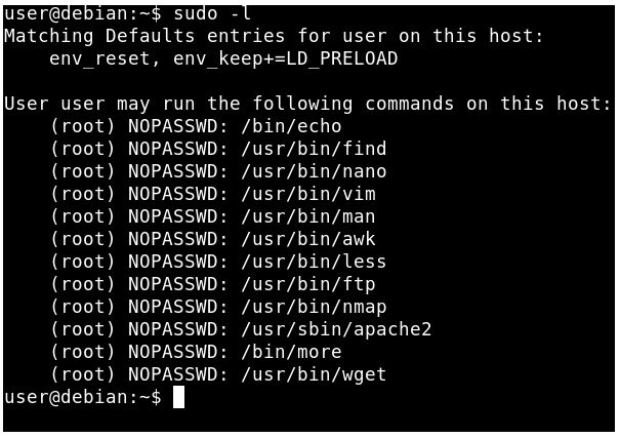
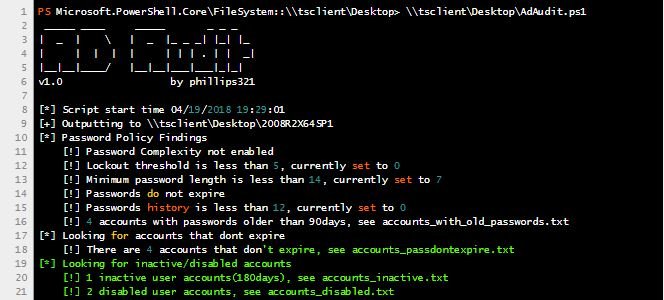
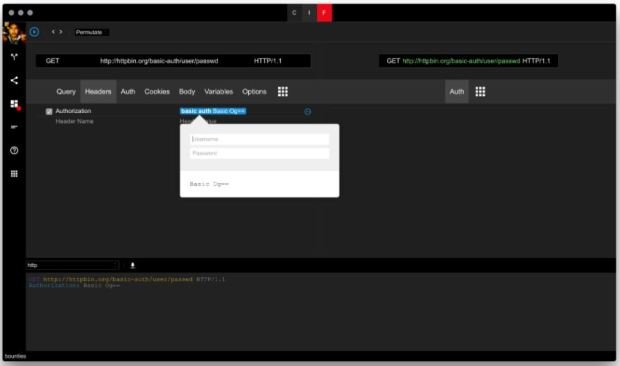
My Cloud EX2 device from Western Digital leaks files by default
According to research conducted by information security professionals at Trustwave, Western Digital’s My Cloud EX2 storage devices filter files to anyone in a local network by default, this is regardlessRead More →