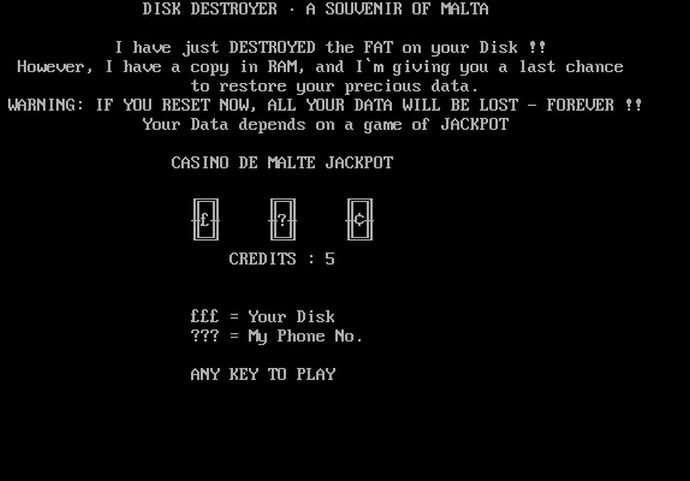
Ransomware for robots, the next security threat
Researchers found they were able to infect robots with ransomware; in the real world such attacks could be highly damaging to businesses if robotic security isn’t addressed. According to information securityRead More →