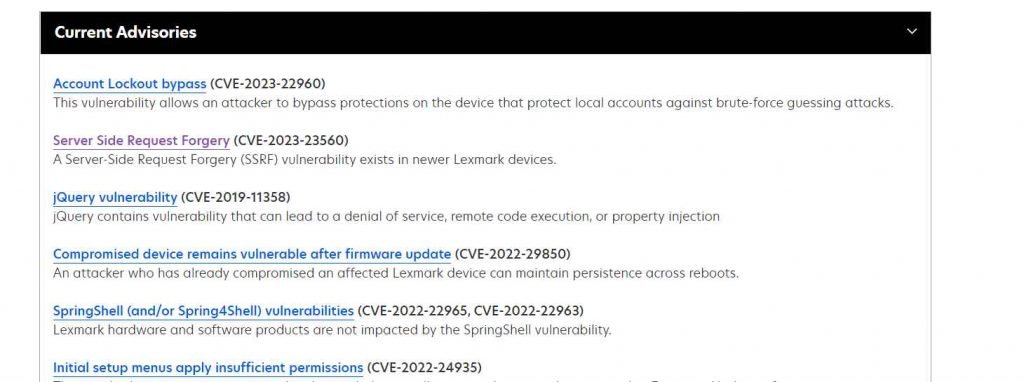
A second vulnerability concerns the device’s bypass protections (CVE-2023-22960, CVSS score: 5.3), which might be exploited by an unauthenticated attacker to circumvent the brute-force defense, enabling unrestricted attempts to guess the credentials of a local account.
A of the issues is serious, with a severity rating of 9.0 out of a possible 10, according to the makers of laser printers and image equipment in their first security alert for 2023.
According to the security alert, more than 100 printer types are susceptible if they use a vulnerable firmware update. Users should verify their firmware level to ensure that it corresponds to an update that resolves the problem.
Lexmark’s security alert contains a complete list of possibly impacted devices, vulnerable firmware revisions, and the updated version that fixes the vulnerability.
Because CVE-2023-23560 affects a significant number of Lexmark printers, owners of Lexmark equipment should review the advice and ensure they’re using a secure firmware version published on or after January 18, 2022.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











