Introduction
Imagine scanning the LAN (Local Area Network) network with one command line. Now coming to this tool Null scan, it’s a Network scanning tool. We can use this tool for scanning the network and websites. This tool is built-in python language and this tool can be used in first stage of penetration testing.
Environment
- OS: Kali Linux 2019.3 64 bits
- Kernel version: 5.2.0
Installation Steps
- Type this command to clone the project.
- git clone https://github.com/noptrix/nullscan
root@kali:/home/iicybersecurity# git clone https://github.com/noptrix/nullscan Cloning into 'nullscan'... remote: Enumerating objects: 283, done. remote: Counting objects: 100% (283/283), done. remote: Compressing objects: 100% (159/159), done. remote: Total 283 (delta 133), reused 270 (delta 120), pack-reused 0 Receiving objects: 100% (283/283), 1.16 MiB | 131.00 KiB/s, done. Resolving deltas: 100% (133/133), done.
- Use the cd command to enter into the nullscan directory.
root@kali:/home/iicybersecurity# cd nullscan/ root@kali:/home/iicybersecurity/nullscan#
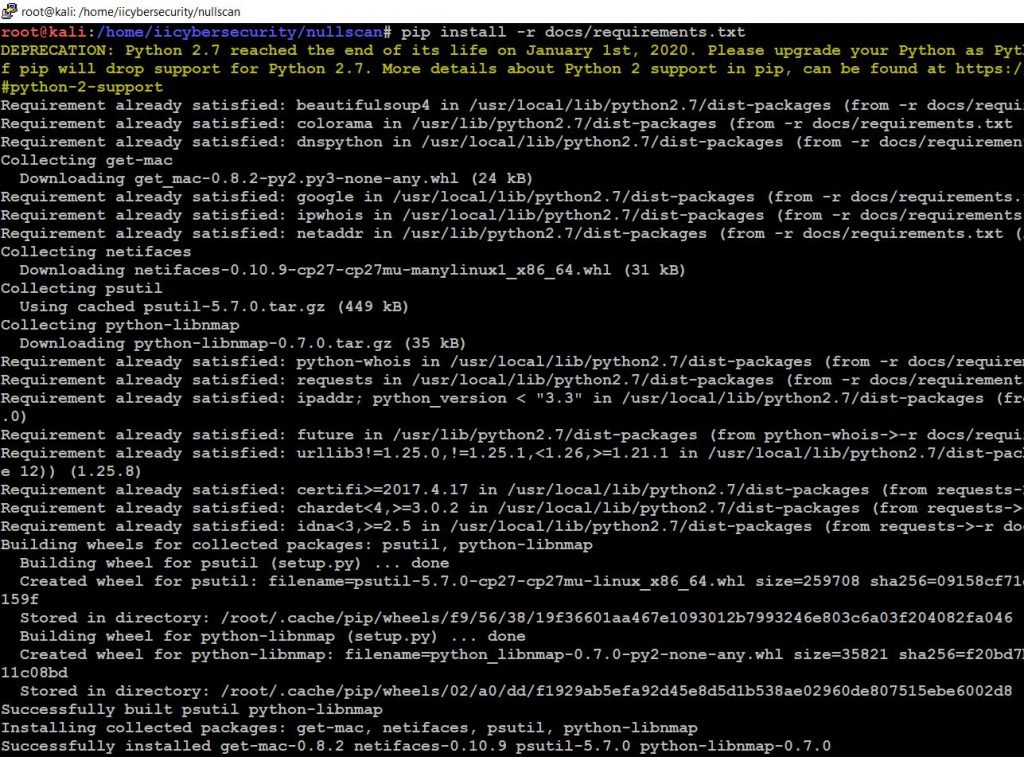
- Now, install the requirements by typing this command pip install -r docs/requirements.txt
- Use this command to give the permission to setup.sh file
- chmod +x setup.sh
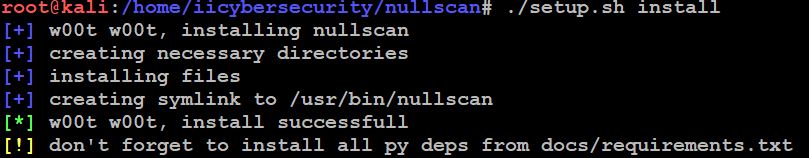
- Now use this command to install the tool
- ./setup.sh install
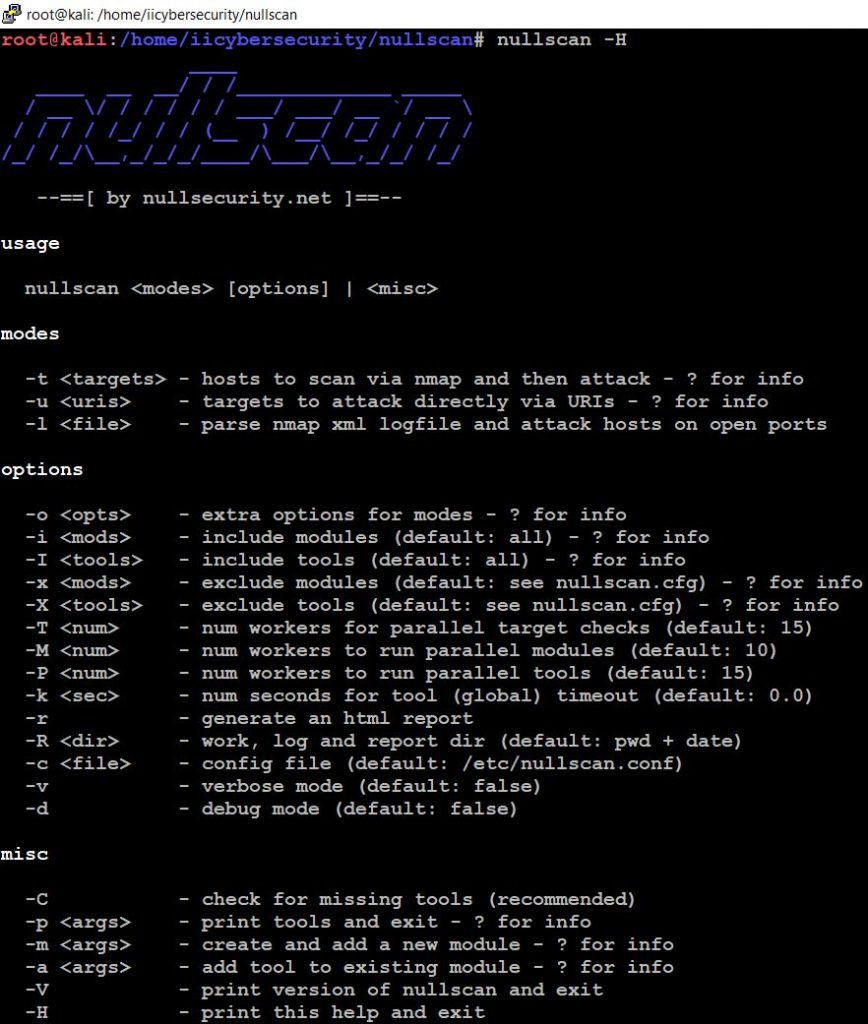
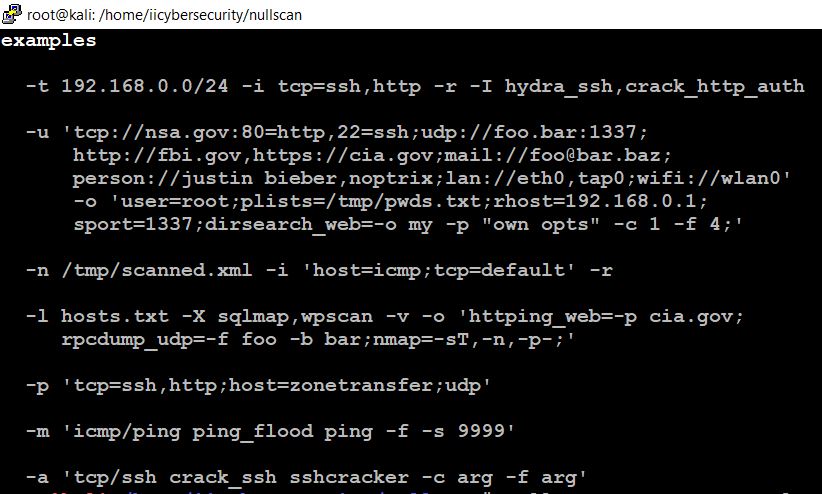
- Next, use this command to find the help options.
