The most important routing protocol for the internet is called BGP. It makes it possible for autonomous systems (ASes), which are groups of IP addresses that are leased to an organization for a certain period of time by a registrar, to share routing and reachability information with one another.
When BGP stops working, an autonomous system (AS) could become inaccessible because other ASs are unable to route their packets to it. As a result, the unreachable AS is severed from the rest of the internet. When BGP is exploited by threat actors, network traffic may be redirected via sites that were not intended for it to go through.
Due to the fact that BGP was not originally created with security in mind, there are interruptions of routing on the internet that may be either inadvertent or deliberate. It has been known for a very long time that the original BGP had several flaws that might result in big events and internet outages. For example, in a situation that occurred in 2018, traffic destined for IP addresses associated with Google was redirected via China Telecom for more than an hour. The Russian Internet service provider Rostelecom made an announcement about routes for sections of Apple’s network in July 2022. As a consequence, it is possible that connections to Apple’s services will be rerouted via Russia for more than 12 hours. Using manual analysis and fuzzing, experts investigated seven widely used BGP implementations, three of which were open source (FRRouting, BIRD, and OpenBGPd), and four of which were closed source (Mikrotik RouterOS, Juniper JunOS, Cisco IOS, and Arista EOS).
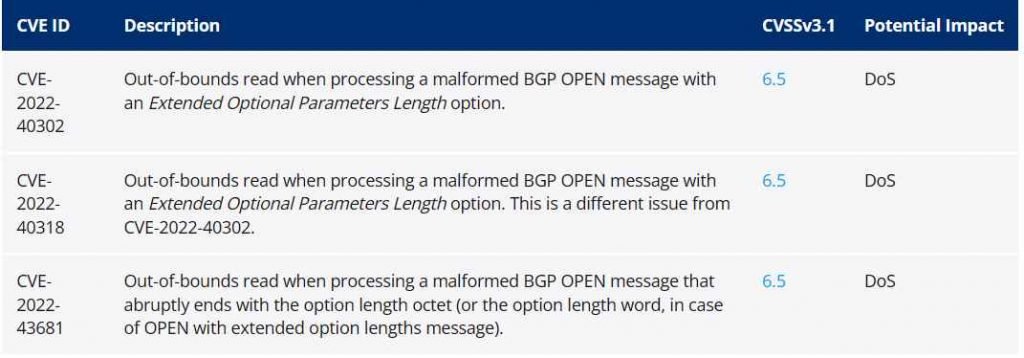
The most recent release of Free Range Routing (FRRouting) at the time was version 8.4, which was published on November 7, 2022. They discovered three new vulnerabilities in this release. The table that follows provides a summary of the flaws that may be exploited. The problems were brought to the attention of the FRRouting team, who then corrected them. The flaws “could be exploited by attackers to achieve a DoS condition on vulnerable BGP peers,” which would result in the peer losing all BGP sessions and routing tables and being unable to respond.
As part of this study, they will be providing an open-source tool that will allow enterprises to evaluate the security of the BGP suites that they use internally, as well as a tool for researchers to utilize to uncover new vulnerabilities in BGP implementations.
The tool is pre-loaded with a number of scripts that demonstrate the vulnerabilities we discovered and provide test cases for the BGP OPEN, UPDATE, ROTE REFRESH, and NOTIFICATION messages. These scripts are accessible immediately after the tool is installed. While the proofs of concept can be executed directly against a device to determine if it contains a vulnerability, the test cases can be executed against new implementations to look for vulnerabilities.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











