The components that make up contactless payment systems include credit and debit cards, key fobs, smart cards, and other devices, such as smartphones and other mobile devices that employ radio-frequency identification (RFID) or near-field communication (NFC, which is used in Samsung Pay, Apple Pay, Google Pay, Fitbit Pay, or any bank mobile application that supports contactless) in order to make safe payments.
Prilex is a solitary threat actor that began as malware aimed targeting ATMs but has now morphed into novel modular PoS malware, which is actually the most sophisticated PoS threat experts have seen to this yet.
The most current Prilex variant, which was found in November 2022 and seems to have originated from a different source than the others, was noticed by specialists in the wild and they managed to get it. Prilex now makes use of a rule-based file, which allows users to choose whether or not to record credit card information and provides users with the option to prevent NFC-based transactions. This is because NFC-based transactions often produce a one-time-use identification number or card number that is only valid for that specific transaction. The following notice will appear on the PIN pad in the event that Prilex identifies an NFC-based transaction and prevents it from proceeding.
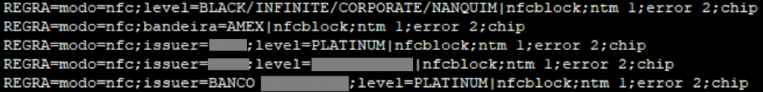
It goes without saying that the objective here is to coerce the victim into using their physical card by having them insert it into the PIN pad reader. This will allow the malware to obtain the information that is generated by the transaction by employing all of the methods that were outlined in our earlier publication, such as performing a GHOST attack and manipulating cryptograms. The ability to filter credit cards according to section and to establish separate criteria for each segment is yet another intriguing new feature that has been incorporated in the most recent Prilex samples. For instance, these rules can only block NFC and capture card data if the card in question is a Black/Infinite, Corporate, or another tier with a high transaction limit. Credit cards with high transaction limits are much more appealing to potential thieves than standard credit cards with low balances and limits.

The number of payments made via this technique has expanded dramatically, and it is anticipated that this trend will continue to expand in the years to come as both the availability of contactless cards and their acceptance rates continue to rise throughout the globe. Because the transaction data produced during a contactless purchase are meaningless from the standpoint of a cybercriminal, it is obvious that Prilex needs to compel victims to enter the card into the infected PoS terminal in order to complete the attack. This ingenious ruse enables the organization to keep functioning while it searches for a method to conduct fraud using individual credit card details.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











