Cisco has revealed the finding of a vulnerability in the Java Remote Management Interface, of the Unified Contact Center Express (Unified CCX) product. According to cloud computing security specialists, exploiting this flaw could allow unauthenticated remote hackers to execute arbitrary code on the affected device.
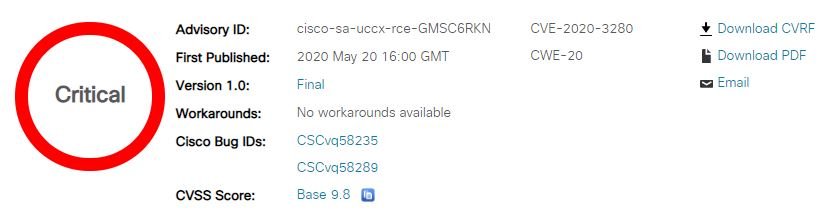
Tracked as CVE-2020-3280, this vulnerability received a score of 9.8/10 on the Common Vulnerability Scoring System (CVSS) scale, so it is considered a critical security flaw.
Apparently, the flaw exists due to unsafe deserialization of the content sent by the user of the affected software. A threat actor could exploit the vulnerability by sending a malicious serialized Java object to a specific listener on the affected system. Successful exploiting of the vulnerability would allow hackers to execute arbitrary code as root user on a target device. The company has confirmed that this vulnerability does not affect Cisco Unified Contact Center.
In response, Cisco released software updates to fix the vulnerability. Users of affected deployments will need to install the updates and wait for support for software versions and feature sets for license owners to be released, cloud computing security specialists mention.
In the table below, the left column lists Cisco software versions. The right column indicates whether a version is affected by the vulnerability described in this notice and the first version that includes the solution for this vulnerability. Administrators are encouraged to upgrade to an appropriate fixed software version as described in this section.

So far, cloud computing security experts on the Cisco Product Security Incident Response Team (PSIRT) have not detected any exploits linked to exploiting this vulnerability. Because there are no workarounds, users are strongly advised to install official updates to mitigate the risk of exploitation.
Although industrial activities in most of the world are experiencing uncertain times due to the pandemic, cybersecurity specialists have been working to mitigate the risks of cyberattacks against users of major technology deployments. For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










