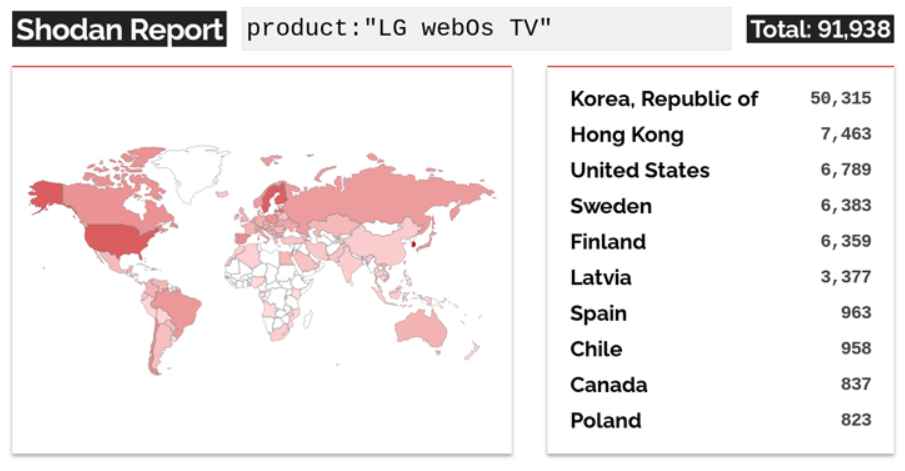
In a recent disclosure, cybersecurity firm Bitdefender has revealed a series of critical vulnerabilities within LG’s WebOS, the operating system used in many of the brand’s smart TVs. These vulnerabilities, affecting versions 4 through 7 of the OS, pose significant risks, ranging from unauthorized access and control over the devices to potential data breaches. Although the vulnerable service is intended for LAN access only, Shodan, the search engine for Internet-connected devices, identified over 91,000 devices that expose this service to the Internet. This comprehensive report provides an in-depth look at the vulnerabilities, their possible impacts, and the recommended measures for mitigation.
These vulnerabilities can be exploited to gain unauthorized access and control over the devices. Here’s a breakdown of each identified vulnerability with hypothetical examples to illustrate their potential exploits:
1. CVE-2023-6317: Authorization Mechanism Bypass
Description: This vulnerability allows an attacker to bypass the authorization mechanism of the WebOS. By setting a specific variable, an attacker can add an extra user to the TV set without proper authorization.
- Technical Mechanism: This vulnerability allows unauthorized users to bypass the PIN verification process required to create a new user account on the TV. It exploits a flawed implementation in the account management service, where a variable (
skipPrompt) is set to true if certain conditions are met, mistakenly granting account creation without the necessary user authentication. - Exploit Path: An attacker can send a specially crafted request that manipulates this variable by mimicking a legitimate user session, leading to the creation of a privileged user account without the owner’s consent.
Example: Suppose an attacker discovers that the WebOS service, which is only intended for LAN access, is exposed over the internet. The attacker crafts a request that exploits this service to set a variable that bypasses normal user authentication procedures, thus allowing them to add a new user with administrative privileges to the television without the owner’s knowledge.
2. CVE-2023-6318: Root Access Elevation
Description: Once initial access is gained via CVE-2023-6317, this vulnerability allows the attacker to elevate their access level to root, giving them full control over the device.
- Technical Mechanism: Following initial access through CVE-2023-6317, this vulnerability leverages another flaw in the system’s command handling routines. It involves an authenticated command injection vulnerability within a service method designed to process system analytics reports (
processAnalyticsReport). - Exploit Path: By manipulating the input parameters of this method, specifically the
reportFileparameter, attackers can insert arbitrary commands that the system executes with root privileges. This is possible because the input is not properly sanitized before being passed to system command functions.
Example: After adding themselves as a user on the TV, the attacker exploits a flaw in another service that escalates their privileges. By sending a specially crafted request to this service, they can execute commands as the root user, allowing them to install malicious software, access all files on the device, and manipulate the TV’s operation.
3. CVE-2023-6319: Operating System Command Injection
Description: This vulnerability involves manipulating a library responsible for displaying music lyrics, allowing an attacker to inject and execute arbitrary operating system commands.
- Technical Mechanism: This flaw allows command execution through the manipulation of a library used for displaying music lyrics. The vulnerability occurs when the lyrics file processing function does not properly sanitize the file path, allowing specially crafted files to execute arbitrary commands.
- Exploit Path: Attackers can upload a malicious MP3 file accompanied by a lyrics file crafted to contain executable commands. When the TV software attempts to display the lyrics, the embedded commands are executed, potentially giving the attacker control over the TV’s operating system.
Example: An attacker uploads a malicious MP3 file with a specially crafted lyrics file to the TV. The lyrics file contains commands wrapped in the metadata, which the TV processes without proper sanitation. When the lyrics are displayed, the embedded commands are executed, potentially giving the attacker the ability to perform actions such as turning on the TV’s microphone for eavesdropping.
