Unlock92 Ransomware Is the Quiet Threat That Nobody Heard About
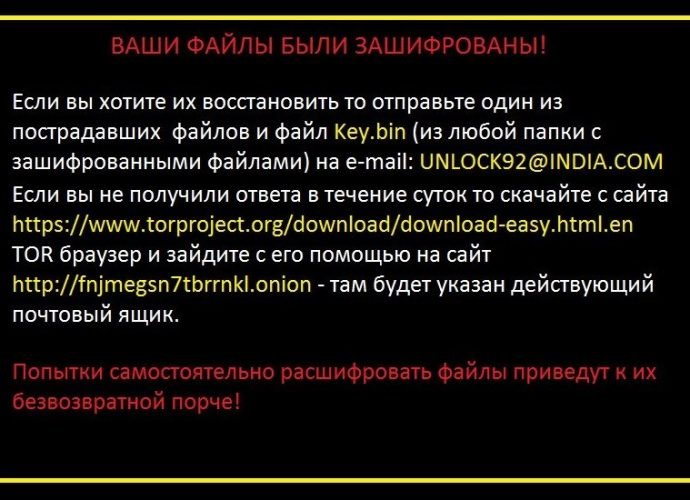
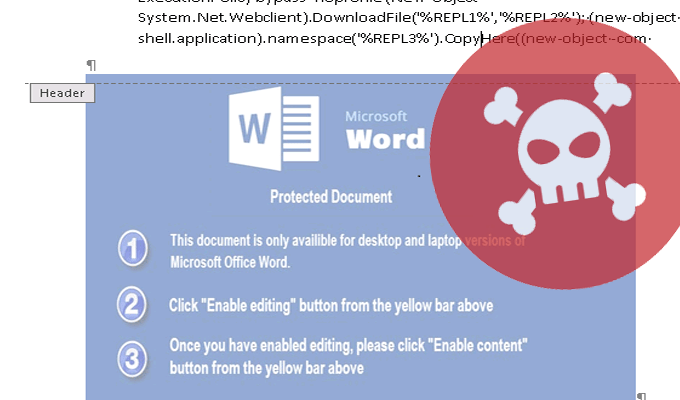
Unlock92 infections going under the radar. A ransomware variant that appeared in early July this year and was initially cracked and decrypted has quietly resurfaced in mid-August and has beenRead More →