Crooks in China have developed an Android ransomware that uses similar graphics to the WannaCry ransom note in an attempt to scare and trick users into quickly paying the ransom.
Spotted by Qihoo 360 researchers, crooks are spreading this ransomware via Chinese gaming forums. The malicious app containing the ransomware tries is disguised as a plugin for the King of Glory, a very popular mobile game in China.
Some people just wanna get arrested
By the looks of it, the ransomware is obviously the work of amateur ransomware operators who have a fetish for getting arrested.
Unlike 99.9% of today’s ransomware, this WannaCry lookalike for Android devices is asking users to pay the ransom fee of 40 Chinese Renminbi ($6) via Chinese payment providers QQ, Alipay, or WeChat.
Its authors have either not heard of Bitcoin before, or bumped their head and forgot they live in China, the country where authorities have the deeper access to data from technology firms.
It would take police minutes to track down who’s on the receiving end of all the ransom payments and crack down on its operators.
WannaCry lookalike uses solid encryption
Outside of the idiotic method of handling ransom payments, this WannaCry lookalike for Android is pretty solid code-wise.
For starters, the ransomware actually encrypts files, which is pretty impressive if we take into account that most Android ransomware is still at the screen-locker level.
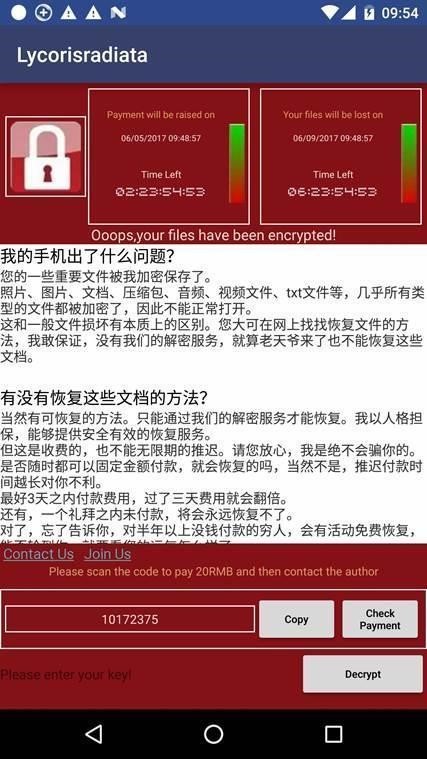
The ransomware uses AES encryption to lock files, and it will append a suffix to all encrypted files consisting of a mixture of Chinese and Latin characters.
Because resources are limited on Android devices, the ransomware will only encrypt files under 10KB in size. To avoid ruining and crashing the Android OS, the ransomware doesn’t encrypt files whose names start with a dot, or files located in folders that include ”android”, “com”, “DCIM”, “download”, or “miad” in their file path.
According to Nikolaos Chrysaidos, security researcher for Avast, this ransomware — which the company named WannaLocker — only encrypts files on the smartphone’s external storage.
Source: https://www.bleepingcomputer.com/news/security/android-smartphones-targeted-by-wannacry-lookalike/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










