Throughout the course of the investigation by researchers, a total of twenty distinct spam campaigns were found to have been directed against the countries of Chile, Mexico, Peru, and Portugal. Theft of credentials was the primary goal of these efforts, which especially targeted online banking, schools, government agencies, social networking, gaming, ecommerce, public repositories, and Outlook email accounts. In a few of the incidents, the cyber criminals built phony web sites for the victim, such as windows for online banking. The perpetrators of the attack first attempted to infect their victims by tricking them into opening a variety of bogus invoices by using either HTML pages or PDF files that were password secured.
The total number of government websites that victims were accessing when their credentials were compromised is as follows:
Chile:105
Mexico: 431
Peru: 265
The following is a list of online banking websites in latin america that victims were using when their credentials were compromised and subsequently stolen:
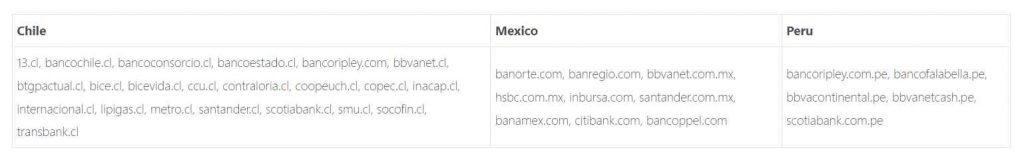
In these campaigns, strategies, tactics, and processes known as TTPs were used that are similar to the banking trojan known as Mispadu.
ESET made the discovery of the malware known as Mispadu around 2019; it is known to target nations in South America via spamming and malicious advertising activities. Because of the group’s malware-as-a-service mode of operation as well as the high level of activity it displays in the area, it is vital to keep an eye on this organization. As a consequence of this, the gang has been continually launching new sorts of operations. These campaigns feature many levels of obfuscation as well as new methodologies, which makes it challenging to adequately safeguard systems against the threat.
Compromising genuine websites and using them as Command & Control Servers for the purpose of furthering the propagation of malware is one of their primary techniques. They achieve this by scanning for websites using outdated versions of content management systems, like WordPress, and compromising those websites. From that point on, they leverage these websites to spread malware in a customized manner. For example, they may filter out countries that they do not wish to infect, drop different types of malware depending on the country that is being infected, and even deploy a one-of-a-kind malicious RAT (Remote Administration Tool) when they detect an interesting device, such as a computer belonging to an employee of a bank.
Throughout these campaigns, the gang will not consider a victim if that person’s system language is any of the following:
Spanish Spain
The English United States of America
Portuguese – Brazil
Since the cybercriminals have automated a method for producing payloads, they are able to swiftly distribute new kinds of malware. As a result, they can extend their operations and run many campaigns in simultaneously.
According to the findings of research of the malware, it is abundantly evident that the gang has an in-depth understanding of the major financial institutions and banks located inside the Latin American nations under attack. The use of several Spanish terms in their malware provides evidence that some of the programmers may be of Latino descent; more precisely, the slang that was used in the comments provides evidence that some of the programmers may be from Chile.
Researchers found numerous additional strategies that were incorporated in this enormous outbreak, which allowed the cybercriminals to access hundreds of different credentials. .
Its multi-stage infection method breaks the dangerous tactics down into their constituent parts, making it more difficult to spot. The following figure provides a visual representation of this tactic:
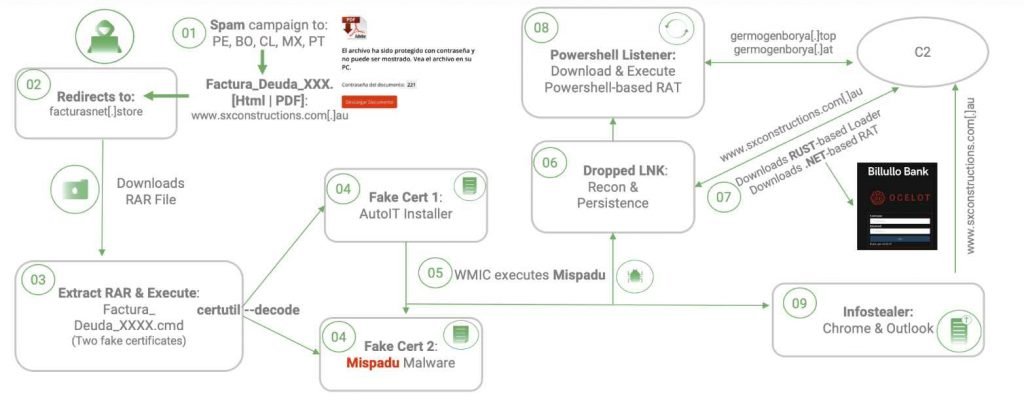
In order to make it more difficult to detect, cybercriminals embed malware inside of false certificates. They then utilize an authorized Windows tool called “certutil” in an improper manner in order to decode and run the banking malware.
Although while Mispadu campaigns were successful in compromising thousands of users, the infection rate of corporate users (who typically have both an antivirus and an EDR/XDR) is still relatively low. This is because corporate users generally have both of these security measures in place.
However, businesses need to operate under the assumption that at some point in the not-too-distant future, one of their employees will be compromised. As a result, they should devise a plan that will help cut down on the amount of time it takes to detect and respond to security threats, while also improving the SOC’s monitoring, detection, and response capabilities.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











