Researchers from Unit 42 discovered a Mirai version known as IZ1H9 that exploited many vulnerabilities in order to propagate itself. The following vulnerabilities are exploited by the threat actors to attack unprotected Linux servers and networking devices running the operating system:
Tenda G103 command injection vulnerability, referred to as CVE-2023-27076
LB-Link command injection vulnerability, also known as CVE-2023-26801
CVE-2023-26802: DCN DCBI-Netlog-LAB remote code execution vulnerability
Zyxel remote code execution vulnerability
Devices that have been compromised might be completely controlled by the attackers who exploited them and become a member of the botnet. These devices have the potential to be used in the commission of further attacks, such as distributed denial-of-service (DDoS) attacks. IZ1H9 presents a significant risk since it exploits many vulnerabilities and can take complete control of affected devices, which then become a member of its botnet. Since November 2021, when it was first seen in the wild, the Mirai IZ1H9 version has been tied to a number of different initiatives. These activities are most likely the workmanship of a single threat actor, as shown by crucial signs such as similar malware shell script downloaders, same XOR decryption keys, and identical function use.

On April 10, 2023, researchers discovered strange traffic that pointed towards a shell script downloader called ‘lb.sh’ and originated from a certain IP. In the event that it was successfully performed, the downloader would first clear the logs, hiding the operations it had been doing, and then it would download bot clients that were customized to work with a variety of Linux architectures. In the last step, it alters the iptable rules of the device, which causes network connections from many ports to become disrupted. Victims will have a harder time recovering remote devices as a result of this strategy.
After doing more research, it turned out that there were two other URLs online that had shell script downloaders. These downloaders had botnet clients that communicated with a command and control (C2) server as well as other URLs that hosted shell scripts. It was observed that the shell script downloaders were downloading botnet clients from a predetermined set of places and making contact with several C2 domains.
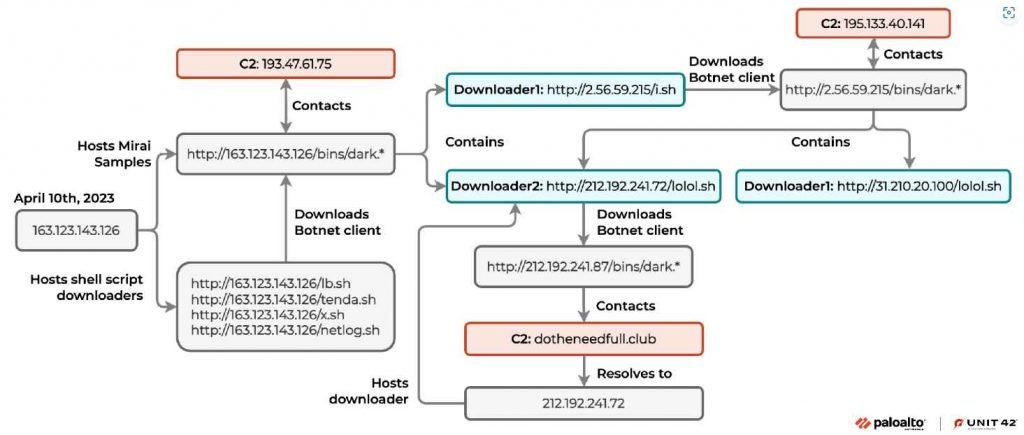
After doing an analysis on the samples that were downloaded, the researchers came to the conclusion that they constituted a subtype of the Mirai botnet known as IZ1H9. Since its discovery in August of 2018, IZ1H9 has gained a lot of attention and continues to be one of the most active Mirai variations. IZ1H9, like the original Mirai, avoids execution for a range of IP blocks, kills other botnet processes, and tries connection to a hardcoded C2 address. This is only one of the numerous similarities between the two variants.
Remote code execution attacks continue to be the most prevalent and most worrying dangers that afflict linux servers and IoT devices. IoT devices have long been a profitable target for threat actors. Devices that are susceptible to attack and are left exposed might result in major danger.
Even if the vulnerabilities that are being exploited by this threat are not as difficult to exploit, their effect is not diminished since they may still result in remote code execution. Once the attacker has gained control of a susceptible device, they are able to add that device and any others that have been hacked to their botnet. This enables them to carry out further attacks, such as a distributed denial of service.
It is strongly suggested that patches and updates be deployed whenever they can be in order to protect against this hazard.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











