Over 100 Snooping Tor Nodes Have Been Spying on Dark Web Sites
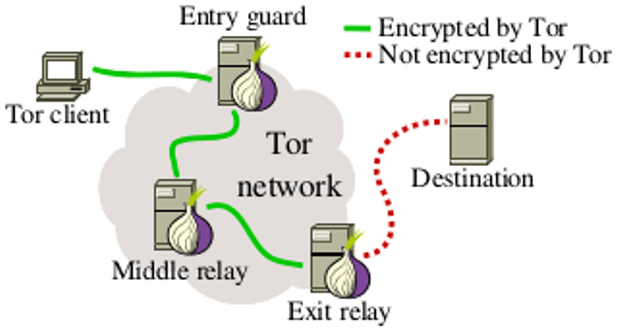
When it comes to accessing public websites, Tor has an intrinsic security problem: though the nodes between your computer and the public internet are unable to see where the trafficRead More →