In what is now considered the largest npm supply-chain compromise in history, attackers hijacked 18 widely used npm packages — including chalk, debug, ansi-styles, and strip-ansi — with a staggering 2.6 billion weekly downloads combined.
The attack unfolded after maintainer Josh Junon (qix) was phished into handing over his npm credentials. Using this access, the attackers published malicious package updates containing a crypto-stealing module that hooked into browser APIs and replaced wallet addresses during cryptocurrency transactions.
The compromise spread incredibly fast: within a two-hour window, malicious versions reached an estimated 10% of all cloud environments.
And yet, despite the scale and speed, the attackers walked away with less than $1,000 in profit.
Attack Anatomy
Initial Access — Maintainer Phishing
- Target: Josh Junon (qix), maintainer of popular npm projects.
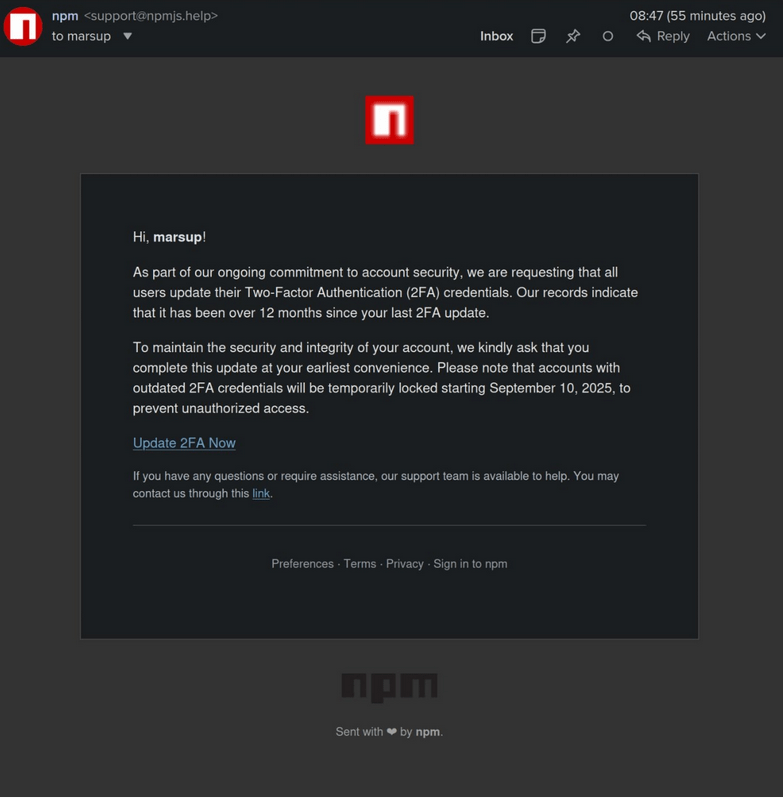
- Attack vector: Phishing email from a fake domain (
npmjs[.]help). - Lure: Threat of account lockout unless 2FA was updated.
- Credential exfiltration endpoint:
https://websocket-api2[.]publicvm.com/images/jpg-to-png.php - Once stolen, attackers had full control of Junon’s npm account.
Malicious Payload Injection
The attackers published compromised versions of 18 core packages, including:
chalk(300M weekly downloads)debug(357M)ansi-styles(371M)supports-color(287M)strip-ansi(261M)wrap-ansi(198M)- plus others (
color-convert,slice-ansi,simple-swizzle, etc.)
These packages are deeply embedded in the Node.js ecosystem, meaning virtually every project indirectly depends on them.
The Malware Logic
- Execution Context: Targeted browser environments (not backend Node.js servers).
- Hooks Installed:
window.fetchXMLHttpRequest- Web3 APIs:
window.ethereum, Solana wallet APIs
- Behavior:
- Intercepted outgoing crypto signing requests.
- Replaced wallet addresses with attacker-controlled addresses.
- Exfiltrated any captured transaction data.
Effectively, the payload acted as a silent man-in-the-browser crypto skimmer.
Propagation Speed
- Wiz analysis:
- 99% of monitored cloud environments used at least one affected package.
- In just two hours, malicious versions reached 10% of all cloud environments.
- This demonstrates how supply chain attacks propagate faster than traditional phishing or malware.
Impact Assessment
- Technical Spread: Massive — billions of downloads, 10% cloud penetration.
- Security Impact: Limited — payload too narrowly designed (crypto-browser interception only).
- Financial Gain:
- ~$429 in ETH
- ~$46 in SOL
- ~$20 in memecoins
- ~$100–200 across BTC/Tron/BCH/LTC
- Total ≈ $600–$1,000
Key irony: The attackers compromised the biggest npm packages ever but wrote a payload that was nearly useless for backend environments where those packages are most used.
Red-Team Style Exploitation Scenarios
Scenario 1 — Successful Backend Payload
If instead of targeting Web3 wallets, attackers had inserted a reverse shell or credential stealer, they could have:
- Exfiltrated AWS or GCP credentials from CI/CD environments.
- Moved laterally inside cloud infrastructure.
- Planted persistence via modified build pipelines.
Impact: Could have led to multi-cloud supply chain breaches at scale.
Scenario 2 — Lateral Supply Chain Infection
Malware could have installed secondary packages in node_modules, each publishing their own compromised updates.
- This would cascade malware across entire dependency trees, making removal much harder.
Scenario 3 — Silent Data Harvester
Instead of noisy crypto-jacking, attackers could have harvested:
- API keys in environment variables.
- Secrets in
.envfiles. - Tokens from cloud SDKs (AWS, Azure, GCP).
Impact: Stealthy long-term espionage instead of short-term profit.
Lessons Learned
- Open-source maintainers are high-value targets. A single phished maintainer can compromise the global supply chain.
- Propagation is nearly instantaneous. Hours, not days, separate compromise from global impact.
- Payload choice matters. Attackers failed not because of poor access, but because of poor payload design.
- The next attackers may not be so careless.
Mitigation Recommendations
For Developers
- Enable phishing-resistant 2FA (FIDO2 keys) on npm/GitHub accounts.
- Pin dependency versions (
package-lock.json) to prevent auto-pulling new releases. - Audit updates for unusual diffs or suspicious network calls.
- Delay critical package updates (24–48h) to allow community vetting.
- Runtime monitoring: Detect unexpected outbound requests from apps.
For Ecosystem & Vendors
- Registry anomaly detection: Auto-flag sudden updates to high-download packages.
- Automated rollback: Quickly revert suspicious package versions.
- Maintainer verification: Extra checks for maintainers of high-impact libraries.
- Transparent dependency signing: Verify package integrity through signatures.
- Rapid community alerting: Broadcast compromised package lists immediately.
This was the largest npm supply-chain compromise ever recorded — billions of downloads, 10% of cloud environments impacted in two hours.
The only reason it wasn’t catastrophic is because the attackers chose the wrong payload. They aimed at browser crypto theft, missing the fact that these packages power backend servers, CI/CD pipelines, and cloud workloads.
The incident is both a relief and a warning:
- Relief, because the damage was minimal.
- Warning, because the next attackers will learn from this mistake.
Supply chain attacks are not going away. If we don’t harden npm, GitHub, and open-source maintainer security, the next breach could be far more destructive.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










