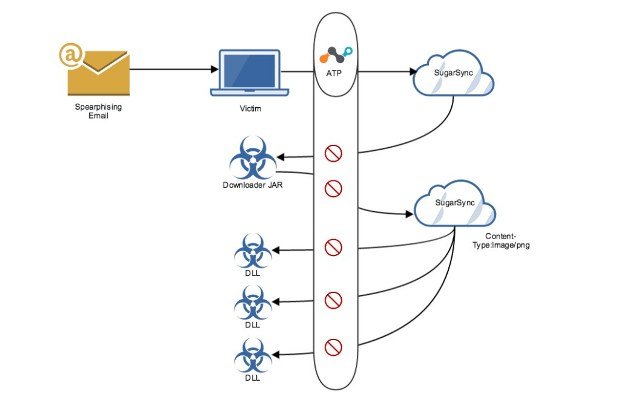
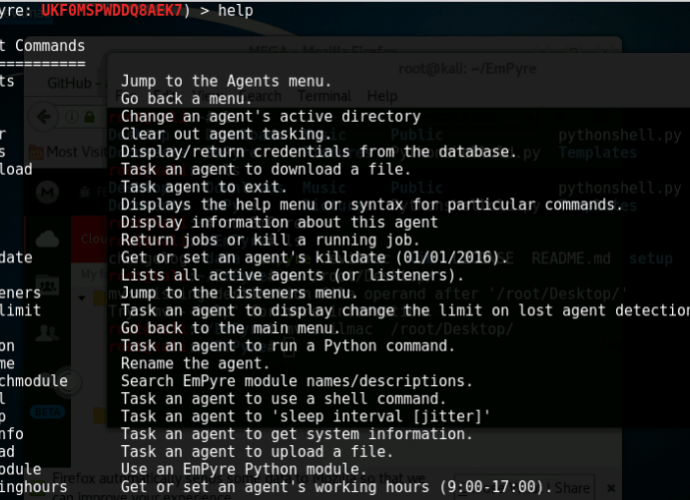
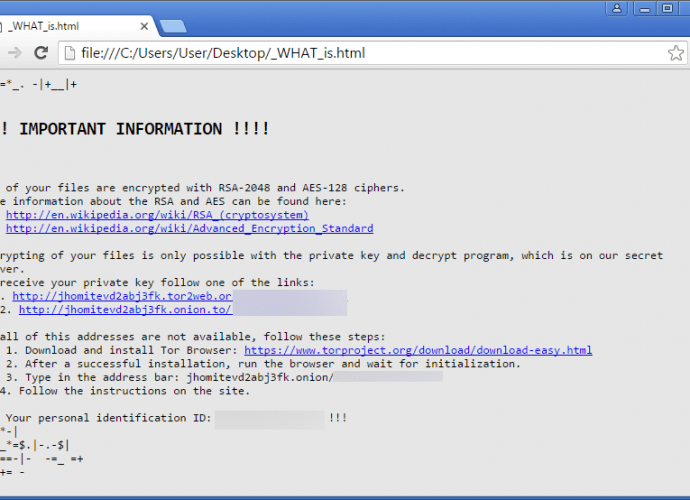
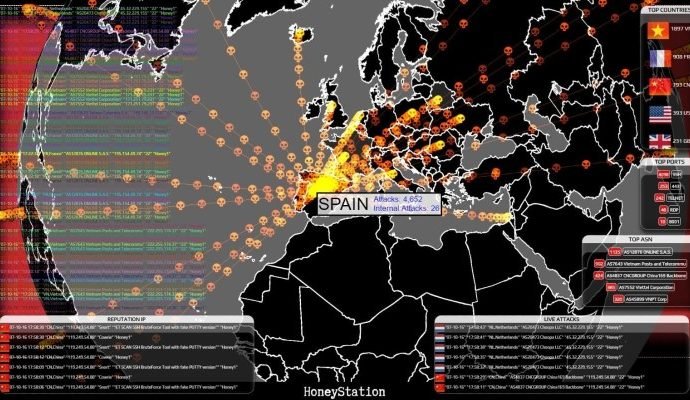
Wannabe Hackers Are Adding ‘Terrible’ and ‘Stupid’ Features to Mirai
In early October, a hacker named Anna-senpai published the source code of a malware created to automatically scour the internet for poorly secured and easy-to-hack connected devices that could beRead More →