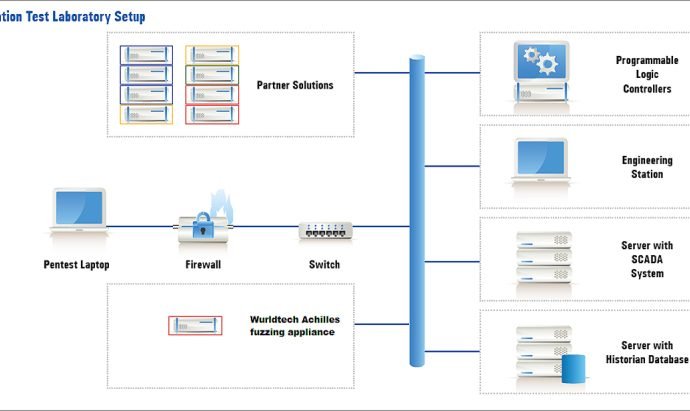
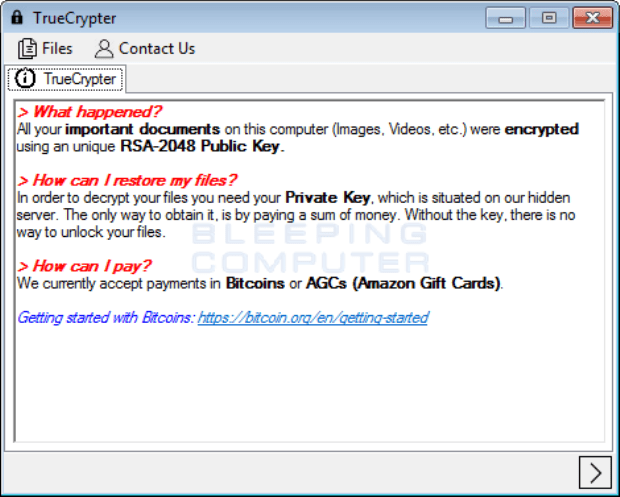
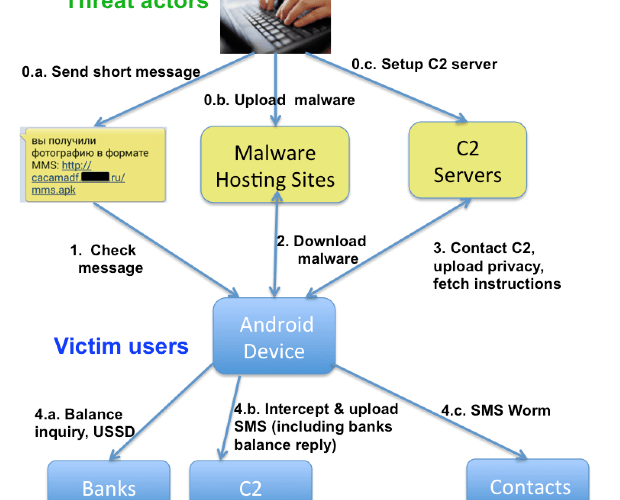
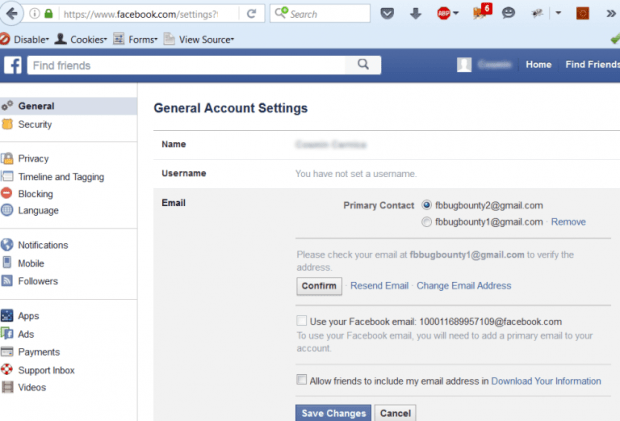
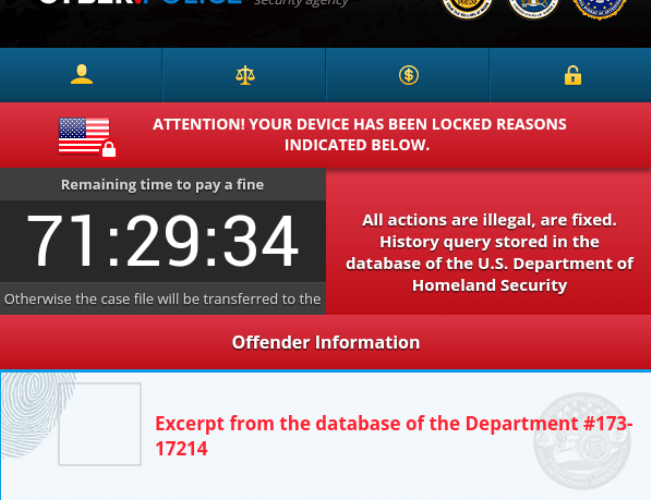
Ransomware Explosion Continues: CryptFlle2, BrLock and MM Locker Discovered
Ransomware makes headlines when hospitals are taken offline or police departments pay cybercriminals to decrypt their files. Established threat actors have also begun distributing ransomware in high volumes (as withRead More →