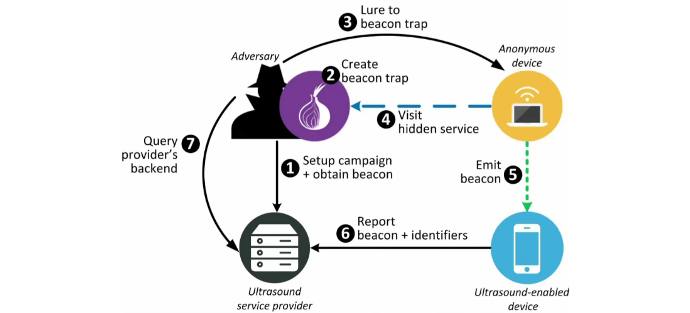
Ultrasound Tracking Could Be Used to Deanonymize Tor Users
Ultrasounds emitted by ads or JavaScript code hidden on a page accessed through the Tor Browser can deanonymize Tor users by making nearby phones or computers send identity beacons backRead More →