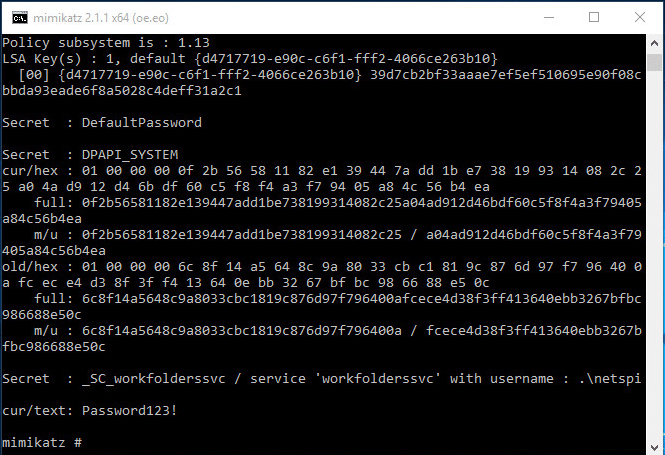
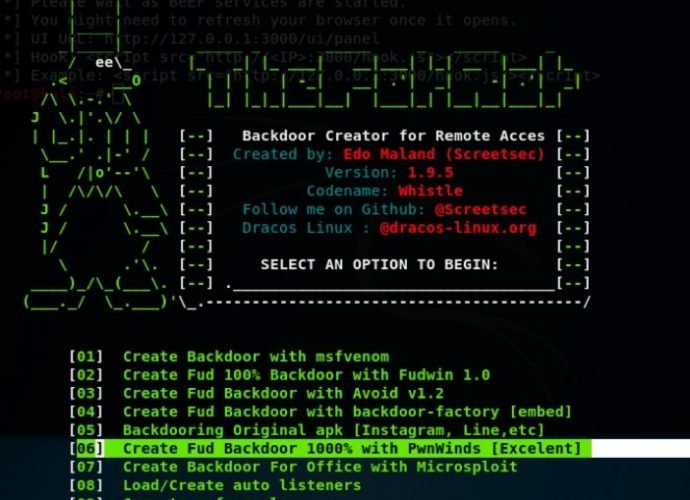
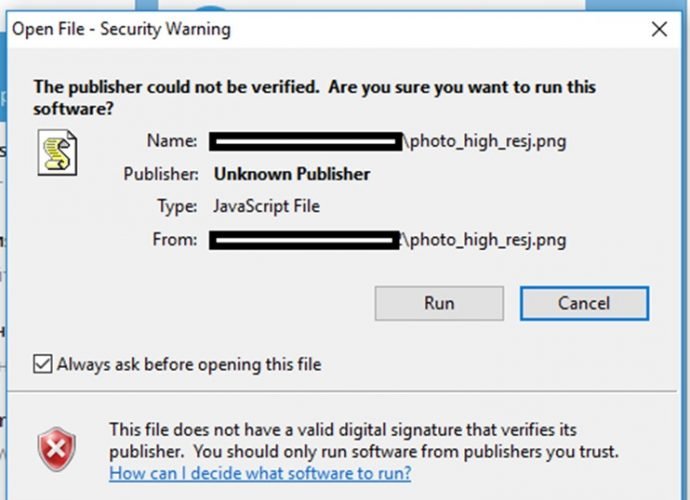
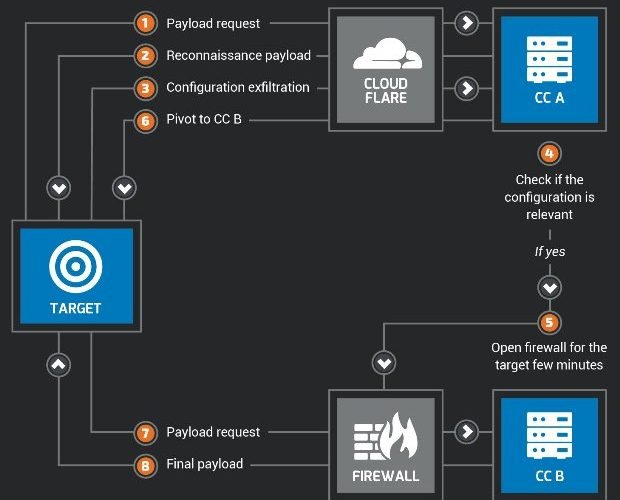
CrossRAT a Trojan built with Java that infects Windows, macOS, Linux and Solaris
Last week companies specialized in cyber security discovered the existence of a new Persistent Advanced Threat APT, supposedly sponsored by Dark Caracal, an organization dedicated to espionage. Since 2012, he has performedRead More →