The contents of the clipboard may be an enticing target for cyberattacks since mobile users often copy and paste sensitive information, such as passwords or payment information, using the clipboard. By using clipboards, attackers may be able to acquire information about their targets and exfiltrate valuable data. Even instances of attackers seizing control of the clipboard and replacing its contents for nefarious reasons have been documented. One such instance involves the modification of a copied cryptocurrency wallet address just before the user pastes it into an app that manages cryptocurrency wallets or into a chat message. In addition, these kinds of attacks take use of a legal component of the system rather than exploiting a weakness, which makes it more difficult to find a solution to the problem.
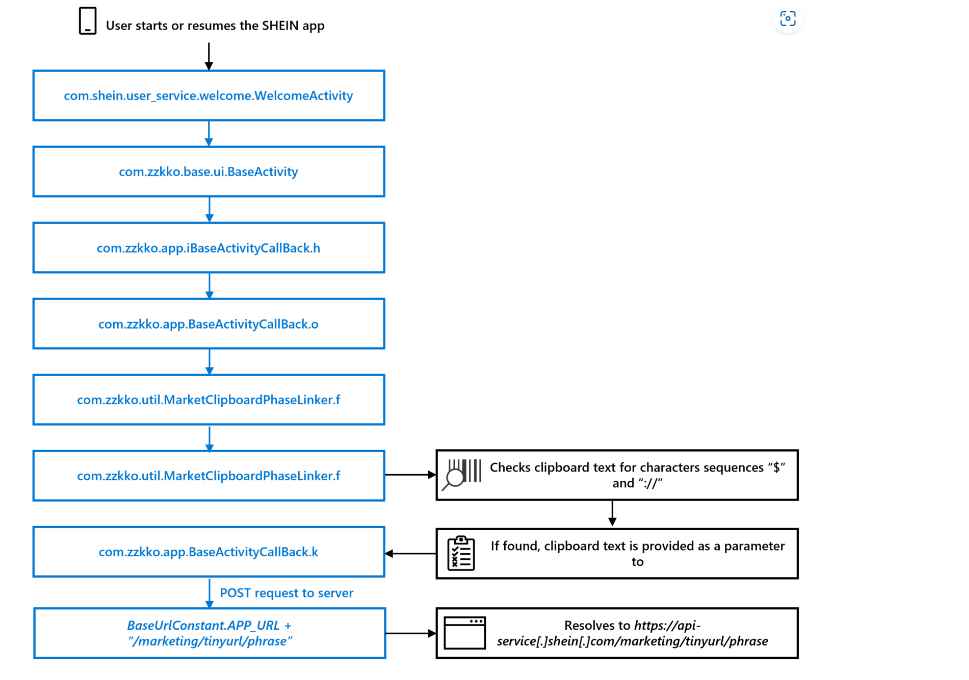
Microsoft discovered that an older version of the SHEIN Android application would periodically read the contents of the clipboard on an Android device and, if a particular pattern was present, would send the contents of the clipboard to a remote server. This was discovered after the company discovered that the SHEIN Android application was developed by SHEIN. We are not directly aware of any nefarious intent behind the behavior, but after doing an analysis, they determined that this behavior is not required for users to complete the goals they have set for themselves inside the program.
The Android application for SHEIN is now available on the Google Play Store, where it has already been downloaded more than 100 million times. Even though SHEIN’s clipboard behavior did not entail any malicious intent, this sample scenario demonstrates the hazards that installed apps might bring. These risks include those applications that are very popular and can be downloaded via the platform’s official app store. They informed Google, the company that runs the Play Store, of our discoveries, which subsequently prompted the Android Security Team to conduct an investigation. In May of 2022, Google notified that the behavior had been deleted from the application, and they verified that this was the case.
In order to validate the results of this static analysis, they carried out a dynamic examination of the application, which consisted of downloading it from the Google Play Store and installing it on a Samsung smartphone that was running Android 9.
In order to investigate how an application interacts with the clipboard, they used Frida to intercept calls made to the android.content.ClipboardManager.getText and com.zzkko.util.MarketClipboardPhaseLinker.f methods. Frida was also used by the team in order to circumvent the application’s certificate pinning and so allow the usage of Burp Proxy for the purpose of network traffic analysis. As was demonstrated in this case involving SHEIN, Android applications are able to make a call to the android.text.ClipboardManager API to read from or write to the device clipboard without first requesting the user’s approval or requiring any particular Android permission. This is because these actions do not require the clipboard to be managed by Android. The ClipboardManager application programming interface (API) makes it possible for apps to simplify certain user actions, such as quickly selecting text to copy. However, applications typically should not be required to make use of this API because the device input method editor (keyboard), which is a separate application, handles the majority of the copying and pasting tasks.
Even behavior in apps that seems to be harmless might be abused for harmful purposes, despite the fact that the team is not aware of any malevolent intent on the part of SHEIN. All information that is copied and pasted is at danger of being stolen or manipulated by attackers if clipboards are targeted by threats. This includes passwords, financial details, personal data, cryptocurrency wallet addresses, and other sensitive information.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











