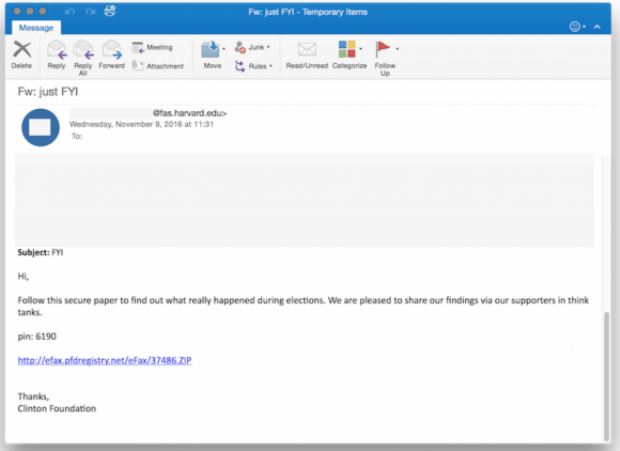
Locky ransomware campaign exploits fears of data stolen in OPM hack
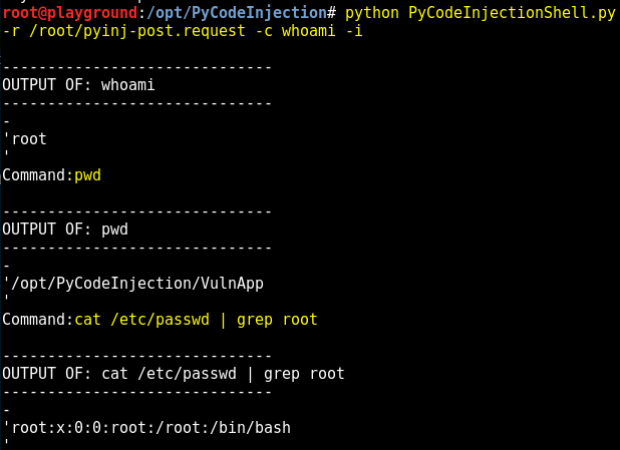
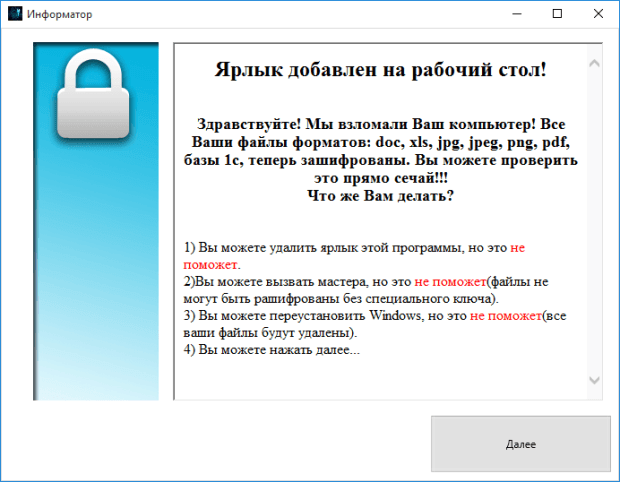
Emails tell victims they need to download an attachment to view “suspicious activity” – then infects them with ransomware. In the immediate aftermath of a major data breach, cybercriminals willRead More →