The Federal Bureau of Investigation (FBI) has issued a warning about an emerging pattern in which bad actors are increasingly producing deepfake video in order to carry out sextortion attacks.
Threatening to make sexually explicit images or films of a victim public or share them with the victim’s family and friends is an example of sextortion, which may be a violation of many federal criminal laws. Sextortion is a kind of coercion in which victims are forced to provide sexually explicit photos or videos of themselves. The urge to consume more unlawful material, the pursuit of financial gain, or the intent to intimidate and harass others are the primary drivers behind this behavior. For the goal of extorting victims for ransom or gaining cooperation for other requests (such as giving nude images), malicious actors have been known to exploit photos or films that have been digitally altered.
As of April 2023, the FBI has seen an increase in the number of sextortion victims reporting the usage of phony photographs or videos made from material placed on their social networking sites or online posts, supplied to the malicious actor upon request, or caught while they were participating in video chats. According to recent reports from victims, the malicious actors often asked either: 1. Payment (such as money or gift cards) along with threats to disclose the photographs or films with family members or friends from social media if the funds were not received; or 2. That the victim submit genuine sexually-themed images or videos. The Federal Bureau of Investigation is issuing a warning to the general public about criminal actors who are producing synthetic material (often known as “deepfakes”) by modifying innocent images or videos in order to target victims. Content production that is facilitated by artificial intelligence (AI) is seeing ongoing improvements in terms of quality, customizability, and accessibility as a result of developments in technology.
The FBI continues to receive complaints from victims, including underage children and people who did not provide their permission, whose images or videos were changed to include obscene information. Among the victims are individuals who did not give their consent. The images or films are then uploaded to social media or pornographic websites where they are made available to the public with the intention of tormenting victims or extorting money from them.
To create sexually-themed images that appear true-to-life in likeness to a victim, malicious actors use content manipulation technologies and services to exploit photos and videos, which are typically captured from an individual’s social media account, open internet, or requested from the victim. These images are then circulated on social media, public forums, or pornographic websites. Before it was brought to their knowledge by another person, many victims, including juveniles, were unaware that their photographs had been stolen, modified, and distributed. The photographs are then delivered directly to the victims by the malicious actors for the purposes of sextortion or harassment, or until it was found by the victims themselves on the internet. After the material has been disseminated, victims may encounter considerable obstacles when attempting to stop further distribution of the modified information or remove it from the internet.
When it comes to uploading or direct messaging personal images, videos, and identifying information on social media platforms, dating apps, and other internet sites, the FBI strongly advises the general public to exercise extreme care. Even though they seem to have no malevolent intent when they are uploaded or shared, the photographs and videos may give criminals with a vast supply of material that they can use in their illegal endeavors. New options for malicious actors to discover and target victims have presented themselves as a result of advancements in content production technologies and the accessibility of personal photographs online. Because of this, they are susceptible to being humiliated, harassed, extorted, suffering financial loss, or being repeatedly victimized over an extended period of time.
What you can do to prevent Sextortion
The Federal Bureau of Investigation (FBI) encourages members of the general public to take into consideration the following when uploading material (such as images and videos) or interacting with persons online:
- Keep an eye on what your kids are doing online and talk to them about the potential dangers of revealing personal information.
- When publishing pictures, videos, and other personal stuff online, especially if it includes children or their information, use caution. This is especially important.
- Images, videos, or personal information that you share online may be collected, modified, and circulated by malevolent actors without your knowledge or agreement. This can happen even if you don’t post the content yourself.
- It may be exceedingly difficult, if not impossible, to delete anything after it has been disseminated or uploaded by other parties on the internet once it has already been shared on the internet.
- Conducting regular online searches of your and your children’s information (such as full name, address, phone number, and so on) might assist you in determining the extent to which personal information has been divulged or distributed throughout the internet.
- If you want to restrict the amount of people who can see your images, videos, and other personal information, you should adjust the privacy settings on your social media accounts. This should include making your profiles and friend lists private.
- It is a good idea to look into utilizing reverse image search engines in order to find any photographs or movies that may have been shared without your knowledge on the internet.
- You should exercise extreme care before accepting friend requests from someone you do not personally know, chatting with them, participating in video talks with them, or sending them photographs. Be particularly aware of those who ask you for anything right away or put pressure on you to give it to them. These things have the potential to have your screen captured, recorded, modified, and shared without your knowledge or agreement in order to exploit you or someone you know.
