The renowned Mirai botnet, which is responsible for a multitude of debilitating DDoS attacks, has once again upgraded its arsenal. This time, it is taking advantage of a newly fixed vulnerability in TP-Link Archer AX21 Wi-Fi routers. During the Pwn2Own Toronto competition, numerous teams independently found and revealed the vulnerability identified as CVE-2023-1389, which had a CVSS score of 8.8.

An unauthenticated command injection vulnerability known as CVE-2023-1389 exists in the localization API of TP-Link Archer AX21 Wi-Fi routers. This vulnerability may be accessed via the online administration interface. During the Pwn2Own Toronto event, Team Viettel, Qrious Security, and Tenable discovered a flaw that enables attackers to exploit a race condition vulnerability linked to iptable handling, which in turn enables them to obtain code execution. The bug was published by the aforementioned companies. In March, TP-Link issued a firmware update that addressed this and other vulnerabilities, just before it was discovered that attack attempts were being made in the wild. The failure of the locale API, which is responsible for managing the language settings of the router and does not evaluate or filter the information that it receives, to perform input sanitization is the root cause of the issue. This gives remote attackers the ability to insert commands into the device that should be carried out.
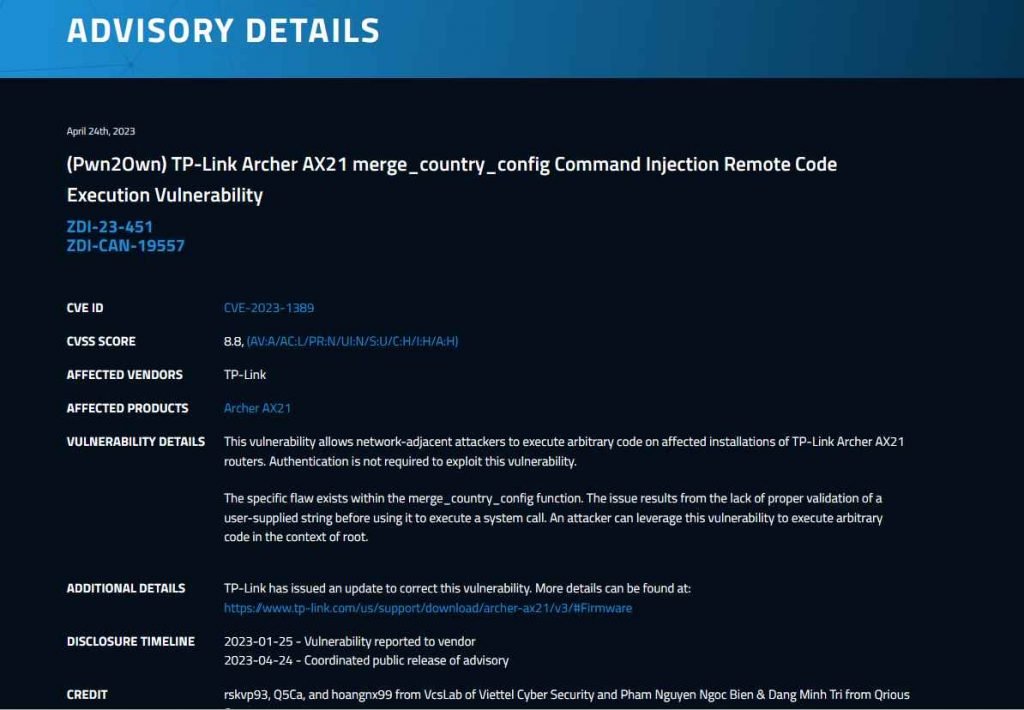
The vulnerability may be exploited by hackers by first submitting a specially constructed request to the router that includes a command payload as part of the country parameter, and then sending a second request that triggers the execution of the command. Hackers can exploit the weakness by sending the requests in the correct order.
On April 11, 2023, researchers saw the first symptoms of a vulnerability being used in the wild, and they have since found evidence of malevolent behavior all around the world. According to ZDI’s findings, a recently released variant of the Mirai virus botnet now takes use of the vulnerability in order to obtain access to the device. After that, it will download the malware payload that is tailored specifically for the architecture of the router in order to include it into its botnet.
This specific version of Mirai is designed to perform distributed denial of service (DDoS) assaults, and its characteristics suggest that its primary target is gaming servers. For example, it has the capability to launch attacks against the Valve Source Engine (VSE). After gathering these payloads, a brute-force search is conducted to locate the one that is suitable for the architecture of the target system. After the installation, the host immediately gets completely infected and starts a connection with the Mirai C2 server. The payloads were analyzed, and the results showed that the attackers encrypt strings by utilizing 0x00 and 0x22 as XOR keys. Once the strings were decrypted, they disclosed the attack functionalities and configuration parameters for the Mirai bot.
The quickness with which CVE-2023-1389 was exploited by the Mirai botnet highlights the lowering “time-to-exploit” pace that has been witnessed in the cybersecurity field. To keep their footing in organizational networks, threat actors are eager to take advantage of newly found vulnerabilities, particularly in IoT devices. This quick reaction highlights how important it is to apply patches in a timely manner in order to guard against dangers of this kind.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











