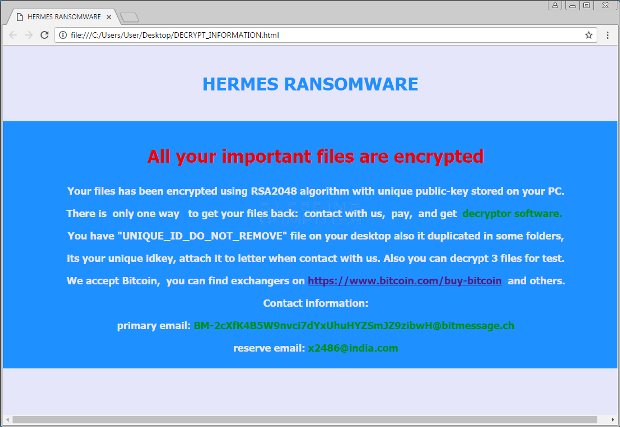
8 things you should know about spyware
Spyware is defined as a “generic term for a range of surreptitious malware such as keyloggers, remote access trojans, and backdoor trojans, especially those that allow remote surveillance of passwordsRead More →