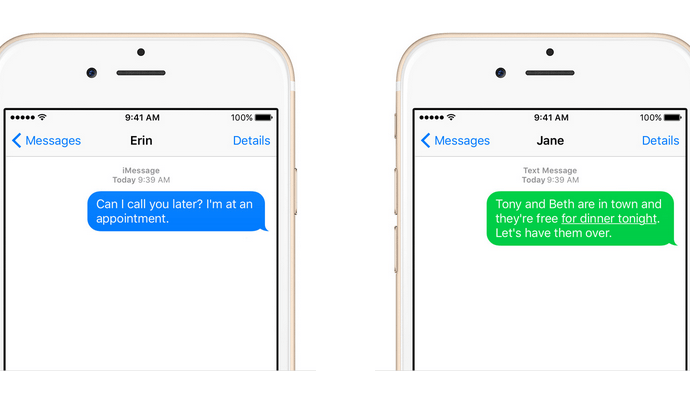
Cryptography Experts Say Apple Needs to Replace iMessage Encryption
iMessage receives several fixes following mammoth research. Apple has added a series of short- and long-term defenses to the iMessage protocol following the private disclosure of several issues discovered by aRead More →