- nullscan -H
- Now, use this command to scan your LAN Network by specifying the range.
- nullscan -t ‘192.168.1.0/24’ -i ‘tcp=ssh,http’ -r -I ‘hydra_ssh,crack_http_auth’
- -t scan the network by using Nmap tool
- -i include modes
- -I include tools
- -r generate HTML Report
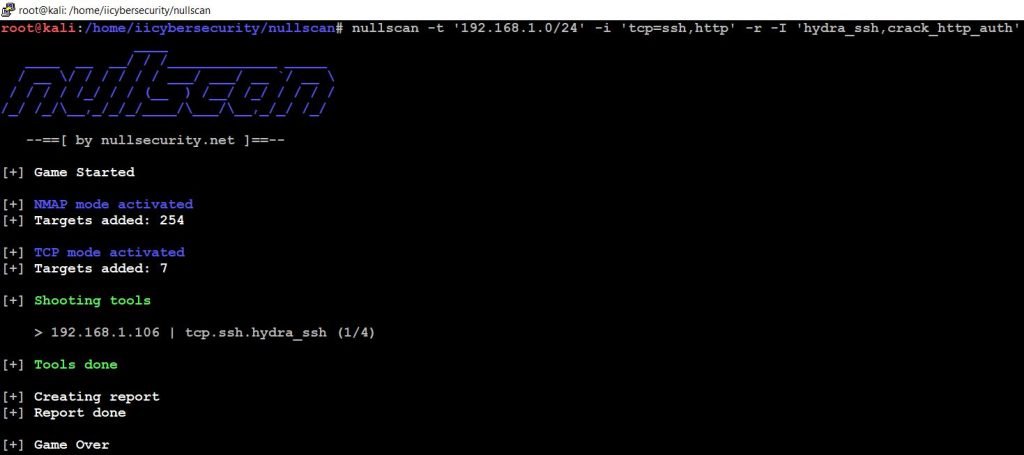
- Here scanning is completed using the Nmap tool, TCP modes and we can see the results in reports directory.
- Use the ls command to view the directory.
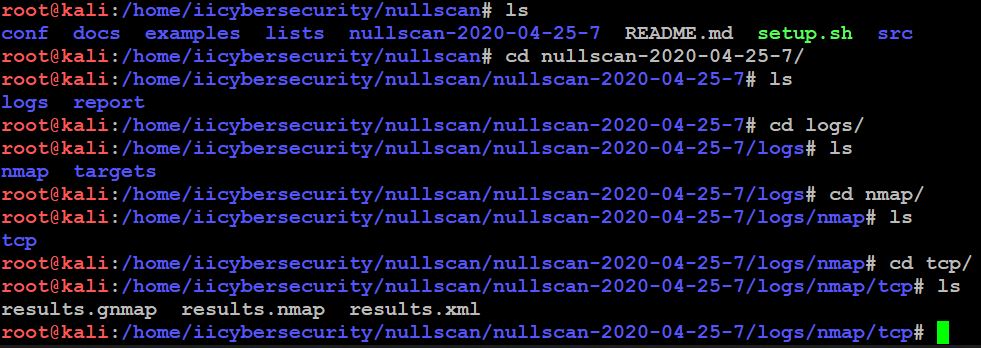
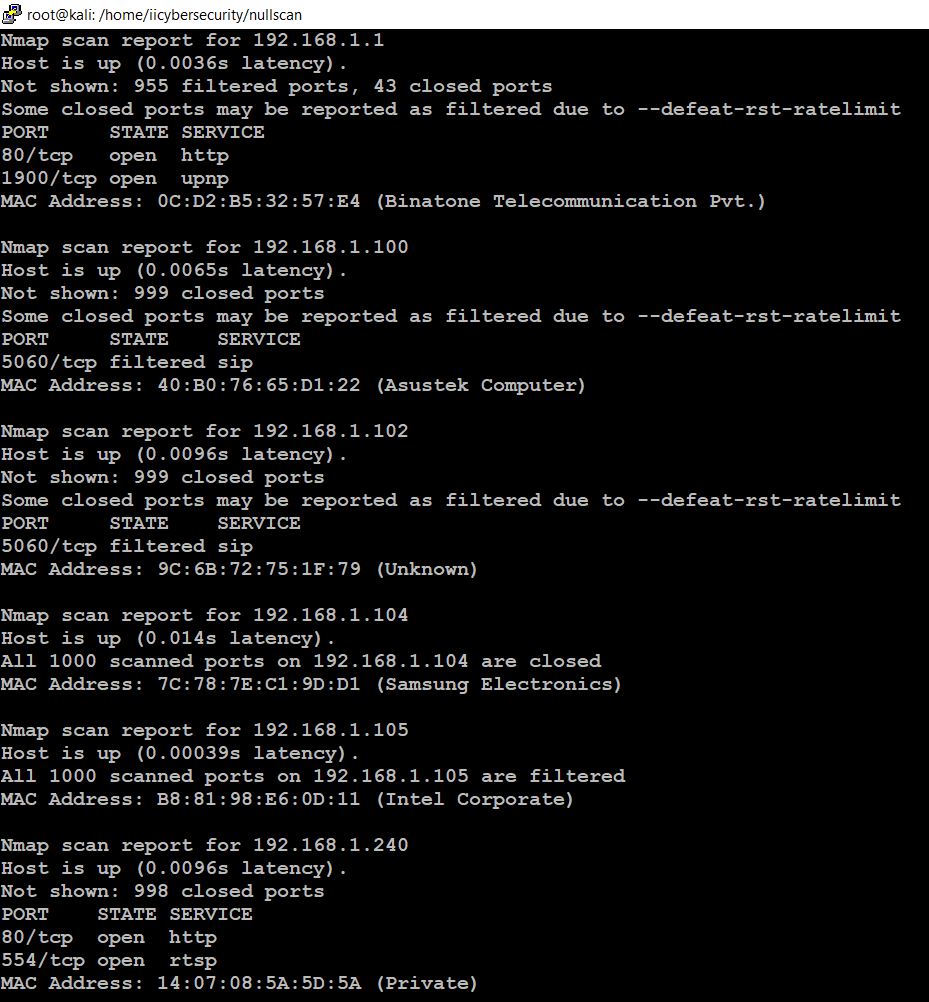
- This tool scans whole network range we specified and displays all open ports on all IP’s.
- In the above picture, we see results (results.gnmap, results.nmap, and results.xml)