- Do not provide money or other valuable stuff to somebody who you do not know very well or who is unfamiliar with you. Even if you comply with malevolent actors, there is no assurance that your private images or other material will not be distributed.
- When communicating with known persons online who seem to be behaving in a manner that is inconsistent with their typical pattern of conduct, use caution. Accounts that have been hacked may be readily used by hostile actors in order to acquire the confidence of friends or connections for the purpose of furthering illegal plans or activities.
- Protect your accounts on social networking platforms and elsewhere online by using difficult passwords or passphrases and enabling multi-factor authentication.
- Before uploading and sharing photographs, videos, or any other personally identifiable material, it is important to do research on the privacy, data sharing, and data retention policies of social media platforms, apps, and websites.
- When it comes to uploading or direct messaging personal images, videos, and identifying information on social media platforms, dating apps, and other internet sites, the FBI strongly advises the general public to exercise extreme care.
Even though they seem to have no malevolent intent when they are uploaded or shared, the photographs and videos may give criminals with a vast supply of material that they can use in their illegal endeavors. New options for malicious actors to discover and target victims have presented themselves as a result of advancements in content production technologies and the accessibility of personal photographs online. Because of this, they are susceptible to being humiliated, harassed, extorted, suffering financial loss, or being repeatedly victimized over an extended period of time.
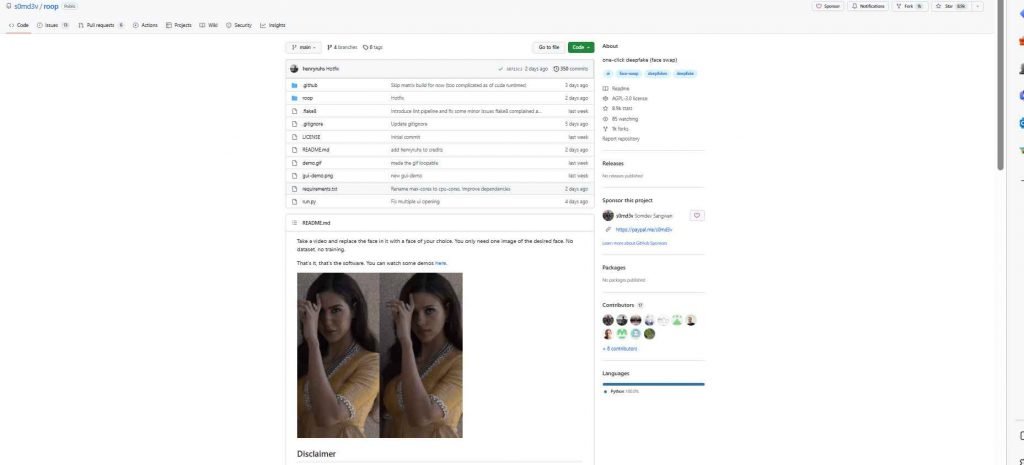
How Easy is to generated Porn video fo Someone
There are several projects for content generation tools that are accessible for free on GitHub. Some of these projects, like this one, can make convincing films using only a single shot of the target’s face and do not need any extra training or dataset.
What You can do if Sextortion happens to you
Take It Down is a free service offered by the National Center for Missing and Exploited Children that helps victims, who are in possession of the image or video files, remove or stop the online sharing of content that was taken while the victim was under the age of 18, including content that is nude, partially nude, or sexually explicit. This content was taken while the victim was under the age of 18. To get further details, please go to https://takeitdown.ncmec.org.
Keep track of any and all information pertaining to the occurrence (such as usernames, email addresses, websites or names of platforms used for communication, photographs, videos, and so on) and promptly report it to the following entities if you have reason to suspect that you have been the victim of a crime committed using these methods:
- The Internet Crime Complaint Center of the FBI may be accessed at www.ic3.gov.
- Contact your local FBI Field Office by calling 1-800-CALL-FBI (225-5324) or visiting www.fbi.gov/contact-us/field-offices.
- Call 1-800-THE-LOST or visit www.cybertipline.org to reach the National Center for Missing and Exploited Children.
- If these crimes are reported, it may assist law enforcement in identifying those responsible for them and prevent additional victims.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











