A new piece of malware known as Atomic macOS Stealer (AMOS) was recently discovered by researchers as it was being offered for sale on Telegram. The threat actor who is promoting it charges $1,000 each month and continually updates the virus that they are selling. The Atomic macOS Stealer is capable of stealing a variety of information from the computer of the victim, such as passwords saved in the Keychain, comprehensive system information, files from the victim’s desktop and documents folder, and even the macOS password itself.
One of its many capabilities is the extraction of data from web browsers and cryptocurrency wallets such as Atomic, Binance, Coinomi, Electrum, and Exodus. This is only one of its many functions. When a threat actor purchases the stealer from the creators of the stealer, they are also given a web panel that is pre-configured and ready to use for managing the victims.
In the event that AMOS is installed, it has the potential to compromise a broad range of data, some of which include the passwords for iCloud Keychain, the password for the macOS system, cookies, passwords, and credit card credentials from browsers like as Chrome, Firefox, Brave, Edge, and Opera, among others. Additionally, it has the ability to compromise cryptocurrency wallets such as Atomic, Binance, Exodus, Electrum, MetaMask, and a great number of others.
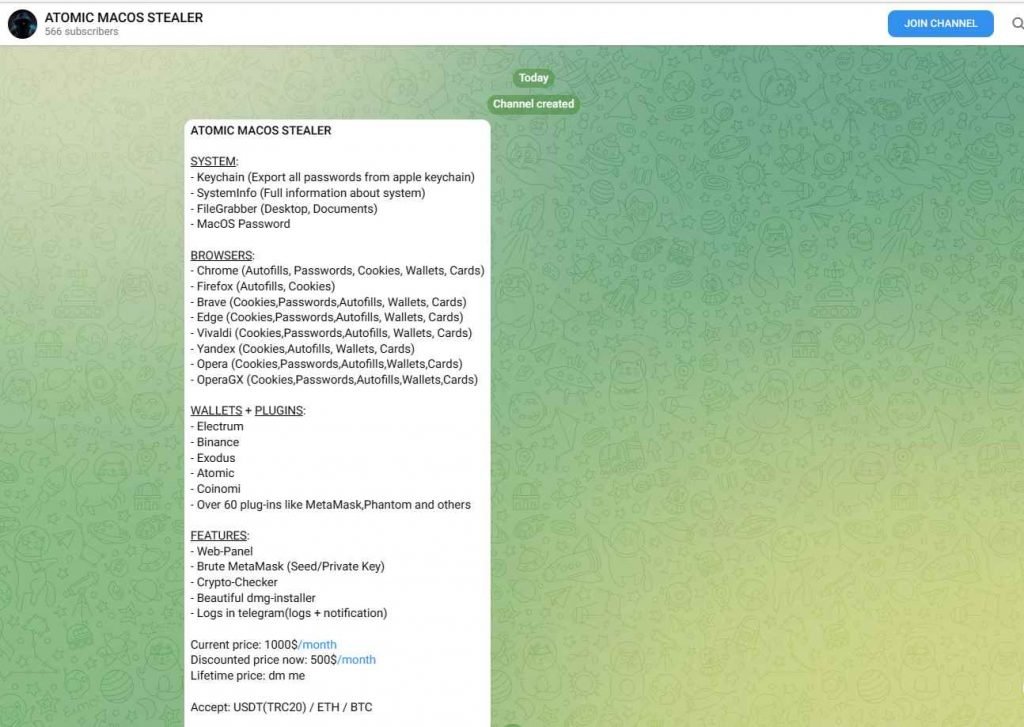
A web panel, a program called Brute MetaMask, logs in Telegram with alerts, and more features are provided to customers by the malicious party that is offering malware as a service.
The following is the message that the threat actor posted on Telegram while trying to sell the malware:
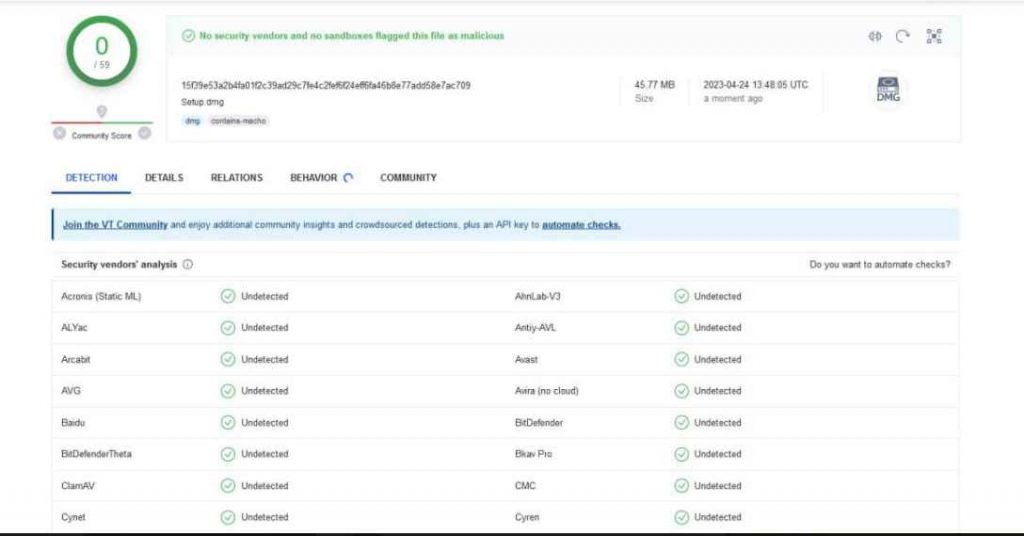
After the malware has gained access to a user’s information, it places the information into a ZIP file, compresses it, and then sends it to the malicious party via a command and control server URL.
It is imperative that users only download and install software from trusted sources, enable two-factor authentication, review app permissions, and refrain from opening suspicious links received via email or SMS messages as a result of this development, which is another sign that macOS is increasingly becoming a lucrative target beyond nation-state hacking groups to deploy stealer malware. The development is also a sign that macOS is becoming a target for cybercriminals to deploy stealer malware.
To protect against it:
Only applications from the official Apple App Store should be downloaded and installed on your device.
Install an antivirus and internet security software package that has a good reputation on your computer.
Make sure to use secure passwords, and implement multi-factor authentication whenever it’s possible.
When it is feasible to do so, enable the biometric security capabilities of the device, such as fingerprint or face recognition, so that it can be unlocked.
Always use caution before clicking on any links that are delivered to you in emails.
When enabling any permissions, exercise extreme caution.
Make that all of your software, including operating systems and apps, is up to date.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