- In the results.gnmap show all IPs in the LAN with their status and open ports.
URL Mode
- In this tool, we have URL mode.
- For testing, we will run DVWA as victim web server:
- For downloading DVWA iso go to: https://www.vulnhub.com/entry/damn-vulnerable-web-application-dvwa-107,43/
- After downloading iso, open iso in virtual box or vmware workstation. Then start iso.
- For getting DVWA ip type ifconfig, In our case IP was 192.168.1.108
- Now we will enter the target URL in NullScan. This mode scans the website and generates a report.
- Use this command to scan website running in DVWA.
- nullscan -u ‘http://192.168.1.108/’ -i ‘tcp=ssh,http’ -r -I ‘hydra_ssh,crack_http_auth’
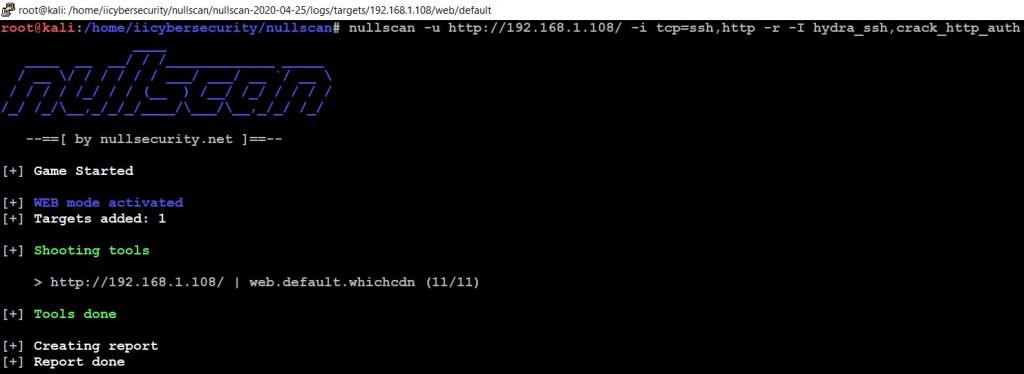
- Use ls command to view the report.
