The research Sierra:21 – Living on the Edge” presents an analysis of vulnerabilities found in Sierra Wireless AirLink cellular routers, which are widely used in OT/IoT (Operational Technology/Internet of Things) environments to connect critical local networks to the Internet. Forescout Vedere Labs identified 21 new vulnerabilities in these routers, as well as in certain open-source components used in them, such as TinyXML and OpenNDS.
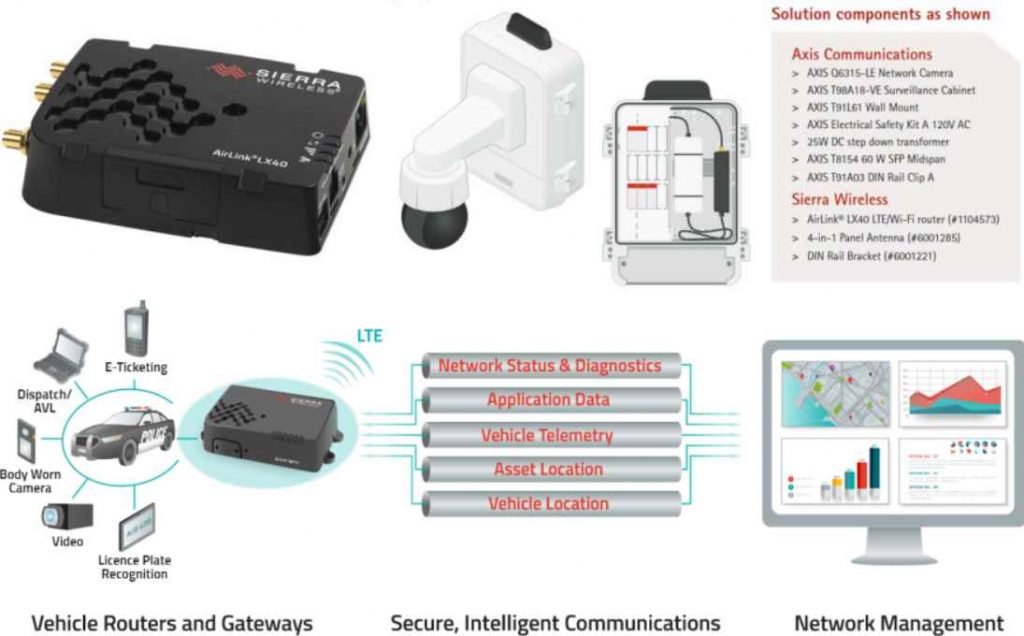
- The study focuses on the Sierra Wireless AirLink cellular routers, crucial for connecting OT/IoT networks to the internet.
- These routers are used in various critical infrastructure sectors, including manufacturing, healthcare, government, energy, transportation, and emergency services.
- Sierra Wireless, OpenNDS, and Nodogsplash have patched several vulnerabilities, but challenges remain due to the abandonment of projects like TinyXML.
Flaws and Examples
The vulnerabilities are grouped into five impact categories:
- Remote Code Execution (RCE): Attackers can take full control of a device by injecting malicious code.
- Cross-Site Scripting (XSS): This allows for the injection of malicious code on clients browsing the ACEmanager application, potentially leading to credential theft.
- Denial of Service (DoS): These vulnerabilities can be used to crash ACEmanager, rendering it unreachable or causing it to restart automatically.
- Unauthorized Access: This involves design flaws like hardcoded credentials and private keys, which could allow attackers to perform man-in-the-middle attacks or recover passwords.
- Authentication Bypasses: These allow attackers to bypass the authentication service of the captive portal and directly connect to the protected WiFi network.
Severity of Vulnerabilities: Among these 21 vulnerabilities, one is of critical severity, nine have high severity, and eleven have medium severity. These vulnerabilities could allow attackers to steal credentials, take control of a router by injecting malicious code, persist on the device, and use it as an initial access point into critical networks.
Affected Sectors: The affected devices are found in multiple critical infrastructure sectors. These include manufacturing, healthcare, government and commercial facilities, energy and power distribution, transportation, water and wastewater systems, retail, emergency services, and vehicle tracking. Additionally, these routers are used to stream video for remote surveillance and connect police vehicles to internal networks.
Extent of Exposure: Over 86,000 vulnerable routers are exposed online. Notably, less than 10% of these exposed routers have been confirmed to be patched against known vulnerabilities found since 2019, which indicates a large attack surface. Moreover, 90% of devices exposing a specific management interface (AT commands over Telnet) have reached the end of their life, meaning they cannot receive further patches.
Specific examples include:
- CVE-2023-40458: ACEmanager enters an infinite loop when parsing malformed XML documents, leading to DoS.
- CVE-2023-40459: A NULL-pointer dereference in ACEmanager during user authentication, leading to limited DoS.
- CVE-2023-40460: Attackers can upload HTML documents to replace legitimate web pages in ACEmanager, leading to XSS attacks.
- CVE-2023-40461 and CVE-2023-40462: Issues with uploading client certificates and client TLS keys in ACEmanager, enabling JavaScript code injection.
- CVE-2023-40463: Hardcoded hash of the root password in ALEOS, allowing unauthorized root access.
- CVE-2023-40464: Default SSL private key and certificate in ALEOS, enabling impersonation and traffic sniffing/spoofing.
Mitigation or Workaround
- Patching is essential. Sierra Wireless has released updated ALEOS versions containing fixes.
- Change default SSL certificates.
- Disable unnecessary services like captive portals, Telnet, and SSH.
- Deploy web application firewalls to protect against web-based vulnerabilities.
- Use OT/IoT-aware intrusion detection systems to monitor network connections.
Conclusion
- Vulnerabilities in OT/IoT network infrastructure are a major concern and are often left unpatched.
- Less than 10% of routers exposed online are patched against known vulnerabilities.
- Embedded devices lag in addressing vulnerabilities and implementing exploit mitigations.
- Incomplete fixes can lead to new issues, as seen with CVE-2023-40460, originating from an incomplete fix for a previous vulnerability.
- Manufacturers need to understand and address the root causes of vulnerabilities for effective long-term solutions.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











