An intruder might utilize a security hole in the Android App Pin feature to make illegal purchases using Google Wallet if they are determined enough to do so. Because of the vulnerability, an attacker is able to access the whole card number as well as the expiration date from a device that is locked. To take advantage of the vulnerability identified as CVE-2023-35671, an attacker would need physical access to the device belonging to the victim. After that, they would have to put the gadget in App Pin mode and hold it close to an NFC scanner. After the data from the card has been read, the perpetrator may use it to make an unlawful payment.
Tiziano Marra, an ethical hacker, was the one who discovered the vulnerability. This vulnerability, which has been assigned the identifier CVE-2023-35671, is not your typical security flaw. An information disclosure flaw, sometimes known as a ticking time bomb, is at the core of the issue, and it ultimately results in a logic mistake. What are the possible repercussions? It provides a pernicious capacity to an attacker to gather the whole card number as well as the expiry data of the card.
The Android App Pin feature is where the vulnerability may be accessed once it has already been exploited.Android app pinning was first referred to as’screen pinning’ when it was first introduced with Android 5.0 Lollipop (API level 21) on November 12, 2014. On Android smartphones, this powerful security feature improves the user’s ability to regulate their privacy and protect their data.
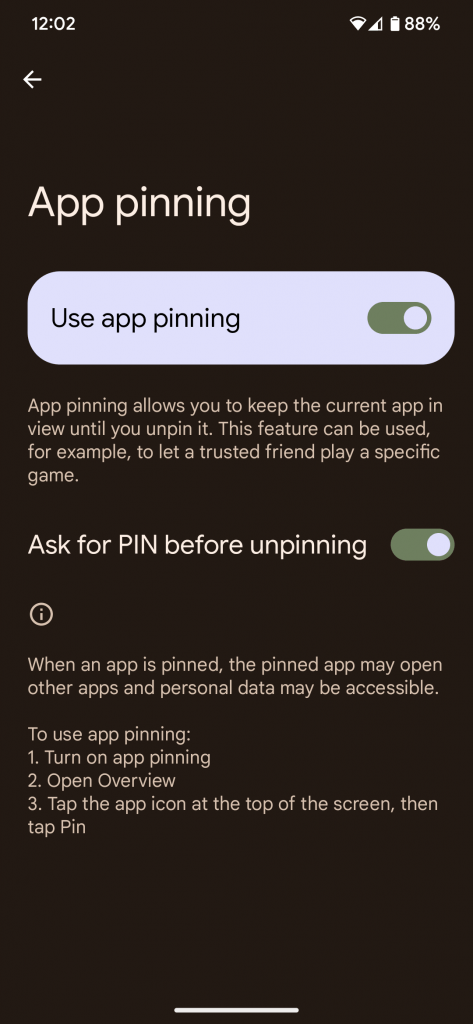
Users are given the ability to restrict their mobile device to a single program via the use of a feature known as “app pinning,” which effectively restricts their access to other apps and sensitive data. This capability proved to be quite useful in situations where keeping a highly concentrated work environment, dealing with public terminals, or sharing a device were all necessary requirements. When this is done, it stops unauthorized users from accessing personal data, programs, and settings, which contributes to an overall more secure digital experience.
The following procedures are often included when implementing app pinning as a method of application management:
Users may enable this feature by going to the Settings menu on their smartphone and selecting the Security and Privacy menu followed by the More Security Settings menu and then selecting the App Pinning option. After it has been enabled, users will be able to choose whatever app they want to pin.
Launching the chosen application is the first step in the pinning process, which allows users to enter pinned mode. This operation will permanently lock the device within the user interface of the chosen app.
When using the pinned mode, you won’t be able to interact with any other applications since they will be momentarily hidden from view. If you try to move to another app, access notifications, or perform any other function while the pinned app is open, the device will remind you that you are in the wrong app and keep you there.
Exiting Pinned Mode Users often need to give an extra layer of authentication in order to quit this mode. This may take the form of inputting a pre-set PIN, pattern, or password, or it can be accomplished via the use of biometric recognition (such as fingerprints or face recognition). Because of this additional degree of security, only users who are permitted to do so are able to exit the pinned app environment.
Pinning an Android app has many advantages, including the following:
Pinned mode protects users’ privacy and security by preventing unwanted access to private information, data, and programs that are deemed particularly sensitive.
Public Terminals: App pinning is important in scenarios like kiosks or shared devices since it confines users to a single program, hence decreasing the danger of illegal access and data exposure. This may be accomplished by pinning the application to the home screen of the device.
Focus and Productivity: Users may establish focused work environments by restricting the capabilities of their device to a single application that is task-oriented. This can increase their level of productivity.
Pinning an app to the home screen allows parents to limit their children’s access to just those games and programs that are suitable for their age or those that are instructive.
In a nutshell, Android app pinning, which was formerly referred to as “screen pinning,” was launched with Android 5.0 Lollipop and offers comprehensive control over the functionality and access of the device. It provides increased security, privacy, and focused interaction with digital information by designating a certain app as the one that may be used and needing authentication in order to leave that mode.
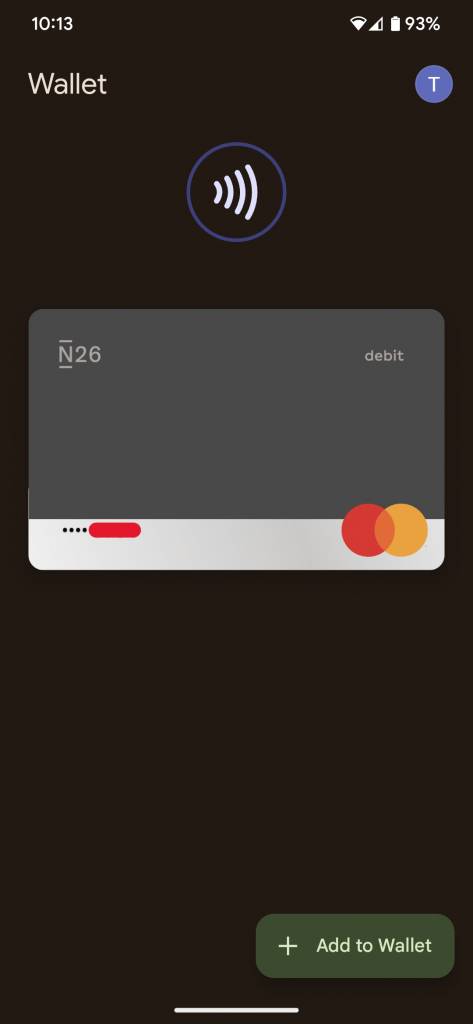

There is a logic mistake in the code that makes it possible for a general purpose NFC reader to read the whole card number and expiration data even while the screen on the device is locked. This problem can be found in the HostEmulationManager.java file, which is located in the onHostEmulationData section. This might result in the leaking of local information without the need of any extra execution rights. Exploitation may occur without the participation of the user.
According to Google’s calculations, the severity of this vulnerability is rather high.Along with his discoveries, the hacker was kind enough to submit a proof-of-concept attack, which brought attention to the seriousness of this high-severity vulnerability.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