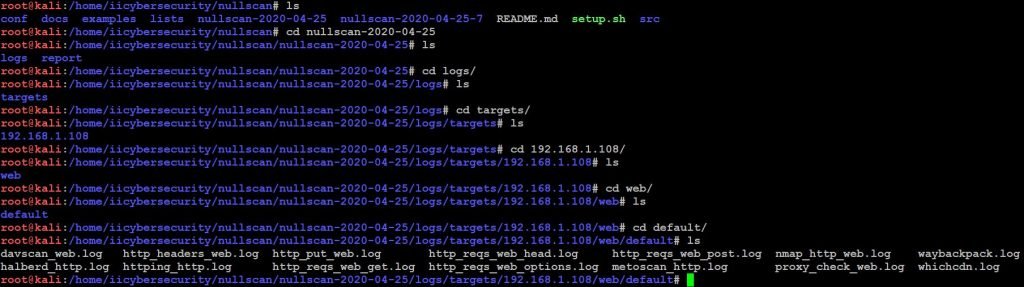
- It also generates an HTML report. There we can view the complete results.
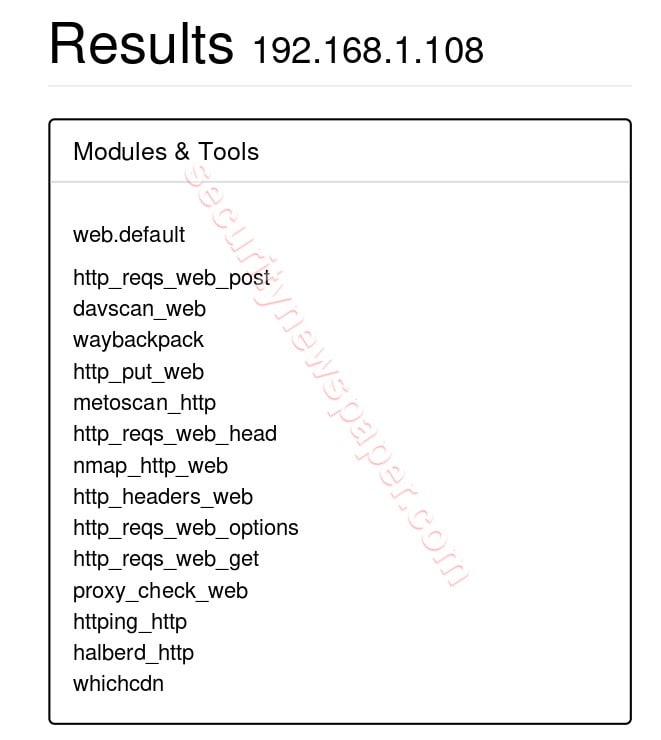
- Here, we see the complete web.default results with different modes.
- Now, we show some unique information about target web site
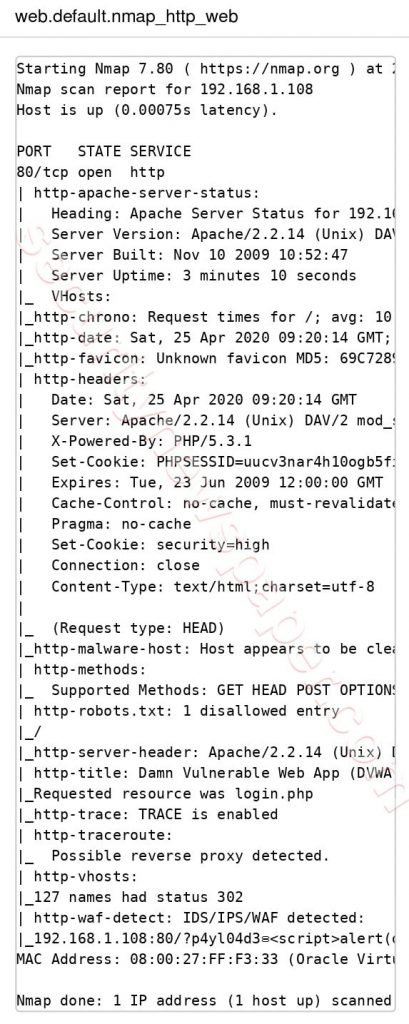
In the above picture we see some unique results of port status, services about the target.
Conclusion
This tool can scan Complete LAN network by using single command. This tool is quite useful for all IT Admin to quickly scan their network for vulnerabilities. We can execute this tool in less time with more results.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










