Within the expansive domain of collaboration tools, Atlassian’s Bitbucket and Confluence emerge as prominent figures, bestowing their enabling capabilities onto many developers and teams worldwide. Nevertheless, similar to other formidable entities, these platforms are not immune to possible risks. In recent times, a few vulnerabilities of significant severity have emerged, eliciting a sense of apprehension throughout the Atlassian community.
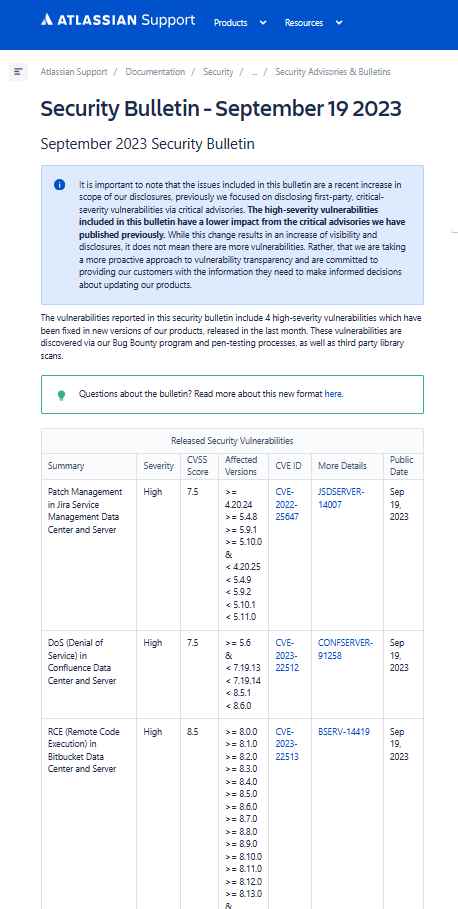
The potential risk present inside the Bitbucket Data Center and Server is not an ordinary one. The vulnerability, identified as CVE-2023-22513, is classified as high-severity due to its CVSS score of 8.5. It allows for Remote Code Execution (RCE) and can be traced back to version 8.0.0.
A perpetrator who has successfully authenticated himself and is abusing this vulnerability has the ability to execute arbitrary code, which might result in severe and perhaps catastrophic outcomes. It exhibits the combination of three significant effects, namely secrecy, integrity, and availability, without requiring any kind of user engagement.
Fortunately, the susceptibility was identified by a diligent individual user, as a result of Atlassian’s Bug Bounty initiative.
Atlassian has promptly responded by giving a strong recommendation for customers to update to the most recent version. In the event that you are unable of doing the task, it is recommended that you enhance your instance by upgrading it to one of the officially designated approved fixed versions.
The vulnerability identified as CVE-2023-22512 pertains to a Denial of Service (DoS) attack that may be exploited in Confluence Data Center and Server.
The Denial of Service (DoS) vulnerability has been present in Confluence Data Center and Server starting with its 5.6 version. The vulnerability identified as CVE-2023-22512, with a CVSS score of 7.5, does not compromise the confidentiality or integrity of the system. However, it targets the aspect that is most vulnerable.
The presence of this vulnerability enables an unauthorized attacker to exploit it, resulting in the disruption of a network-connected Confluence instance, either momentarily or forever. It may be likened to an imperceptible force that depletes one’s available resources.
Once again, a member of the Bug Bounty program played the role of a vigilant observer who identified and reported this vulnerability.
Atlassian recommends that those who are enthusiastic about Confluence promptly switch to the most recent version. For those seeking temporary remedies, it is recommended to consider implementing required version updates. In the event that you are unable to do the task, it is recommended that you update your instance to one of the officially approved fixed versions as mentioned.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











