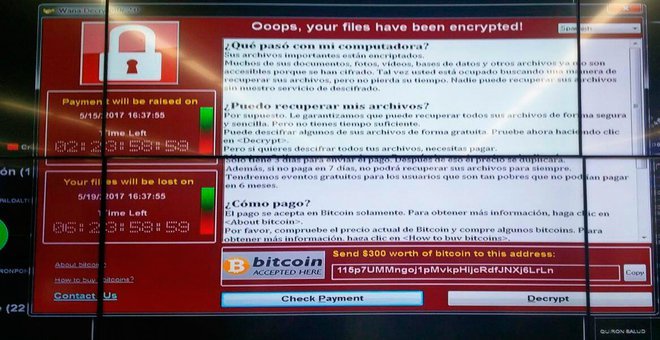
Honeypot Server Gets Infected with WannaCry Ransomware 6 Times in 90 Minutes
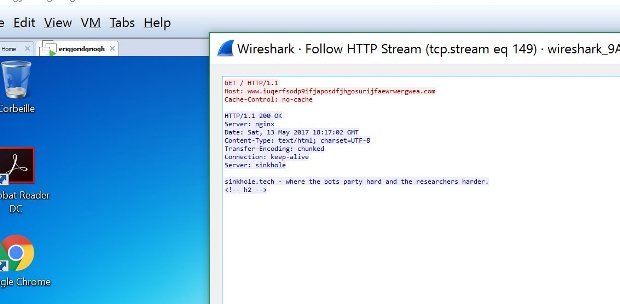
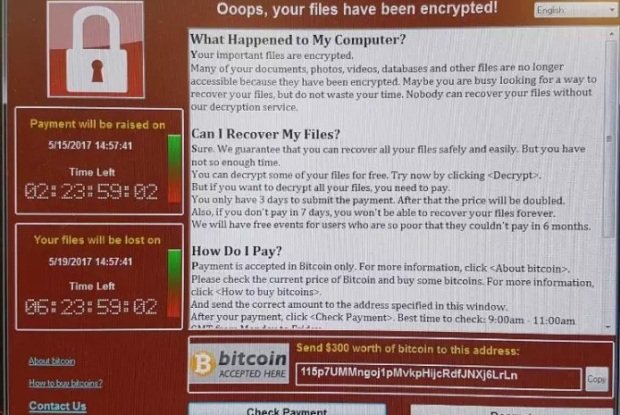
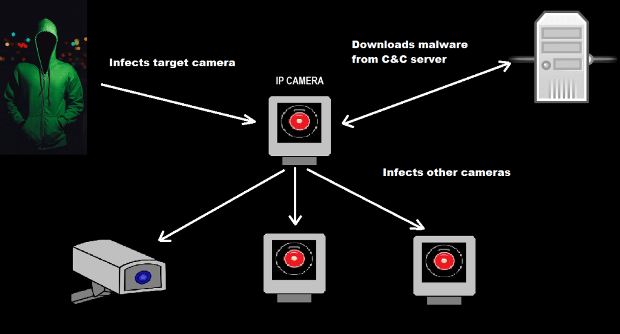
The WannaCry ransomware — also known as WCry, Wana Decrypt0r, WannaCrypt, and WanaCrypt0r — infected a honeypot server made to look like a vulnerable Windows computer six times in theRead More →