Recently, a vulnerability that might possibly result in the variable that stores the command being released more than once was identified in the widely used Linux function known as sudo. This flaw, which is known as a double-free vulnerability, has the potential to cause the computer system to crash or might potentially be exploited by a malicious user to obtain unauthorized access. CVE-2023-27320 is the name of the vulnerability that exists in the per-command chroot function of sudo. This capability enables users to designate an alternative root directory that sudo would shift to before carrying out the operation.
Only a user who has been given sudo access via a sudoers rule that has a “CHROOT” setting and the rule must match the current host may trigger the flaw. This means that the bug can only be caused by a user. There will be no effect on anything if no users have sudoers rules that include the word “CHROOT.” This function is not used very often.
The fact that the bug has not been reported by anybody else has led experts to conclude that it has not been exploited by hackers. This vulnerability affects versions of Sudo 1.9.8 through 1.9.13p1, including the most recent release. Nevertheless, sudo versions older than 1.9.8 are not vulnerable to this issue. The memory leak that was fixed in Sudo 1.9.8 was in the set cmnd path() method. This memory leak caused the “user cmnd” variable to be released twice, however this only occurred when processing a sudoers rule that had a “CHROOT” value. The Defaults setting for “chroot” will not be changed as a result of this. The problem will only be triggered by a “CHROOT” configuration that is applied to individual rules.
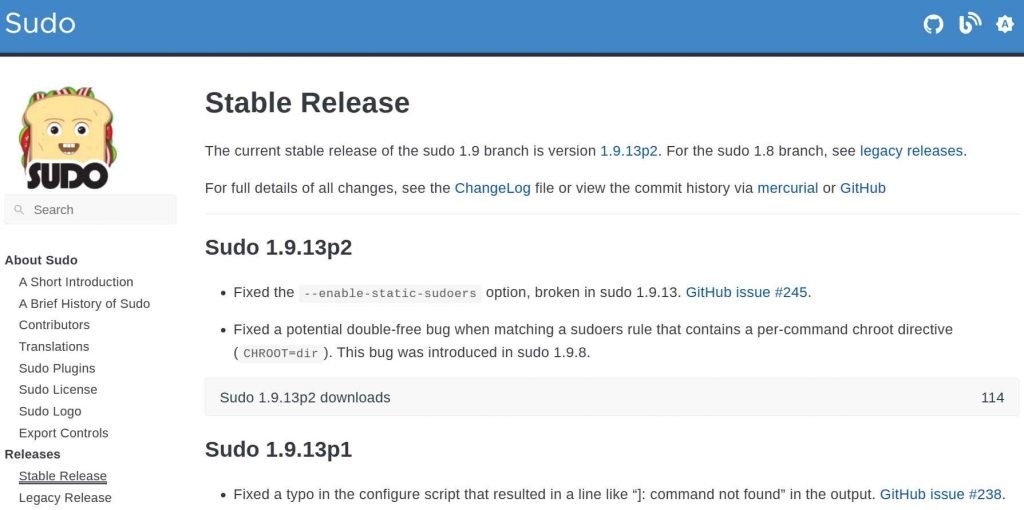
Due to the fact that the per-command chroot capability is rarely used by the majority of users, the effect of the CVE-2023-27320 flaw is not particularly severe. Only a user who has been given sudo capabilities by means of a sudoers rule that has a “CHROOT” setting will be able to trigger the flaw, and the rule itself must be able to match the currently active host. The issue has been resolved in sudo version 1.9.13p2, and users are strongly recommended to switch to this version as soon as they are able to do so. Maintaining the most recent version of your software is very necessary at all times, but it is especially important when security flaws have been uncovered and fixed.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











