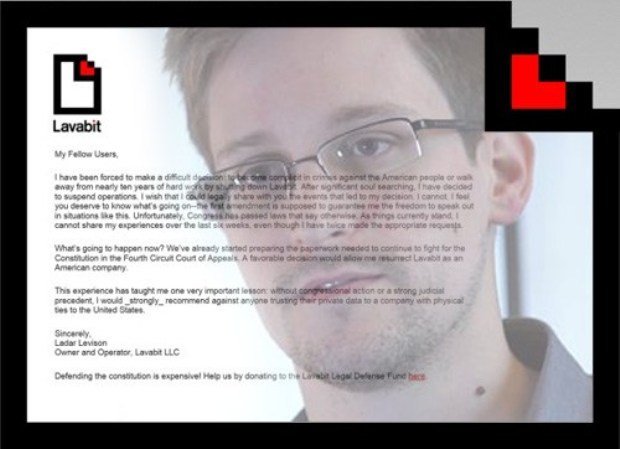
Lavabit, the Snowden recommended encrypted email service, is back
Lavabit, the Snowden recommended encrypted email service, is back. Its CEO Ladar Levison announced new privacy-enhancing features. Do you remember Lavabit? It was the US Encrypted Email Service used by theRead More →