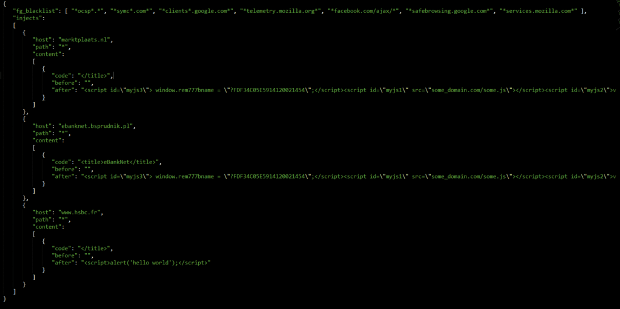
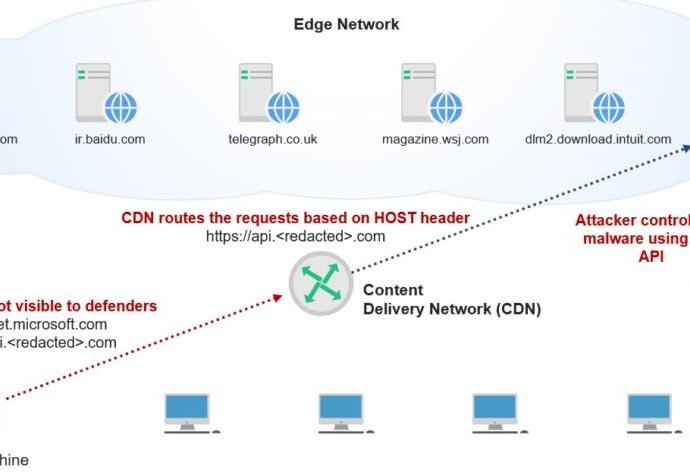
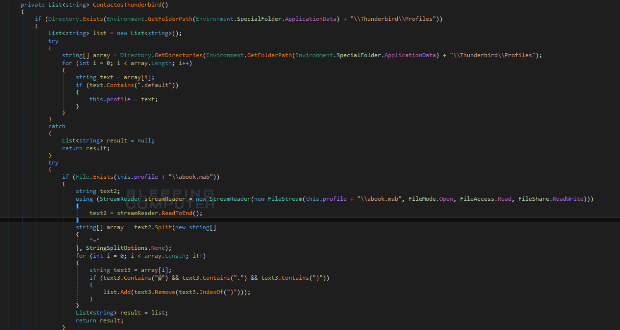
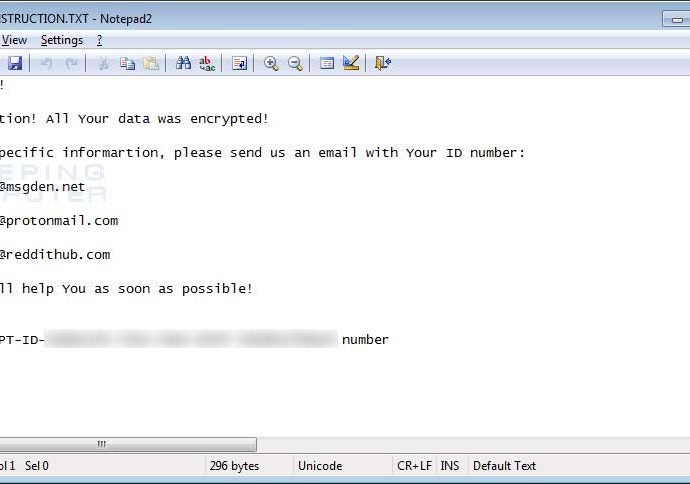
“Perverse” malware infecting hundreds of Macs remained undetected for years
Surveillance malware dubbed Firefly was easy to spot but flew under the radar anyway. A mysterious piece of malware that gives attackers surreptitious control over webcams, keyboards, and other sensitiveRead More →