4. CVE-2023-6320: Authenticated Command Injection via API
Description: This vulnerability allows an attacker to inject authenticated commands through the com.webos.service.connectionmanager/tv/setVlanStaticAddress API endpoint, which manipulates the network configuration without proper input validation.
- Technical Mechanism: This vulnerability is found in the
com.webos.service.connectionmanager/tv/setVlanStaticAddressAPI endpoint, which allows for network configuration changes. The flaw stems from inadequate input validation, permitting command injection through parameters intended for configuring network settings. - Exploit Path: With authenticated access (possibly gained through exploiting CVE-2023-6317), an attacker can inject commands into the
ip_address,bcast_address, andnetmaskparameters of this API endpoint. These commands are then executed by the system, allowing the attacker to alter network configurations or perform other unauthorized actions.
Example: Having gained authenticated access through previous exploits, the attacker uses this vulnerability to change the TV’s network settings, isolating it on a virtual LAN that routes all traffic through a server controlled by the attacker. This could be used to intercept sensitive information or serve as a pivot point for further attacks within the home network.
The identified vulnerabilities in LG’s WebOS affect multiple versions of the operating system, running on various LG TV models. Below is a table summarizing the affected versions and corresponding devices:
| WebOS Version | Model Numbers | Vulnerabilities Affected |
|---|---|---|
| 4.9.7 | LG43UM7000PLA | CVE-2023-6317, CVE-2023-6319 |
| 5.5.0 | OLED55CXPUA | CVE-2023-6317, CVE-2023-6318, CVE-2023-6319, CVE-2023-6320 |
| 6.3.3-442 | OLED48C1PUB | CVE-2023-6317, CVE-2023-6318, CVE-2023-6319, CVE-2023-6320 |
| 7.3.1-43 | OLED55A23LA | CVE-2023-6317, CVE-2023-6319 |
Explanation:
- WebOS 4.9.7 and 7.3.1-43 share similar vulnerabilities, primarily the authorization bypass and the operating system command injection via the music lyrics display mechanism.
- WebOS 5.5.0 and 6.3.3-442 are affected by all four disclosed vulnerabilities, making them the most at-risk versions, potentially due to having broader functionality that interacts with more system components or more complex network settings.
- The vulnerabilities span from basic authorization mechanism bypasses to more complex command injections that can give attackers deep access to the system.
Mitigation Measures for LG (Vendor)
- Patch Deployment:
- Immediate Updates: LG should release patches for the affected WebOS versions as soon as possible. These updates should fix the root causes of the vulnerabilities, such as improper input validation and inadequate authorization checks.
- Automatic Update Feature: Ensure that all WebOS devices are set to receive and install updates automatically, minimizing the window of vulnerability exposure.
- Enhanced Security Protocols:
- Review and Reinforce: LG should conduct a thorough review of all API endpoints and internal mechanisms for handling user inputs and authentication processes. This includes reinforcing the use of proper sanitization and validation techniques to prevent injection attacks.
- Secure Software Development Lifecycle (SDLC): Implement an SDLC with a strong focus on security, including regular code reviews, vulnerability assessments, and penetration testing.
- User Notification and Support:
- Transparent Communication: Proactively inform users about the vulnerabilities and the steps being taken to address them. Provide clear instructions on how to update their devices.
- Technical Support: Set up a dedicated helpline or online support system to assist users with the update process and to answer any security concerns.
Recommendations for Users
- Apply Updates Promptly:
- Check for Updates: Users should manually check for software updates on their LG TV if automatic updates are not enabled. Applying these updates is crucial in protecting their devices from exploits.
- Restart Devices: Ensure that the device is restarted after applying the update to enforce changes.
- Secure Network Configuration:
- Network Segmentation: Place IoT devices on a separate network segment, reducing the risk of an attacker pivoting from a compromised TV to more sensitive devices like personal computers or storage.
- Firewall and Router Settings: Configure firewalls and routers to block unnecessary inbound connections and limit what can be accessed from the smart TV.
- Increase Monitoring and Awareness:
- Monitor Network Traffic: Use network monitoring tools to detect unusual activities that could indicate exploitation attempts, such as unexpected outbound connections or high volumes of data transfer.
- Stay Informed: Regularly follow updates from LG and security researchers to stay informed about any new threats or patches.
Long-Term Security Enhancements
- Educational Campaigns:
- Security Awareness: LG could offer educational resources on the importance of cybersecurity and best practices for securing IoT devices.
- Workshops and Tutorials: Provide online tutorials or webinars that guide users on securing their home networks and understanding the security settings on their devices.
- Community Engagement:
- Bug Bounty Programs: Initiate or enhance bug bounty programs to encourage the ethical disclosure of new vulnerabilities by external researchers.
- Open Source Collaboration: Consider collaborating with the open-source community to allow external developers to contribute to the security robustness of WebOS.
By implementing these mitigation measures and recommendations, LG can help secure its devices against the identified vulnerabilities, while users can protect their home environments from potential breaches. This proactive approach is essential in building trust and ensuring the security of increasingly connected smart home ecosystems.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











